Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
July 2023
Implementing TLS in Kubernetes
As cloud technology continues to evolve, the demand for Kubernetes is skyrocketing. As a result, security has become a top priority for developers looking to protect their application data. That's where Transport Layer Security (TLS) comes into play. TLS is essential for ensuring a secure connection between your applications and the internet. TLS leverages asymmetric and symmetric cryptographies to keep your data secure in transit and at rest.
Red team exercises against social engineering attacks
How can you take a proactive approach to your organization’s cybersecurity strategy? Scoping the threat landscape and having a solid incident response plan is a good start. But you also need to continuously seek out vulnerabilities and weaknesses to remediate or mitigate. These vulnerabilities and weaknesses aren’t just limited to systems and processes – the human factor plays a prominent part in many cybersecurity breaches.
RCE vulnerability CVE-2023-36884
How secure is WebAssembly? 5 security concerns unique to WebAssembly
WebAssembly, sometimes called Wasm, is a portable, low-level binary code instruction format executed in a web browser’s virtual machine (VM). It enables developers to write high-performance code in various languages and runs alongside JavaScript. Developers are embracing WebAssembly for its ability to accelerate complex algorithms, enable gaming and multimedia applications, and provide a secure sandbox environment for running untrusted code.
OWASP ASVS with your security testing tools
OWASP ASVS is a great project to provide a framework of security controls for design and define the basis of secure development. But the problem is when you decide to use these checks in your organization, you end up with a 71-page pdf file or an OWASP ASVS checklist (excel sheet). It is incredibly hard for organizations to adapt and spread the word within the company. This is why we decided to implement a feature that gets all the security testing tools results (by CWE) and maps them into OWASP ASVS automatically so you can use it in every aspect of your application security program.
NIS2 Directive and cyber risk management
The NIS2 Directive, published in December 2022, sets out a series of measures for improving cyber risk management throughout the European Union. All EU member states must apply the Directive as part of national law by October 2024. By the same date, all applicable organizations must comply with the measures set out in NIS2.
Using Mitre Att&CK with threat intelligence to improve Vulnerability Management
MITRE ATT&CK® is a globally accessible knowledge base of 14 adversary tactics and over 500 techniques based on real-world observations. The first model was proposed in 2013 and publicly released in 2015 which has been gathering momentum over the last couple of years.
Control your role! Kubernetes RBAC explored
Role-based access control (RBAC) is an approach for controlling which actions and resources in a system are available to different users. Users are assigned roles that grant them permission to use particular system features. Kubernetes has a robust built-in RBAC implementation for authorizing user interactions with your cluster. Setting up RBAC allows you to define the specific actions that users can perform on each Kubernetes object type.
Office Hours: Best Practices for Securing your Applications with Snyk in Jenkins
Secure Code Review Best Practices [cheat sheet included]
Reducing vulnerabilities in your software means manual and automated secure code reviews. Download our handy cheat sheet to keep your review practice on track.
Snyk's 2023 State of Open Source Security: Supply chain security, AI, and more
The 2021 Log4Shell incident cast a bright light on open source software security — and especially on supply chain security. The 18 months following the incident brought a greater focus on open source software security than at any time in history. Organizations like the OpenSSF, AlphaOmega, and large technology companies are putting considerable resources towards tooling and education. But is open source software security actually improving? And where are efforts still falling short?
CVE-2023-35078: Remote Authentication Bypass Vulnerability in Ivanti Endpoint Manager Mobile
Common Types of Network Vulnerabilities for Businesses
ModSecurity v3: DoS Vulnerability in Four Transformations (CVE-2023-38285)
ModSecurity is an open-source Web Application Firewall (WAF) engine maintained by Trustwave. This blog post discusses an issue with four transformation actions that could enable a Denial of Service (DoS) attack by a malicious actor. The issue has been addressed with fixes in v3.0.10. ModSecurity v2 is not affected.
