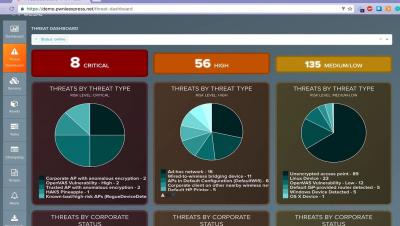
What matters most: VA scans or pen tests
All sources agree that cyber crime is increasing year on year, putting businesses small and large at increasing risk. Attacks jumped by 31% during the height of the 2020 pandemic alone, and is predicted to cost the global economy over $10 trillion by 2025. In order to stay ahead of the hackers, savvy enterprises are stepping up their security scanning regimes by using vulnerability scanning and penetration tests to uncover security flaws.