Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
February 2022
How to secure web apps continuously with Pen Testing as a Service
Web applications are continuously evolving due to the hypo-velocity of code changes and stream of new features and functionality leaving businesses exposed to application security risks. A new wave of automated pen testing conducted through a software as a service delivery model can help reduce this risk by providing automated vulnerability findings in real time.
Log4j: Separating the exploits from the noise
Critical Vulnerability in the SAP Internet Communication Manager Component Could Lead to Full System Takeover, Patch Available
Solving the CVE puzzle with MITRE ATT&CK and threat intel
Magento security requires additional patch to fix sanitization vulnerability
As technology folks, we are often under a lot of pressure to fix some deployed code, update an infrastructure component, or patch some code. Often it’s with little notice and needs to be done 5 minutes ago. The gamble with any “zero turnaround” is the rush to fix now vs. taking the time to test and check.
CrowdStrike Automates Vulnerability Remediation Processes While Enhancing SecOps Visibility
Adversaries are becoming more adept and sophisticated in their attacks. Taking advantage of vulnerabilities present in major software is often an attractive entry point for establishing a campaign within an enterprise environment. The CrowdStrike 2022 Global Threat Report highlights how adversaries continue to shift tradecraft and weaponize vulnerabilities to evade detection and gain access to critical applications and infrastructure.
What Is Managed Vulnerability Scanning And Why Do You Need It?
Top 8 Uses Of Website Vulnerability Scanners
OWASP Top 10: API Security Threats
4 Best Practices to Reduce Zero Day Exploits
CVE-2022-23628, OPA and Styra DAS
CVE-2022-23628 was published last week by the Open Policy Agent (OPA) project maintainers after a user reported unexpected behavior from a policy bundle that was built with optimizations enabled. The problem stemmed from a regression fix in the v0.33.1 release that addressed incorrect pretty-printing of Rego object literals by the `opa fmt` command and the underlying `format` package.
Conveniently insecure: the tradeoff between security and convenience
When it comes to making business decisions about new technologies and software adoption into your organization – it’s vital to work with your security team to balance the need for speed without sacrificing security.
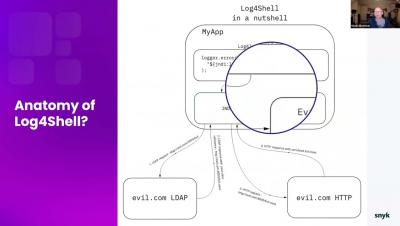
What you need to know about Log4Shell
Photo by ThisIsEngineering from Pexels Considered one of the largest exploitable vulnerabilities in history, Log4Shell affects many as Log4J is one of the most extensively used logging libraries. An issue that has existed for almost a decade but just recently was discovered, Log4Shell leaves companies vulnerable to the full extent of these attacks. AT&T Alien Labs blogged about the vulnerability back in December 2021, with more technical detail.
Welcoming Fugue as we build the future of developer-first cloud security
Today, I am excited to announce Snyk’s acquisition of Fugue and welcome their team to the Snyk family. The addition of Fugue to Snyk’s platform will allow us to continue our mission to help developers find and fix security issues in the applications they create, by providing visibility into the security of applications and the cloud services they use. But it’s about more than just visibility of the cloud posture.
CVE-2022-24086 Vulnerability alert for websites using Magento Ecommerce
Magento has been a much used and loved e-commerce platform since its initial release in 2008. One of the things I’ve always loved about Magento is its ability to grow as ecommerce businesses grow. Starting as a self-hosted version (which I’ve used extensively as a developer over the years), Magento now has clear support and management options available via Adobe or third party ecosystem partners.
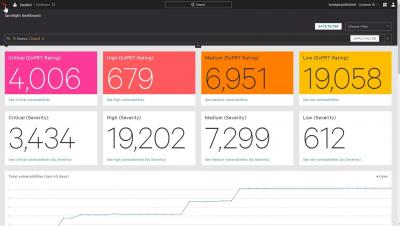
How to Automate Workflows with Falcon Spotlight
How to Perform a Comprehensive Network Vulnerability Assessment
Despite growing awareness and prioritization of cybersecurity, close to 22,000 vulnerabilities were published in 2021 alone. This concerning number proves that awareness and a willingness to invest in cybersecurity aren’t always enough to protect your organization’s network, and that network vulnerability is far from a problem of the past. To protect your networks, you need to continually monitor and assess their potential vulnerabilities to guarantee security.
How to Perform a Comprehensive Network Vulnerability Assessment
Despite growing awareness and prioritization of cybersecurity, close to 22,000 vulnerabilities were published in 2021 alone. This concerning number proves that awareness and a willingness to invest in cybersecurity aren’t always enough to protect your organization’s network, and that network vulnerability is far from a problem of the past. To protect your networks, you need to continually monitor and assess their potential vulnerabilities to guarantee security.