Open-source: The New Way of Envisioning Security
The Secret's Out: Researchers Reveal Backdoor in Emergency Radio Encryption
For over 25 years, a technology utilized for vital data and voice radio communications globally has remained under wraps, preventing in-depth testing for potential vulnerabilities. However, a small group of researchers in the Netherlands has now shed light on it, uncovering significant flaws, including a deliberate backdoor.
How Cloudflare is staying ahead of the AMD vulnerability known as "Zenbleed"
A new flaw in AMD's Zen 2 processors is detailed in this blog post (archive.org snapshot) today, July 24, 2023. The 'Zenbleed' flaw affects the entire Zen 2 product stack, from AMD's EPYC data center processors to the Ryzen 3000 CPUs, and can be exploited to steal sensitive data stored in the CPU, including encryption keys and login credentials.
ISO 27002 puts Threat Intelligence center stage
The ISO 27000 series is an industry standard that has long defined and dictated base-level requirements for organizations’ information security management systems (ISMS). Through more than a dozen standards, the framework helps organizations demonstrate management commitment to their ISMS as they regularly review and improve their systems and procedures.
Product demo - O24 Farsight VPT for Risk-based Vulnerability Management
MOVEit Vulnerability Investigations Uncover Additional Exfiltration Method
Kroll has identified two different file exfiltration methodologies leveraged by threat actors, primarily CLOP, during recent engagements involving the exploitation of the MOVEit vulnerability (CVE-2023-34362) throughout May and June 2023. In the vast majority of Kroll’s global MOVEit investigations, the primary data exfiltration method consisted of utilizing the dropped web shell to inject a session or create a malicious account (named Method 1 for this piece).
New TETRA:BURST Vulnerabilities Enable Attackers to Intercept and Inject Critical Radio Traffic - How to Mitigate Risk
What are Vulnerability Disclosure Programs?
Mitigating the Latest Microsoft Teams Vulnerability with Netskope
Recently, a team of experts from JumpSEC Labs discovered a vulnerability in Microsoft Teams that allows malicious actors to bypass policy controls and introduce malware through external communication channels. Leaving end-users susceptible to phishing attacks. Microsoft’s advice is to educate end-users to detect phishing attempts. One workaround would be to disable Microsoft Teams collaboration with external organizations.
Electrifying Exploit: A Case Study on SSRF Vulnerability in an EV Manufacturer's System
The Rise of CI0p Ransomware with MOVEit Transfer Vulnerabilities
GuidePoint Security Breached in MOVEit Data Attacks: Customers Get Exposed
GuidePoint Security is a software company that specializes in security services. The organization is located in Herndon, Virginia, employs 722 people, and protects and manages data for thousands of people during its daily operations. This company was compromised in the MOVEit data breaches, putting a large number of people at risk.
Adobe ColdFusion Vulnerabilities Exploited in the Wild
New research reveals rapid remediation of MOVEit Transfer vulnerabilities
8 tips for securing your CI/CD pipeline with Snyk
Securing your CI/CD pipeline is critical to modern application security. So, we created a cheat sheet to make the process easier. In this post, we’ll cover using Snyk in your CI/CD pipelines to catch security issues quickly and empower your developers to fix them before they get to production.
Addressing the npm Manifest Confusion Vulnerability
A potential security risk in the npm ecosystem known as “manifest confusion” has recently been spotlighted in a blog post by Darcy Clarke, a former Staff Engineering Manager at GitHub. Clarke mentioned that JFrog Artifactory seems to replicate this issue, so of course we investigated it right away. In this post, we will explain what the issue is and what it might mean for JFrog Artifactory users.
Netskope Threat Coverage: Microsoft Office and Windows Zero Day (CVE-2023-36884)
Microsoft disclosed a zero-day vulnerability impacting Office and Windows on July’s Patch Tuesday. This vulnerability has an “important” severity level, and can allow attackers to perform remote code execution with the same privileges as the target. As of this writing, there is no patch available to mitigate the vulnerability, but Microsoft has provided mitigation steps.
Why is Software Vulnerability Patching Crucial for Your Software and Application Security?
