|
By Cenk Kalpakoğlu
Okta Bcrypt Authentication Bypass Explained Last week, on October 30th, Okta released an interesting security advisory detailing a vulnerability that could potentially lead to an authentication bypass. According to Okta, the vulnerability was discovered during an internal review and was promptly addressed. Okta was transparent about the issue, sharing the details publicly.
|
By Andreas Wiese
In this two part blog post we will take a deeper look at eBPF and some of its known vulnerabilities. After a quick introduction to eBPF, how it and its ecosystem works, common attacks, we will talk about how automation and fuzzing can help you to harden your eBPF applications.
CVE-2024-45409 is a critical vulnerability in the Ruby-SAML (affecting versions up to 12.2 and from 1.13.0 to 1.16.0) and OmniAuth SAML libraries. It hence effectively poses a security risk for unpatched versions of GitLab (read more on the GitLab blog). This vulnerability arises from improper verification of the SAML Response signature. An attacker with access to any signed SAML document can forge a SAML Response or Assertion with arbitrary contents.
CVE-2023-2163 is a critical vulnerability in the Linux Kernel, specifically affecting kernel versions 5.4 and above (excluding 6.3). This vulnerability arises from incorrect verifier pruning in the Berkeley Packet Filter (BPF), leading to unsafe code paths being incorrectly marked as safe. The vulnerability has a CVSS v3.1 Base Score of 8.8, indicating its high severity. The consequences are arbitrary read/write in kernel memory, lateral privilege escalation and container escape.
|
By Andreas Wiese
This is the second instalment of a two-part blog post. The blogs are based on one of our “AppSec Talk” YouTube videos, featuring Kondukto Security Advisor Ben Strozykowski and Rami McCarthy, a seasoned security engineer with experience at Figma and Cedar Cares. In that video, Ben and Rami delved into the critical role developers play in the security program and the application security lifecycle.
Application Programming Interfaces (APIs) have become the backbone of modern applications. They enable seamless interaction between different software systems, allowing businesses to innovate rapidly. With the proliferation of APIs comes an increased risk of security vulnerabilities. Ensuring API security is crucial to safeguarding sensitive data, maintaining user trust and protecting the integrity of applications.
|
By Andreas Wiese
Historically, security programs have struggled when they fail to include developers and partner teams, often falling into the trap of focusing solely on the security team’s needs. This approach has led to a disconnect between security and development teams, resulting in ineffective vulnerability management and often strained relationships.
|
By Andreas Wiese
The shift towards a proactive cybersecurity mindset has been steadily gaining momentum. Industry experts have emphasized the importance of best practices for implementation and the role of security orchestration. By integrating modern threat intelligence solutions into vulnerability management platforms, forward-thinking enterprises can become more proactive in their fight against cyber threats.
In this blog, we are going to take a closer look at the concept of Fuzzing, using Go, and how to integrate it into your CI/CD pipeline. As a quick primer, Fuzzing is an automated testing technique that involves feeding random, unexpected, or invalid data to a program or API to uncover bugs and vulnerabilities. The core idea is to expose the program to inputs that developers may not have anticipated, thereby revealing flaws such as crashes, memory leaks, and security vulnerabilities.
|
By Ali Köse
CVE-2024-32002 was published on May 15, 2024 and is affecting versions of Git SCM. The vulnerability exploits a bug where Git can be fooled into writing files into a.git/ directory instead of a submodule's worktree. To fully mitigate this vulnerability additional steps need to be taken beyond updates.
|
By Kondukto
In this episode, Alex Krasnov from Meta shares his thoughts on the supply chain security tools and processes, the impact of government mandates on the evolution of the industry and what lies ahead.
|
By Kondukto
In this episode, we talk with Rami McCarthy from Figma about best practices in security programs including the roles of developers, and effective triage and remediation processes.
|
By Kondukto
Kondukto integrates with OpenAI and gets vulnerability remediation advice for all your security testing results on this concept work. OpenAI is an artificial intelligence research laboratory that surprised the world with ChatGPT. It was founded in San Francisco in late 2015 by Sam Altman and Elon Musk, and many others. ChatGPT grabbed 1M people's attention in the first six days, and unbelievable AI & Human conversations screenshots are still getting shared.
|
By Kondukto
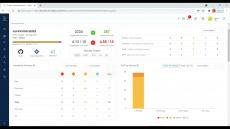
Kondukto allows you to set SLA levels for your vulnerabilities and easily track the ones that are overdue.
|
By Kondukto
You can easily activate Nuclei on Kondukto and scan your applications in no time.
|
By Kondukto
On Kondukto you can apply automated workflows on vulnerabilities that are manually imported to Kondukto as well. In this video, you can see how Kondukto automatically creates issues on issue managers and sends notifications as soon as a new file is imported.
|
By Kondukto
With Kondukto an action taken on a vulnerability discovered in one branch is automatically reflected on the same vulnerability discovered in a different branch.
|
By Kondukto
With Kondukto's Secure Code Warrior integration you can send training videos to your developers to raise awareness about certain types of vulnerabilities.
|
By Kondukto
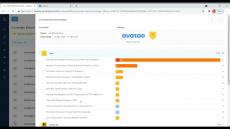
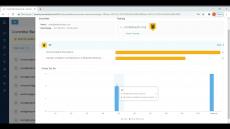
Kondukto lets you pinpoint the developers responsible for vulnerabilities discovered by your SAST tools. After analyzing the type and number of vulnerabilities created by each developer, you can quickly assign courses on Avatao with a single click on Kondukto.
|
By Kondukto
Kondukto lets you pinpoint the developers responsible for vulnerabilities discovered by your SAST tools. After analyzing the type and number of vulnerabilities created by each developer, you can quickly assign courses on Codebashing with a single click on Kondukto.
- November 2024 (1)
- October 2024 (3)
- September 2024 (3)
- August 2024 (2)
- June 2024 (2)
- May 2024 (3)
- April 2024 (1)
- March 2024 (2)
- February 2024 (4)
- January 2024 (3)
- December 2023 (2)
- November 2023 (2)
- October 2023 (3)
- September 2023 (1)
- August 2023 (2)
- July 2023 (1)
- June 2023 (1)
- May 2023 (1)
- April 2023 (2)
- March 2023 (1)
- February 2023 (1)
- January 2023 (1)
- December 2022 (1)
- October 2022 (1)
- September 2022 (2)
- August 2022 (1)
- July 2022 (2)
- June 2022 (1)
- May 2022 (1)
- November 2021 (1)
- September 2021 (1)
- July 2021 (1)
- May 2021 (1)
- March 2021 (1)
- December 2020 (1)
- November 2020 (1)
- October 2020 (2)
- December 2019 (2)
The Kondukto Platform is the ultimate tool for application security teams, allowing them to effortlessly transform vulnerability management, giving back the time, focus, and insight they need to succeed.
Instantly get all security testing tool results in a single view, automate vulnerability remediation workflows and manage risks with key security performance indicators (KPIs).
Effortless efficiency that saves time and money:
- Gain visibility & insight: Speed up prioritization process with the power of orchestration and automation.
- Remediate faster: Reduce distraction and low value work to speed up remediation.
- Boost learning and accountability: Support a culture of continuous improvement with our developer-level vulnerability data.
Accelerate triage and remediation with AppSec orchestration.