Using the Snyk Vulnerability database to identify projects for The Big Fix
As developers we all have our morning startup routine: make coffee, check slack/discord/email, read the latest news. One thing I do as part of my daily startup routine is check the Snyk vulnerability database for the latest open source vulnerabilities. It’s been especially interesting to see the types of exploits and vulnerabilities that appear in different ecosystems. For example, since May 2021 I’ve been watching the emergence of vulnerabilities in Tensorflow libraries.
A quarter of critical vulnerabilities exposed during penetration tests are not being remediated by businesses
Case study: Python RCE vulnerability in Celery
I conducted research based upon existing Python vulnerabilities and identified a common software pattern between them. By utilizing the power of our in-house static analysis engine, which also drives Snyk Code, our static application security testing (SAST) product, I was able to create custom rules and search across a large dataset of open source code, to identify other projects using the same pattern. This led to the discovery of a stored command injection vulnerability in Celery.
Sysdig and Snyk use runtime intelligence to eliminate vulnerability noise
One of the greatest challenges in cloud environments today is to ensure rapid development cycles while keeping up with security vulnerabilities. Sysdig and Snyk announced today a partnership to deliver integrated code to container runtime security that eliminates up to 95% of vulnerability alert noise, optimizes remediation, and protects runtime. Developers can be fast with security barriers removed, and yet without sacrificing security.
CVE-2021-44521 - Exploiting Apache Cassandra User-Defined Functions for Remote Code Execution
JFrog’s Security Research team recently disclosed an RCE (remote code execution) issue in Apache Cassandra, which has been assigned to CVE-2021-44521 (CVSS 8.4). This Apache security vulnerability is easy to exploit and has the potential to wreak havoc on systems, but luckily only manifests in non-default configurations of Cassandra.
ICMAD SAP Vulnerability (CVE-2022-22536) - Critical Risk
SAP stands for System Applications and Products in data processing, the market leader in ERP software, helping some of the biggest names in the business. The application tier is often the heart of the entire SAP ERP system, looking after interfacing with other apps, transactions, jobs, reporting and database access.
Highlights from the Ultimate Guide to Client-Side Security
In today’s world, businesses, economies, and lives are connected by a complex spider web of code and software applications. This code and these applications drive e-commerce, financial transactions, and data input. They impact our ability to quickly transfer money from one account to another, to fill out an online mortgage application, and to order supplies from a vendor. The code that drives these systems is complicated. If something can go wrong, it will.
OT Vulnerability Management: A Risk-Based Approach
The number of missing security patches in an OT system is typically very large—measured in the thousands, at least. It would be difficult and expensive for an asset owner to evaluate each missing security patch / cyber asset pair. This may be one reason we see a patch everything approach, but this is also difficult and expensive. In fact, assessments show this is rarely done even where required by policy.
CISA Shields Up: How to prepare for the Russia-Ukraine cybersecurity hazard
CISA issues ‘Shields Up’ alert to warn US companies about potential Russian hacking attempts to disrupt essential services and critical infrastructure as the Russia-Ukraine crisis escalates. Get ahead of the situation with essential information.
Recent Examples of Zero Day Attacks & How to Avoid Them
Zero day attacks consist of almost 80% of all malware attacks. Take a look at some recent attacks and learn how to prevent them. You work hard to secure your business network. Yet determined hackers probe persistently until they find a software vulnerability you don’t know about. They use this previously unknown and unpatched flaw.
Lessons learned from the Argo CD zero-day vulnerability (CVE-2022-24348)
On January 30, 2022, , the Argo CD team was contacted by researchers at Apiiro regarding a vulnerability they had discovered in the popular continuous delivery platform that could allow bad actors to steal sensitive information from deployments. The Argo CD team was able to quickly develop fixes for all three of their currently supported releases and publish them to their users within 48 hours.
Log4Shell Peace of Mind in Minutes, Not Weeks
Discovered on December 9, 2021, the log4Shell vulnerability is one of the most talked-about vulnerabilities in computing. Because simple text can be used to take control of a device and download anything that is Internet-accessible, companies are taking it seriously. As they should – log4Shell has the maximum CVSS score of 10 (CVSS, Common Vulnerability Scoring System, is an industry-standard for ranking vulnerabilities).
How to Use the Snyk CLI to Fix Vulnerabilities in Your Application: The Big Fix
From Stored XSS to Code Execution using SocEng, BeEF and elFinder CVE-2021-45919
A stored cross-site scripting vulnerability, tracked as CVE-2021-45919, was identified in elFinder File Manager. The vulnerability can result in the theft of user credentials, tokens, and the ability to execute malicious JavaScript in the user's browser. Any organization utilizing an out-of-date elFinder component on its web application could be affected.
