Creating Trust in an Insecure World: Strategies for Cybersecurity Leaders in the Age of Increasing Vulnerabilities
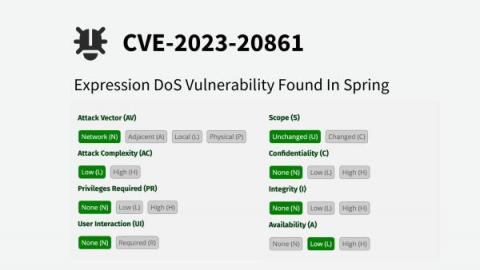
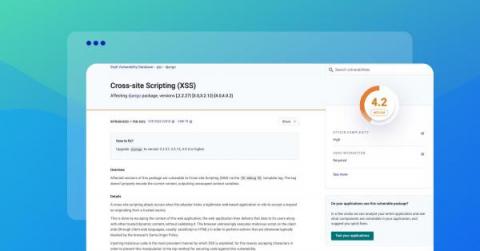
Vulnerabilities are on the rise, and it's not just the number that's growing; the severity of these vulnerabilities is also increasing. Cybercriminals are taking advantage of these vulnerabilities to launch sophisticated attacks, leading to data breaches, ransomware, and other devastating cyber incidents.