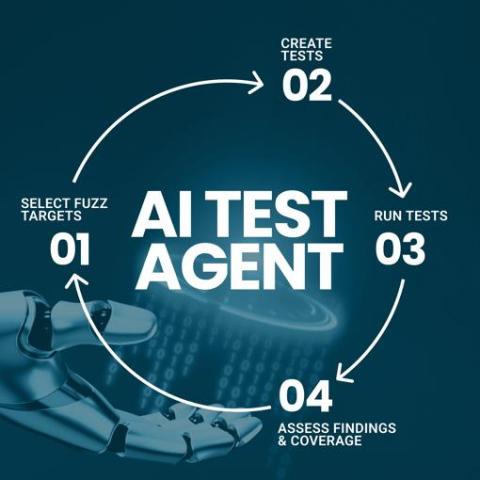
Top Six Most Dangerous Vulnerabilities in C and C++
C and C++ programming are notorious for being bug-prone. Let’s look at the most dangerous software weaknesses in 2024 that are relevant for C and C++, so that you know what type of issues to test your code against in 2025. We examined the 2024 CWE Top 25 Most Dangerous Software Weaknesses list developed by Common Weakness Enumeration (CWE) and identified weaknesses relevant to C/C++. These weaknesses can become vulnerabilities. We explained how they occur and how you can uncover them.