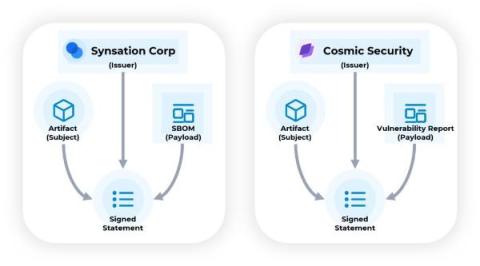
Why you need an SBOM (Software Bill Of Materials)
SBOMs are security analysis artifacts becoming required by more companies due to internal policies and government regulation. If you sell or buy software, you should know the what, why, and how of the SBOM.