Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2023
Building a security-conscious CI/CD pipeline
Continuous integration (CI) and continuous delivery (CD) has become a ubiquitous practice for DevOps teams. The CI/CD process focuses on building and deploying new applications or releasing updates to already-deployed workloads. As a result, most CI/CD efforts focus on enhancing development speeds. However, CI/CD practices can accomplish much more than enabling workload deployments.
The importance of verifying webhook signatures
Webhooks are a callback integration technique for sending and receiving information, such as event notifications, in close to real-time. Webhooks can be triggered by application events and transmit data over HTTP to another application or third-party API. You can configure a webhook URL and connect external participants to customize, extend, or modify workflows. Webhooks may or may not be signed.
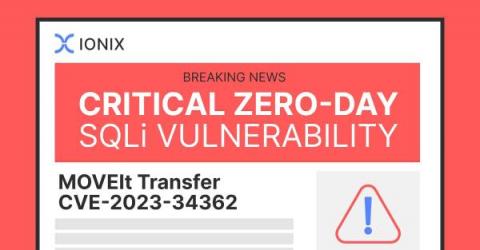
The Nasty MOVEit Zero-Day Vulnerability: How to Respond
MOVEit mayhem: Attackers found, patch released, but no end in sight
The entire cybersecurity realm is buzzing over zero-day vulnerabilities and SQL injection attacks owing to the MOVEit Transfer MFT breach. In case you missed it, here’s the back story, timeline of events, and latest updates. On May 31, 2023, Progress Software rolled out security patches for the recently discovered SQL injection vulnerability in their file sharing application, MOVEit Transfer.
Using insecure npm package manager defaults to steal your macOS keyboard shortcuts
Malicious npm packages and their dangers have been a frequent topic of discussion — whether it’s hundreds of command-and-control Cobalt Strike malware packages, typosquatting, or general malware published to the npm registry (including PyPI and others). To help developers and maintainers defend against these security risks, Snyk published a guide to npm security best practices.
Egress Vulnerability Disclosure Program (VDP)
In today's rapidly evolving digital landscape, cybersecurity remains a top priority for organizations of all sizes. As a leading provider of security solutions, we appreciate and understand the pressures of the current threats that organizations face daily. A critical risk often faced by suppliers is supply chain security. A supply chain attack can undermine a company’s operations and introduce risk at unprecedented levels, potentially leading to a catastrophic outcome.
SNAPPY: Detecting Rogue and Fake 802.11 Wireless Access Points Through Fingerprinting Beacon Management Frames
I’ve always had a great love of all things wireless/RF for as long as I can remember. The ability to send frames/packets of data out into the world (the airwaves!) for anyone with the right equipment and looking at the right frequency to pluck them out and reconstruct them - amazing! I am still the proud owner of both ORiNOCO Gold and Silver PCMCIA cards, these two bad boys defined wireless hacking back in the early 2000’s.
Mimic your mental model with Project Collections
At Snyk we’re constantly trying to improve how you can work with Projects at scale. To continue the journey, we’ve been furthering how you can organize your Projects. There are nearly limitless ways to organize projects outside of Snyk because there is no standard mental model that is used by everyone, for example, some organize projects as mono-repos, and others as application components.
2023 OSSRA deep dive: High-risk vulnerabilities
Remediation Ballet Is a Pas de Deux of Patch and Performance
Generative AI capabilities continue to make their way into every organization, with increasingly useful ways of helping employees and contractors be more productive. This includes advancing how fully automated vulnerability remediation works, and with the power of generative AI, is able to take into account unique environments and uses in real-time.
Maximizing IAM security with AWS permissions boundaries and Snyk
In today's rapidly evolving cloud landscape, managing permissions and ensuring robust security controls are essential for organizations utilizing Amazon Web Services (AWS). AWS Identity and Access Management (IAM) is crucial in managing permissions to access AWS resources. While IAM provides granular control over permissions, AWS IAM permissions boundaries offer additional security and flexibility for fine-tuning access controls.