CVE-2021-44142: Critical Samba Vulnerability Allows Remote Code Execution
Recently, a critical out-of-bounds vulnerability, assigned to CVE-2021-44142, was disclosed in Samba versions prior to 4.13.17. The Samba vulnerability carries a critical CVSS of 9.9 and allows attackers to remotely execute code on machines running a Samba server with a vulnerable configuration. The vulnerability was disclosed as part of the Pwn2Own Austin competition where researchers are challenged to exploit widely-used software and devices with unknown vulnerabilities.
New Year, New Features in Xray
How to Protect the Software Supply Chain from Vulnerable Third-Party Code
What happens when the software, scripts and code snippets that your business uses on your website and network have been compromised at the source? The compromise could be unintentional—perhaps the coders simply made a mistake. Or the compromise could be intentional—maybe hackers wrote a malicious script and promoted it as legitimate on a third-party library source to encourage users to download and install.
Triaging vulnerabilities - the way it ought to be
What Is Penetration Testing? Benefits And Pen Testing Vulnerabilities
CVE 2022-24348 - Argo CD High Severity Vulnerability and its impact on Kubernetes
Researcher Moshe Zioni from Apiiro, discovered a major software supply chain critical vulnerability - CVE-2022-24348 - in the popular open-source CD platform Argo CD. Exploiting it enables attackers to obtain sensitive information like credentials, secrets, API keys from other applications. This in turn can lead to privilege escalation, lateral movements, and information disclosure.
How to Protect Cloud Workloads from Zero-day Vulnerabilities
Protecting cloud workloads from zero-day vulnerabilities like Log4Shell is a challenge that every organization faces. When a vulnerability is published, organizations can try to identify impacted artifacts through software composition analysis, but even if they’re able to identify all impacted areas, the patching process can be cumbersome and time-consuming. As we saw with Log4Shell, this can become even more complicated when the vulnerability is nearly ubiquitous.
Log4Shell remediation with Snyk by the numbers
We’re almost two months from the disclosure of Log4Shell, and we here at Snyk couldn’t be more excited with the role we’ve gotten to play in finding and fixing this critical vulnerability that’s impacted so many Java shops. For starters, we’ve been able to help our customers remediate Log4Shell 100x faster than the industry average! How have we been able to achieve that?
ServiceNow - Username Enumeration Vulnerability (CVE-2021-45901)
During a recent engagement Trustwave SpiderLabs discovered a vulnerability (CVE-2021-45901) within ServiceNow (Orlando) which allows for a successful username enumeration by using a wordlist. By using an unauthenticated session and navigating to the password reset form, it is possible to infer a valid username. This is achieved through examination of the HTTP POST response data initially triggered by the password reset web form. This response differs depending on a username's existence.
Pentest 101: How to Dodge the Directory Traversal Vulnerability
Vulns Unleashed: Pwnkit
Top 10 Uses of Website Vulnerability Scanner Tools
Fun with ciphers in copycat Wordles
Here at Snyk, we spend a lot of time researching vulnerabilities. We do that because there are a lot of other folks out there researching new ways to break into apps and systems. We’re often putting on our “grey hats” to think like a malicious hacker. I regularly view-source, look at network traffic and eyeball query strings. One such delicious little query string caught my attention this week on one of the many copycat Wordle sites.
Log4Shell Live Hack: A Hands-on, Actionable Fix Guide
Hunting pwnkit Local Privilege Escalation in Linux (CVE-2021-4034)
In November 2021, a vulnerability was discovered in a ubiquitous Linux module named Polkit. Developed by Red Hat, Polkit facilitates the communication between privileged and unprivileged processes on Linux endpoints. Due to a flaw in a component of Polkit — pkexec — a local privilege escalation vulnerability exists that, when exploited, will allow a standard user to elevate to root.
CVE-2021-44142: Vulnerability in Samba Enables Bad Actors to Execute Arbitrary Code as Root
A number of security vulnerabilities have been identified on the popular freeware, Samba, which implements the Server Message Block (SMB) protocol that allows users to access files, printers, and other commonly shared resources over a network. These flaws enable remote attackers the ability to execute arbitrary code with the highest privileges on affected installations. The most prominent is CVE-2021-44142, which affects all versions of Samba before 4.13.17.
Log4j Update: Brian Roche - Chief Product Officer
The Impact of CVE-2022-0185 Linux Kernel Vulnerability on Popular Kubernetes Engines
Last week, a critical vulnerability identified as CVE-2022-0185 was disclosed, affecting Linux kernel versions 5.1 to 5.16.1. The security vulnerability is an integer underflow in the Filesystem Context module that allows a local attacker to run arbitrary code in the context of the kernel, thus leading to privilege escalation, container environment escape, or denial of service.
Snyk integrates with AWS CloudTrail Lake to simplify security audits
Since organizations around the globe began investing more aggressively in their digital transformation by migrating and modernizing applications within the cloud, the value of audit logging has shifted. It has expanded from industries like finance and healthcare to nearly any company with a digital strategy.