Scanning Harbor registry images for vulnerabilities with Snyk
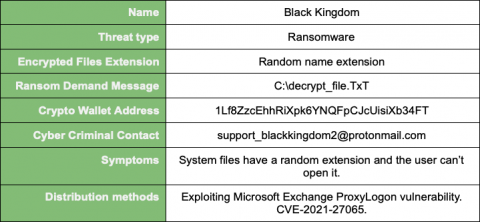
It’s official! Snyk Container offers support for scanning container images stored in the popular open source container registry, Harbor. Snyk Container helps you find and fix vulnerabilities in your container images, and now it integrates with Harbor as a container registry, enabling you to import your projects and monitor your containers for vulnerabilities. Snyk tests the projects you’ve imported for any known security vulnerabilities found, testing at a frequency you control.