Responding to remote service appliance vulnerabilities with Sumo Logic
MOVEit Supply Chain Attack
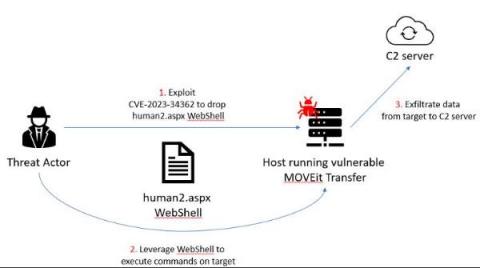
On the 31st of May 2023 a public warning was issued by MOVEit, regarding a critical SQL injection vulnerability found in in their systems. This vulnerability allowed malicious actors to gain access to the database. The flaw, known as CVE-2023-34362, was identified on the 2nd of June, but it had already been exploited four days before the alert. By the end of May, approximately 2,500 instances of MOVEit file transfers were discovered to be exposed online, primarily in the United States.
CVE-2023-33299: Critical Fortinet FortiNAC RCE Vulnerability
How to Spend Less Time Fixing CVEs
Fortinet Fortigate Vulnerability CVE-2023-27997: How to Surface Exposed Devices and Mitigate the Threat
Recently, a critical vulnerability tracked as CVE-2023-27997 was identified in Fortinet Fortigate appliances. Fortinet makes some of the most popular firewall and VPN devices on the market, which makes them an attractive target for threat actors. This vulnerability has been exploited by the Chinese APT group Volt Typhoon, among others, targeting governments and organizations worldwide. As a result, Fortinet has released an urgent patch for affected systems.
Exploiting ancient vulnerabilities: How did the 3CX supply chain attack occur and what can we learn from it?
The Implications of CVSS 4.0 for Cybersecurity
Research with Snyk and Redhunt Labs: Scanning the top 1000 orgs on GitHub
Open source code is a vital aspect of modern development. It allows developers to increase their application’s functionality, while reducing overall development time. However, the system isn’t perfect. The nature of third party software and it’s dependencies often creates opportunity for security vulnerabilities to lurk in libraries and downloads.
Installilng the Snyk Security in Jira Cloud app
HiBob - Can You Please Share Customers' Data?
As part of our ongoing commitment to conducting original research and maintaining an up-to-date Hacker’s Playbook, the SafeBreach Labs team is dedicated to uncovering new threats. My recent research focused on searching for vulnerabilities and design issues in the API security domain in line with this objective. As a result, we discovered a security vulnerability in the popular HR information system (HRIS) platform called HiBob.
CVSS 4.0 - What's New?
The latest version of the Common Vulnerability Scoring System, CVSS 4.0, entered its public preview phase at the 35th annual FIRST conference put on by FIRST, the Forum of Incident Response and Security Teams. An international confederation of computer incident response teams, FIRST writes the CVSS specification that plays such an important role in identifying and cataloging software and application vulnerabilities.
MOVEIt Vulnerability: A Painful Reminder That Threat Actors Aren't the Only Ones Responsible for a Data Breach
The MOVEIt data breach continues to impact a number of both private and government groups across the US and Europe by exposing confidential data. With breaches like this becoming increasingly common, it can be easy to blame advanced persistent threat (APT) groups and other malicious actors; however, there is a valuable lesson to learn from the MOVEit breach: it is essential to be proactive about these threats, Not doing so may lead to a breach.
Ransomware Gangs Exploit Three Zero-Day Vulnerabilities in MOVEit
In quick succession at the end of May into mid-June, software developer Progress released three advisories that any customers using its popular managed file transfer (MFT) solution MOVEit should immediately update to the latest release. In this time, they were made aware of three critical vulnerabilities, CVE-2023-34362 on May 31, CVE-2023-35036 on June 9, and CVE-2023-35708 on June 15.
SnakeYaml 2.0: Solving the unsafe deserialization vulnerability
In the December of last year, we reported CVE-2022-1471 to you. This unsafe deserialization problem could easily lead to arbitrary code execution under the right circumstances. In the deep-dive blog post “Unsafe deserialization vulnerability in SnakeYaml (CVE-2022-1471)”, I explained the problems in this library and how it could be executed. The gist of the problem was that by default SnakeYaml parsed the incoming yaml to the generic object type.
