What is SDLC? Why Should You Opt for Secure SDLC Instead?
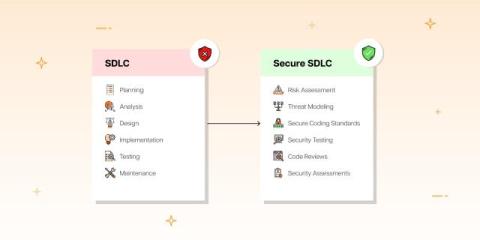
The Software Development Life Cycle (SDLC) provides a systematic framework for developing and maintaining software from conception to modification, producing high-quality software that meets stakeholder and customer requirements within specified time and cost constraints. However, traditional SDLC practices fall short of ensuring thorough application security. Why?