Log4j Vulnerability Alert: 100s of Exposed Packages Uncovered in Maven Central
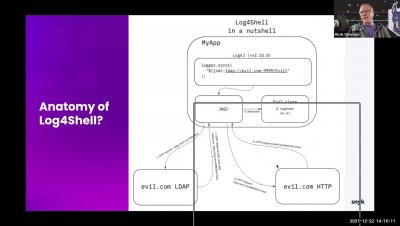
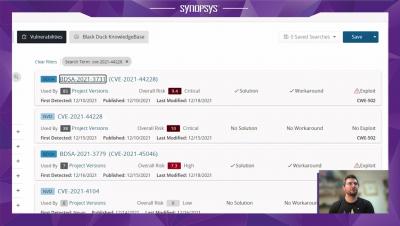
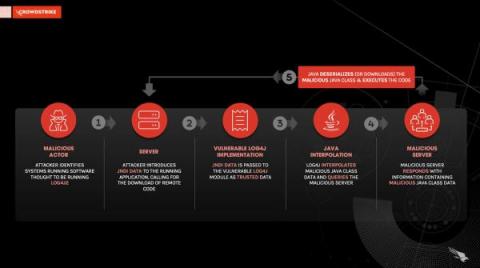
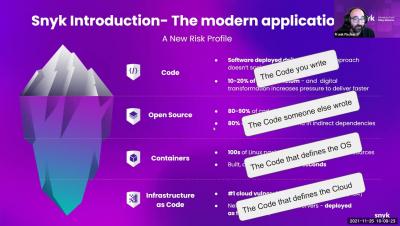
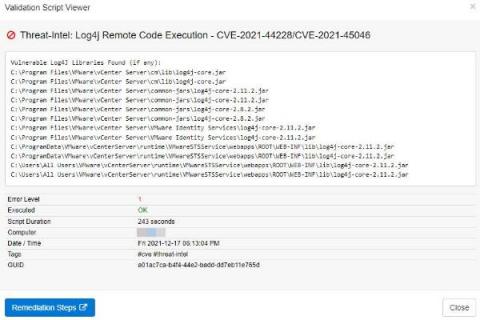
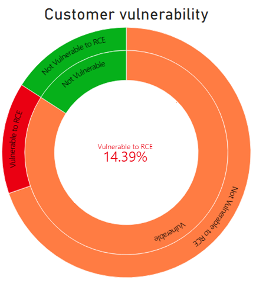
The high risk associated with newly discovered vulnerabilities in the highly popular Apache Log4j library – CVE-2021-44228 (also known as Log4Shell) and CVE-2021-45046 – has led to a security frenzy of unusual scale and urgency. Developers and security teams are pressed to investigate the impact of Log4j vulnerabilities on their software, revealing multiple technical challenges in the process.