|
By Natalia Kazankova
C and C++ programming are notorious for being bug-prone. Let’s look at the most dangerous software weaknesses in 2024 that are relevant for C and C++, so that you know what type of issues to test your code against in 2025. We examined the 2024 CWE Top 25 Most Dangerous Software Weaknesses list developed by Common Weakness Enumeration (CWE) and identified weaknesses relevant to C/C++. These weaknesses can become vulnerabilities. We explained how they occur and how you can uncover them.
|
By Natalia Kazankova
In 2025, fuzz testing has become an essential practice for ensuring software security and reliability. By identifying vulnerabilities through randomized input testing, fuzzing helps development teams uncover bugs that traditional testing methods—such as static analysis and penetration testing—often miss. With rapid advancements in security tools, let’s explore the top fuzz testing tools of 2025, their key features, benefits, and how they compare.
|
By Natalia Kazankova
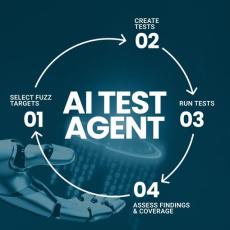
We’re thrilled to announce the general availability of Spark, an AI Test Agent that lowers the entry barrier to white-box fuzz testing. In this blog, we explain how Spark works and share the main results from its beta testing that prove its effectiveness.
|
By Natalia Kazankova
At the 6th de:hub Pitch Night, an event celebrating innovation and digital transformation, Code Intelligence was honored with the prestigious German AI Award. This recognition, awarded by a distinguished jury of industry experts and investors, underscores Code Intelligence’s pivotal role in advancing software security through artificial intelligence.
|
By Natalia Kazankova
Fuzz testing is most commonly classified based on its analysis approach. The two main categories of fuzz testing solutions are white-box and black-box fuzzers. In this blog, we explain the difference between approaches as well as their main features.
|
By Code Intelligence
Spark Uncovers Vulnerability in WolfSSL During Beta Testing.
|
By Peter Samarin
We are super excited to announce the discovery of a heap-based use-after-free vulnerability in wolfSSL, identified through a fuzz test automatically generated by an AI Test Agent. This marks another milestone in advancing automated security testing and demonstrates the power of AI-driven tools to improve software reliability and safety.
|
By Natalia Kazankova
White-box fuzz testing has proven highly effective in finding critical bugs and vulnerabilities. Tech giants like Google and Microsoft uncover thousands of issues using this method. But why doesn’t every company adopt fuzz testing as part of their testing strategy? The main barrier is the high level of manual effort and the extensive time required to properly set it up and maintain it.
|
By Natalia Kazankova
The market of embedded computing has been growing constantly, and this trend is expected to continue in the near future. Notably, embedded systems are key components for the Internet of Things (IoT) and for Cyber Physical Systems (CPSs). In the embedded software industry, secure software development is critical. This is especially true because embedded software often involves vital industries, such as medical devices or automotive solutions.
|
By Sergej Dechand
We are beyond excited to share some fantastic news with our community: Jazzer is now fully open source again under the Apache 2.0 license!
|
By Code Intelligence
A few weeks ago, we introduced Spark, an AI Test Agent that autonomously uncovers bugs in unknown code with just a single command. Watch the video to see how Spark generated 3 successful fuzz tests, identified a severe vulnerability, and achieved 79% code coverage with just one command. Spark has already identified several real-world vulnerabilities in open-source projects, even those that are continuously fuzzed.
|
By Code Intelligence
Testing Classic AUTOSAR applications has long been a significant challenge due to the reliance on hardware-in-the-loop (HiL) setups, which are costly, complex, and hard to scale. In this free webinar, Khaled Yakdan explains how a Tier-1 automotive supplier implemented Code Intelligence’s AUTOSAR simulator and enabled Software-in-the-Loop testing. Dr. Khaled Yakdan, Chief Product Officer, of Code Intelligence, also explains how this approach helps catch more critical bugs that can be accessed externally, speeds up security testing, and reduces hardware dependency.
|
By Code Intelligence
In previous videos, you've seen that LLM can generate fuzz tests. But what if AI fails to produce a working test or to cover specific workflows that are unavailable as unit tests or usage examples in the code base? You can prompt AI to make changes. Here is how the "Interactive mode" works in CI Fuzz.
|
By Code Intelligence
After generating fuzz tests with LLMs, the next important step is verifying that these tests are of high quality and ensuring they run and work as intended. CI Fuzz can now automatically build the generated fuzz test, run it, and perform a health check to assess its quality and refine it further if it doesn't pass the health check. Watch the video to see it in action.