Software vulnerability patching plays a critical role in safeguarding your code base, software, applications, computer systems, and networks against potential threats, and ensuring they’re compliant, and optimized for efficiency. Organizations’ codebases have become increasingly complex, involving sophisticated relationships between components and their dependencies.
Penetration Tests vs. Vulnerability Scans: What's the Difference?
Compliance with regulatory requirements works best when you understand the terms of art used in compliance and cybersecurity, such as the difference between penetration tests and vulnerability scans. You can perform many types of tests to assess the state of your data security, vulnerability scans and penetration tests being among the most important — but they are not the same thing, and they serve different purposes.
Best practices for using AI in the SDLC
AI has become a hot topic thanks to the recent headlines around the large language model (LLM) AI with a simple interface — ChatGPT. Since then, the AI field has been vibrant, with several major actors racing to provide ever-bigger, better, and more versatile models. Players like Microsoft, NVidia, Google, Meta, and open source projects have all published a list of new models. In fact, a leaked Google document makes it seem that these models will be ubiquitous and available to everyone soon.
Finding and fixing insecure direct object references in Python
An insecure direct object reference (IDOR) is a security vulnerability that occurs when a system’s implementation allows attackers to directly access and manipulate sensitive objects or resources without authorization checks. For example, an IDOR can arise when an application provides direct access to objects based on user-supplied input, allowing an attacker to bypass authorization.
CVE-2023-3519: Critical Unauthenticated RCE Vulnerability in Citrix ADC and Citrix Gateway
Does PCI DSS v4.0 Require a Pen Test?
PCI version 4.0 was released in March 2022, and all organizations that must be compliant with the regulation have a deadline of March 31, 2024 to do so. So, what does the new version say about pen testing? According to Requirement 11 of the Payment Card Industry Data Security Standard (PCI DSS), pen testing is required for organizations and entities that store, process, and/or transmit cardholder data.
Best practices for effective attack surface analysis
An application’s attack surface is the sum of points where it might be vulnerable to bad actors. It consists of all the paths in and out of the application. Identifying vulnerabilities is vital to mitigating threats because any access point is a potential entry point for an attack. An attack surface analysis, which is critical to this mitigation strategy, is the process of identifying and assessing the potential vulnerabilities and risks in a software system or network.
Swift deserialization security primer
Deserialization is the process of converting data from a serialized format, such as JSON or binary, back into its original form. Swift provides multiple protocols allowing users to convert objects and values to and from property lists, JSON, and other flat binary representations. Deserialization can also introduce unsuspecting security vulnerabilities in a user’s codebase that attackers could exploit.
ThreatQ Cyber Forum Recap: Expert Insights on Risk-Based Vulnerability Management
The discipline of vulnerability management has been around for decades and the way we assess risk, based on severity and likelihood of exploitation, has remained fairly constant. However, there are challenges in how this formula is usually applied that narrow our perspective on risk and our mitigation strategies.
How to Respond: CVE-2023-27997 (Fortigate SSL VPN)
The New Era of AI-Powered Application Security. Part Two: AI Security Vulnerability and Risk
AI-related security risk manifests itself in more than one way. It can, for example, result from the usage of an AI-powered security solution that is based on an AI model that is either lacking in some way, or was deliberately compromised by a malicious actor. It can also result from usage of AI technology by a malicious actor to facilitate creation and exploitation of vulnerabilities.
XS leaks: What they are and how to avoid them
Cross-site leaks (XS leaks) are a class of web security vulnerabilities that allow hackers to obtain sensitive information from a user’s browsing session on other websites or web apps. Modern web applications share data through various features and APIs — a function attackers can exploit to access this user data.