Discovering the MOVEit Vulnerability with the CrowdStrike Falcon Platform
On June 15, 2023, Progress Software announced a critical vulnerability in the MOVEit file transfer software (CVE-2023-35708). This was the third vulnerability impacting the file transfer software (May 2023: CVE-2023-34362; June 9: CVE-2023-35036). The vulnerabilities have been fixed, and all MOVEit Transfer customers are strongly urged to immediately apply all applicable patches.
New CISA Directive Highlights Vulnerabilities at Network Edge
After a wave of zero-day attacks targeting widely used security and networking appliances, the Cybersecurity & Infrastructure Security Agency (CISA) is taking new measures to protect Internet-exposed networking equipment.
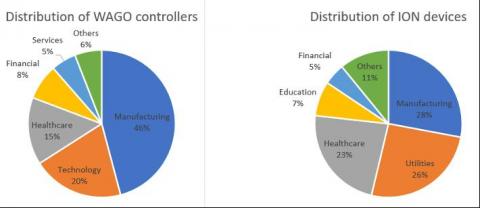
Lessons Learned from OT:ICEFALL - New Vulnerabilities and Insights on OT Security Design and Patching
In our final OT:ICEFALL report, Forescout Vedere Labs presents three new vulnerabilities and concludes the project after one year of research following the original disclosure. The OT:ICEFALL research, including 61 vulnerabilities affecting 13 vendors, has yielded three key insights into the current state of OT product security.
Understanding Kubernetes Pod Security Standards
Kubernetes “crossed the adoption chasm” in 2021 after 5.6 million developers used it to orchestrate their containers, according to the Cloud Native Computing Federation (CNCF). The annual CNCF survey recorded that an impressive 96% of organizations were either contemplating or outright using Kubernetes. However, Kubernetes becomes more appealing to hackers and malefactors as it becomes more popular.
Indusface Threat Coverage: MOVEit Transfer SQL Injection Vulnerabilities
SecurityScorecard Identifies Infrastructure Linked to Widespread MOVEit Vulnerability Exploitation
New disclosures regarding the widespread exploitation of CVE-2023-34362, a new vulnerability affecting the MOVEit file transfer software, and the Cl0p ransomware group’s claim of responsibility for its widespread exploitation and the resulting data theft, have continued in the weeks since the vulnerability’s original publication.
MOVEit Supply Chain Attack Campaign Update
AI vs. Hackers: How Artificial Intelligence is Changing the Game in Cybersecurity
OWASP Machine Learning Top 10 And All About It
Applications of machine learning have grown exponentially over the past few years and with it, the possibilities of malicious attacks targeting it through any vulnerabilities present.
ICS attack classifications: differentiating between Cyberwarfare, Cyberterrorism, & Hacktivism
Every news article about a threat group or attack floods the reader with classifications: nation-state groups, hacktivists, cyberterrorists, etc. But how can we define who is what? How can we differentiate between said categories? How should we deal with potential classification overlaps? Especially in the ever-evolving cyberwarfare realm, how can we approach these closely rooted phenomena?
OWASP Explained: Today's OWASP Top 10
What you need to know about the new 2023 OWASP API Security Top 10
Continuous scanning in your production environment is more important than ever
The SecurityManager is getting removed in Java: What that means for you
The Java Development Kit (JDK) library's java.security package is one of the most important packages, yet despite consistent updates, it remains vastly underutilized. In light of the increased emphasis on cybersecurity frameworks, including zero trust, it's imperative for Java developers to become familiar with Java SE's security libraries. As with any other field in information technology, cybersecurity has a capricious nature. After all, it has to keep up with the latest trends in cybercrime.
