- July 2024 (1)
- May 2024 (1)
- February 2024 (1)
- January 2024 (2)
- December 2023 (2)
- November 2023 (2)
- October 2023 (1)
- January 2023 (1)
- October 2022 (1)
- April 2022 (1)
- December 2021 (1)
- June 2021 (1)
- May 2021 (1)
- April 2021 (1)
- December 2020 (1)
- October 2020 (2)
- September 2020 (1)
- August 2020 (1)
- May 2020 (1)
- March 2020 (1)
- February 2020 (1)
- January 2020 (1)
- December 2019 (1)
- July 2019 (1)
- May 2019 (1)
- April 2019 (1)
- March 2019 (1)
- November 2018 (1)
- September 2018 (1)
- July 2018 (4)
- June 2018 (2)
- May 2018 (1)
- March 2018 (1)
- January 2018 (2)
- December 2017 (3)
- November 2017 (5)
- October 2017 (1)
NETIKUS.NET develops EventSentry an award-winning Hybrid SIEM which features real-time eventlog, system health and network monitoring to proactively monitor networks and preemptively respond to threats.
PingSentry Availability Monitoring to help you quickly monitor the availabilty of your criticial resources. From the creators of EventSentry we now offer a way to be notified when your site is unreachable or if your SSL/TLS certificate is experiencing unexpected errors.
Many of our award-winning products and online services are offered for free, including the free version of EventSentry, EventSentry Light, the EventSentry SysAdmin Tools as well as the EventSentry Admin Assistant.
Why EventSentry?
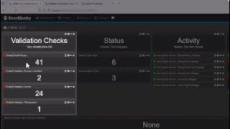
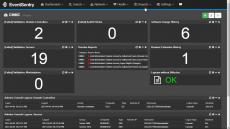
- Single Pane of Glass: EventSentry looks beyond events and log files - by monitoring multiple aspects of Windows-based systems to give you a complete picture - and not just a few pieces of the puzzle. Server monitoring (CPU, Memory, Disk space), performance monitoring, inventory and more monitoring features are all included.
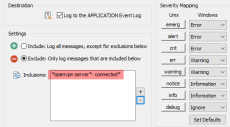
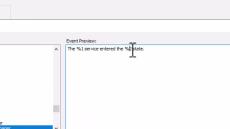
- Real-Time Event Log Monitoring: Our state-of-art agents monitor all Windows servers, workstations & laptops securely, efficiently and in real-time - with native 64-bit support. Data is encrypted & compressed, and collected metrics are cached and re-transmitted during temporary network outages.
- Descriptive Email Alerts: EventSentry's email alerts go the extra mile to make troubleshooting faster and more effective by providing additional context. Footers provide a status of the monitored host, security codes are automatically explained and performance alerts include embedded visual charts. IP addresses contained in emails are supplemented with reverse DNS lookup and geolocation data.
At NETIKUS.NET we make customer support our number one priority, and we work very closely with our users who help us shape and improve our products.