Four Critical SonicWall Vulnerabilities Patched
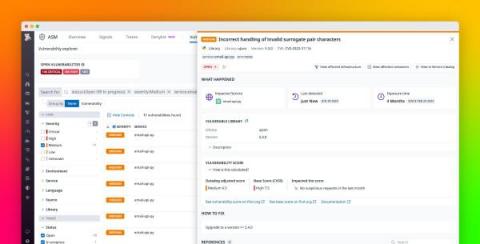
Introduction to Insights by Snyk
The 443 Podcast - Episode 250 - New Microsoft Office 0-Day
Analysis of CVE-2023-2868 Exploitation: Campaign Targeting U.S. Entities Using Barracuda Email Security Gateway
CVE-2023-2868, a vulnerability in the Barracuda ESG was announced on May 23. On June 15th, a report surfaced, attributing the exploitation of this vulnerability to a threat actor group tracked as UNC4841, which analysts believe is conducting espionage on behalf of the Chinese government. SecurityScorecard’s STRIKE Team consulted its datasets to identify possibly affected organizations.
Top 5 security concerns for infrastructure as code
Infrastructure as code (IaC) has changed how we deploy and manage our cloud infrastructure. Instead of having to manually configure servers and networks with a large operations team, we can now define our service architecture through code. IaC allows us to automate infrastructure deployment, scale our entire fleet of servers, document a history of changes to our architecture, and test incremental changes to the network.
Adversaries Can "Log In with Microsoft" through the nOAuth Azure Active Directory Vulnerability
On June 20, 2023, Descope published research detailing how a combination of a flaw in Azure Active Directory and poorly integrated third-party applications — dubbed “nOAuth” — could lead to full account takeover. nOAuth is the latest in a large number of vulnerabilities and architectural weaknesses in Microsoft software and systems like Active Directory that can be exploited and put organizations at risk.
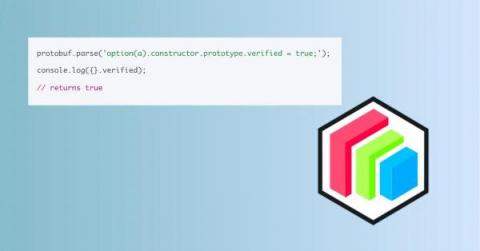
Code Intelligence Finds New Vulnerability in protobufjs: CVE-2023-36665
CVE-2023-33308: Critical Fortinet FortiOS and FortiProxy RCE Vulnerability
The Value of Vulnerability Management
There’s nothing that makes you feel older than realizing how much of your life you have dedicated to a single topic. At what point do you consider yourself an expert? After more than 17 years in vulnerability management, I’m starting to come around to the idea that I might be an expert in the field. Although, the main reason I feel that way is because, at this point, I’ve seen pretty much everything.
How to Deal with Hundreds of Fixes? Choosing the Right Vulnerability Management Solution
Relying solely on the Common Vulnerability Scoring System (CVSS) is insufficient when it comes to effective vulnerability management. While the CVSS score provides a quantitative measure of a vulnerability’s severity, it fails to capture the contextual nuances that can significantly impact the actual risk to an organization. In this article, we will discuss how best to choose a vulnerability management solution.
How to strengthen security in your CI/CD pipeline
DevSecOps refers to the integration of security practices into DevOps process. With modern development cycles, you can't afford to leave security until the end. It should be baked in at every stage. Continuous integration, continuous delivery (CI/CD) security is a big part of the DevSecOps picture. It's critical that you secure your pipelines and that the automated systems used to implement CI/CD are not vulnerable to attack.
Enhance SBOMs with runtime security context using Datadog Application Vulnerability Management
Software today relies heavily on open source, third-party components, but these reusable dependencies sometimes inadvertently introduce security vulnerabilities into the code of developers who use them. Some of the most serious vulnerabilities discovered in recent years—like the OpenSSL punycode vulnerability, Log4Shell (Log4j), and Dirty Pipe (Linux)—reside in popular open source packages, making them so widespread that they could compromise almost the entire software ecosystem.
Proof of Concept Developed for Ghostscript CVE-2023-36664 Code Execution Vulnerability
Ghostscript, an open-source interpreter for the PostScript language and PDF files, recently disclosed a vulnerability prior to the 10.01.2 version. This vulnerability CVE-2023-36664 was assigned a CVSS score of 9.8 that could allow for code execution caused by Ghostscript mishandling permission validation for pipe devices (with the %pipe% or the | pipe character prefix). Debian released a security advisory mentioning possible execution of arbitrary commands.