Vulnerabilities: The Gateway to Cloud Breaches
A Guide to Handling the MOVEit Attack
Last week, a vulnerability in the popular MOVEit managed file transfer service was exploited by the CL0P ransomware gang to execute data breaches – an increasingly common cybersecurity attack technique where popular software is exploited to target, by extension, their users. Victims of this hack include British Airways, Boots, BBC, and multiple US government agencies.
CVE-2023-34362 - Zero-Day Vulnerability Discovered in MOVEit Transfer is Exploited in the Wild by Cl0p Ransomeware - Here's What you Need to Know
On May 29, 2023, a critical security vulnerability, identified as CVE-2023-34362, was published, leaving users of MOVEit Transfer software at high risk. According to Progress, organizations have reported possible exploitation in the wild. Therefore it’s crucial that any business using MOVEit Transfer to take immediate action, especially since all versions of this popular file transfer software are affected by this vulnerability.
Minimizing Intrusion Detection Time with Cyber Threat Intelligence
With the increasing frequency of cyber-attacks, businesses need to prioritize proactive early incident detection. In this blog, we will highlight the significance of a high-quality threat intelligence solution in building a well-rounded and proactive defense strategy. In an era defined by pervasive connectivity, businesses of all sizes find themselves grappling with an escalating threat of cyber-attacks.
BestinBAS Threat Researchers Discover Their 40th CVE
SafeBreach Labs is the research and development arm of SafeBreach. SafeBreach Labs delivers cutting-edge vulnerability and cybersecurity research as well as novel product ideas. Real-world insights and observations of “in-the-wild” attacks, as well as in-depth and frequent conversations with the top cybersecurity researchers and CISOs worldwide, serve as the foundation for its research and product-related work.
4 Tips to Improve Cybersecurity for Your Business
Snyk named a Leader, placed highest in Strategy category in The Forrester Wave: Software Composition Analysis (SCA), Q2 2023 report
We’re thrilled to announce that Snyk was named a Leader in The Forrester Wave™: Software Composition Analysis (SCA), Q2 2023 report! We believe this recognition — and the fact that we are ranked highest in the Strategy category out of all evaluated vendors — highlights the work we’ve done at Snyk to disrupt the industry with developer-centric application security solutions to help companies secure their software supply chain.
What is a QR Code? Its Usage, Vulnerability, Advantages, and Comeback Story - Part 1
This article helps you understand what a QR code is, how it works, the different types of QR codes, the rise in its usage, the risks involved, the advantages and disadvantages, and whether it is safe.
Mass Exploitation of MOVEit Transfer Critical Vulnerability - Recommended Mitigations and How Forescout Can Help
On May 31, Forescout Research – Vedere Labs uncovered a significant incident where threat actors exploited a critical zero-day vulnerability in the MOVEit Transfer software, which resulted in unauthorized access to and exfiltration of private data, as well as privilege escalation. MOVEit Transfer is a widely adopted managed file transfer (MFT) solution that enables organizations to securely exchange files with their business partners and customers.
Shielding Against the Most Recent Fortinet Vulnerability
During a red team assessment for a client, Charles Fol and Dany Bach from LEXFO, discovered a heap overflow bug in Fortigate’s SSL VPN that can be exploited to achieve remote code execution on Fortigate instances. This vulnerability is reachable without authentication, and can be used to execute arbitrary code on vulnerable systems, which could lead to a complete compromise of the system.
Introduction to Insights by Snyk
KeePass CVE-2023-32784: Detection of Processes Memory Dump
During May, a new vulnerability CVE-2023-32784 was discovered that affected KeePass. KeePass is a popular open source password manager which runs on Windows, Mac, or Linux. The vulnerability allows the extraction of the master key in cleartext from the memory of the process that was running. The master key will allow an attacker to access all the stored credentials. We strongly recommend updating to KeePass 2.54 to fix the vulnerability.