|
By Code Intelligence
Creating high-quality fuzz tests is essential for efficient fuzz testing. However, crafting these tests is a time-consuming, manual process, which has become a major barrier to the widespread adoption of fuzz testing. Watch the video to see how CI Fuzz can automatically generate high-quality fuzz tests by leveraging LLMs and static analysis.
|
By Code Intelligence
The first step to start fuzzing is to identify what part of the software you want to fuzz. You definitely want to fuzz the most critical functions/APIs—those that exercise a significant amount of code and trigger key functionalities. However, manually identifying these targets can be time-consuming and challenging. Watch the video to see how CI Fuzz can automatically prioritize functions for fuzzing.
|
By Code Intelligence
If you want to automate your code analysis to identify the best fuzzing targets, you can do so with CI Fuzz. In the previous video, Khaled demonstrated how CI Fuzz automatically prioritized functions to test. But what if you already have unit or fuzz tests? CI Fuzz can analyze an LCOV coverage report and identify less-covered functions. These functions will now receive higher scores, highlighting them as top targets for new tests.
|
By Code Intelligence
About this webinar: Join the webinar to learn and see an in-depth live demo on how you can leverage fuzz testing to detect out-of-bound memory access bugs and similar vulnerabilities in C and C++ projects.
|
By Code Intelligence
The Crowdstrike incident is a recent example of out-of-bounds memory access in C/C++ causing a crash. CrowdStrike reported that problematic content in Channel File 291 triggered an out-of-bounds memory read, leading to a Windows operating system crash (BSOD). Another critical example with the exact root cause is the Heartbleed vulnerability, which affected the OpenSSL library. Remarkably, fuzz testing could identify this issue in less than 10 seconds. Watch the video to see fuzz testing in action.
|
By Code Intelligence
Sergej Dechand, Code Intelligence's CEO, demonstrates how developers can submit new code, which is automatically tested and analyzed for security issues. Sergej explains the process of running tests, assessing findings, and integrating with ticketing systems. You'll also see how to measure code coverage and download reports. It includes all the mentioned use cases with simulating hardware and autogenerated fuzz test setup..
- February 2025 (2)
- January 2025 (6)
- December 2024 (5)
- November 2024 (4)
- October 2024 (3)
- September 2024 (3)
- August 2024 (4)
- July 2024 (2)
- June 2024 (1)
- May 2024 (4)
- April 2024 (4)
- March 2024 (3)
- February 2024 (1)
- January 2024 (2)
- December 2023 (1)
- October 2023 (2)
- September 2023 (3)
- August 2023 (4)
- July 2023 (3)
- June 2023 (1)
- May 2023 (2)
- April 2023 (8)
- March 2023 (10)
- February 2023 (8)
- January 2023 (6)
- December 2022 (11)
- November 2022 (14)
- October 2022 (13)
- September 2022 (10)
- August 2022 (2)
- June 2022 (2)
- May 2022 (1)
- April 2022 (1)
- February 2022 (2)
- January 2022 (2)
- December 2021 (9)
Code Intelligence leverages the best of static and dynamic application security technologies, including advanced fuzz testing, to achieve maximum code coverage without false-positives.
Code Intelligence enables companies to simplify their software testing processes. Our solution - the CI Security Suite - enhances security testing efficiency for experts and enables developers without IT security expertise to perform continuous automated security and reliability tests. In this way, the development process can be accelerated and continuous quality management can be realized.
Secure Your Code With Each Pull Request:
- Choose Your Tech Stack: Code Intelligence can be integrated into all your favorite build systems, IDEs, ticket systems, issue trackers, and CI/CD tools.
- Set Up Fuzz Tests in Minutes: Through automated instrumentation and endpoint detection, Code intelligence makes fuzzing as simple as writing Unit Tests. No need to write fuzz targets or test harnesses.
- Scan Applications Continuously: Our platform features runtime error detection, advanced REST and gRPC API tests, and reliable OWASP vulnerability detectors. You can configure Code Intelligence to run security tests every night, or at each pull request.
- Reproduce Your Findings: Our easy-to-use GitHub integration and debugging features enable you to reproduce all findings without false-positives. Each error message comes with detailed input data, stack trace, and log documentation which can be easily shared with the team.
- Prioritize Security Issues: Our user-friendly dashboard classifies bug reports and vulnerabilities based on severity, so you have everything you need to come up with a well-informed decision on how to proceed with a finding. Manage findings directly within in your IDE or feed them straight into your favorite ticketing systems, and issue trackers.
Find, Triage, and Fix Security Issues at Scale .