How AI Test Agent autonomously finds bugs
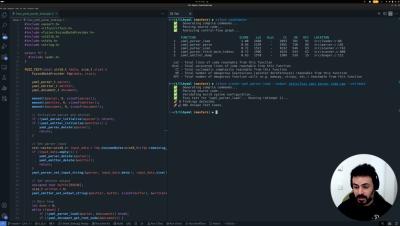
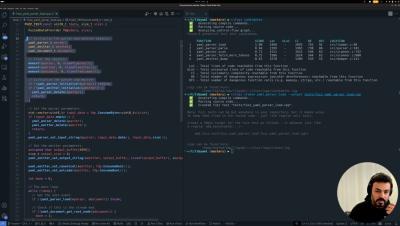
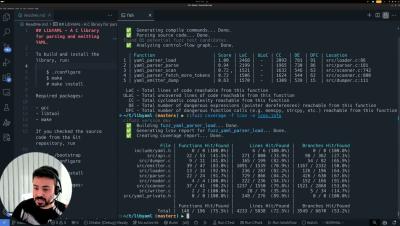
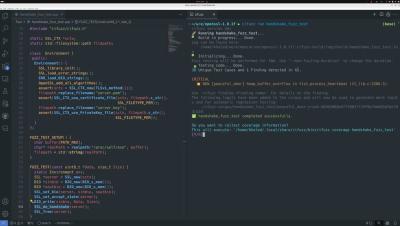
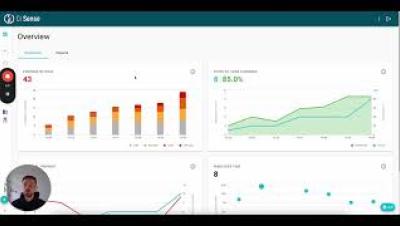
A few weeks ago, we introduced Spark, an AI Test Agent that autonomously uncovers bugs in unknown code with just a single command. Watch the video to see how Spark generated 3 successful fuzz tests, identified a severe vulnerability, and achieved 79% code coverage with just one command. Spark has already identified several real-world vulnerabilities in open-source projects, even those that are continuously fuzzed.