Cyberattack Spotlight: The Zero-Day Exploit
Session management security: Best practices for protecting user sessions
Session management security is an essential component of web application development. It safeguards user sessions and prevents unauthorized access. Managing sessions secures the confidentiality, integrity, and availability of sensitive user data. It also protects user privacy at large — which is essential to maintaining user trust in an application. When we manage sessions securely, we establish processes to destroy session tokens when users log out or their session ends.
How to Decide Whether Vulnerability Remediation Augmented by Generative AI Reduces or Incurs Risk
Software security vendors are applying Generative AI to systems that suggest or apply remediations for software vulnerabilities. This tech is giving security teams the first realistic options for managing security debt at scale while showing developers the future they were promised; where work is targeted at creating user value instead of looping back to old code that generates new work.
What is Juice Jacking?
Juice jacking is a security exploit in which devices are compromised when plugged into an infected USB charging station, port or use an infected charging cable. This type of security exploit takes advantage of the fact that many people need to charge their devices, especially when traveling, and use the provided USB cables to do so. Apart from charging devices, USB cables are also used to sync data which is how attackers are able to take advantage and extract data from devices.
How Cloudflare Images addressed the aCropalypse vulnerability
Acropalypse (CVE-2023-21036) is a vulnerability caused by image editing tools failing to truncate images when editing has made them smaller, most often seen when images are cropped. This leaves remnants of the cropped contents written in the file after the image has finished. The remnants (written in a ‘trailer’ after the end-of-image marker) are ignored by most software when reading the image, but can be used to partially reconstruct the original image by an attacker.
Ghostscript Vulnerability (CVE-2023-36664) Proof of Concept
CVE-2022-31199: Truebot Malware Campaign Actively Exploiting Netwrix Auditor RCE Vulnerability
CVE-2023-36934: New Authentication Bypass Vulnerability Identified in MOVEit Transfer
Guidance on the Critical MOVEit Transfer Vulnerability (CVE-2023-34362)
CVE-2023-26258: Unauthenticated RCE Vulnerability in Arcserve Unified Data Protection
New Vulnerability in protobuf.js: Prototype Pollution - CVE-2023-36665
What the Financial Sector Needs Now: Risk-Based Vulnerability Management
According to the Verizon 2023 Data Breach Investigations Report, basic web application attacks, which consist largely of leveraging vulnerabilities and stolen credentials to get access to an organization’s assets, are the most prevalent pattern of attack against the financial services sector.
What is Vulnerability Testing? Benefits, Tools, and Process
Jackson National Life Insurance is Another Major Company Hit by MOVEit Data Breaches
Jackson National Life Insurance is based in Lansing, Michigan, and was founded in 1961. This insurance and annuities company offers retail brokerage services and offers asset management services to its customers. Nearly 3,000 people are employed by the company, and it has an annual revenue of $14.4 billion. This large-scale insurance company is just one of the many recent organizations to be hurt by the MOVEit file transfer service breaches.
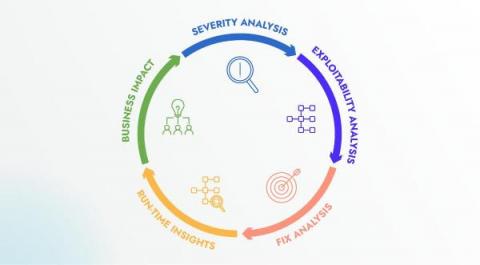
Bugged by vulnerabilities? This is what you need
Twenty-five percent: Any idea what this percentage is referring to? Let’s take some wild guesses: A five-year CAGR of your investments? Your yearly salary hike? If any of your guesses were remotely close to these happy responses, we’re sorry to break your heart! This percentage depicts the rise in the number of identified vulnerabilities in 2022 over the previous year. 2022 saw an alarming spike of 25% in identified vulnerabilities, the count rising to 25,227 from 20,171 previously.