Splunk SOAR Playbooks: Conducting an Azure New User Census
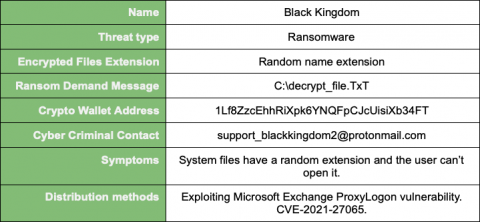
In January and February of 2021, the threat actor called Hafnium used a number of post-exploitation tools after gaining access to Exchange servers through a zero-day exploit. One of their persistence methods was creating new user accounts in the domain, giving them the ability to log back into the network using normal authentication rather than use a web shell or continue to re-exploit the vulnerability (which has since been patched).