CVE-2023-27997: Critical Fortinet Fortigate SSL-VPN RCE Vulnerability
Benefits of Using a Penetration Testing Dashboard For Your Security Testing Needs
Spear Phishing Attacks: Understanding and Mitigating the Risk
New Vulnerabilities Similar to CVE-2023-34362 Identified in MOVEit Transfer and MOVEit Cloud
Snyk integrates with AWS Security Hub to automate security remediation workflows
AWS Security Hub is a cloud security posture management platform (CSPM) that automates security best practice checks, aggregates security alerts, and understands your overall security posture across different AWS accounts. AWS Security Hub ingests security findings from other security services like Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS IAM, and AWS Firewall Manager — as well as findings from partners like Snyk.
Snyk integrates with Amazon EventBridge to enable secure AppDev at scale
In today’s highly dynamic application ecosystem, the number and scope of security issues that developers need to address have increased dramatically, making it imperative for modern development teams to have an automated system to handle security events across every application component.
Hundreds of Companies Using the MOVEit File Service Lose Confidential Data to a Ransomware Attack
MOVEit, a massive global fire-sharing service provider, recently suffered a data breach that could impact 100's of corporations in the United States, Europe, and many other areas of the world. The file-transfer service provider is supposed to offer a secure transfer solution, and it appears that it may not be as secure as so many hoped. This breach is the result of a ransomware attack, and that attack could result in substantial losses for so many involved.
CleanINTERNET Protects Customers from MOVEit Vulnerability
In early June, multiple threat researchers observed attacks on MOVEit servers using a zero day vulnerability that facilitated data exfiltration. MOVEit Transfer is a managed file transfer software that supports the exchange of files and data. This vulnerability allows an attacker to gain access to the database and possibly infer information about the structure and contents of the database.
Cato Protects Against MOVEit vulnerability (CVE-2023-34362)
A new critical vulnerability (CVE-2023-34362) has been published by Progress Software in its file transfer application, MOVEit Transfer. A SQL Injection vulnerability was discovered in MOVEit enabling unauthenticated access to MOVEit’s Transfer database.
CVE 2023-2868: Barracuda Urges Customers to Replace Compromised Email Security Gateway (ESG) Appliances
Trustwave Action Response: Zero Day Vulnerability in Barracuda Email Security Gateway Appliance (ESG) (CVE-2023-2868)
On May 19, 2023, Barracuda Networks identified a remote command injection vulnerability (CVE-2023-2868) present in the Barracuda Email Security Gateway (appliance form factor only) versions 5.1.3.001-9.2.0.006. In its security advisory, Barracuda said the vulnerability existed in the Barracuda software component responsible for screening attachments for malware. In subsequent days, Barracuda deployed a series of patches.
MailMarshal: Delivering Cloud Based and On-Premise Security Peace of Mind Against Advanced Email Threats
The recent discovery of a zero-day vulnerability in a well-known email security product further underscores the importance of robust email security that can effectively counter advanced email threats, offer a defense-in-depth approach, and operate in the cloud or on-premises. To start, if you believe you have suffered a breach, Trustwave’s Digital Forensics and Incident Response (DFIR) is ready and online to take your call and start helping your organization recover. Click here.
Snyk Security Intelligence Overview
Snyk Security Intelligence: Snyk Vulnerability Database
Snyk Security Intelligence: Snyk Code Knowledge Base
Russian Investigator Detained After Taking 1,000 Bitcoin Bribe From Hackers
Read also: Multiple firms impacted in the widespread MOVEit hacking spree, a hack drains at least $35M in crypto from Atomic Wallet users, and more.
MOVEit File Transfer Zero-day Compromises Multiple Organizations
Snyk Partner Speaks series: True DevSecOps with Snyk and Dynatrace
The latest video in our Snyk Partner Speak Series showcases how Snyk and Dynatrace bring complementary capabilities to different parts of the DevSecOps lifecycle. Check it out and learn how the integration enables organizations to observe, investigate, fix, and govern with a single solution. The Snyk DevSecOps Lifecycle Coverage App is the newest milestone in the Snyk and Dynatrace strategic alliance.
SafeBreach Coverage for US-CERT Alert (AA23-158A) - CVE-2023-3462 MOVEit Vulnerability
On June 7th, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory highlighting the recent efforts of threat actors to disseminate CL0P ransomware. The various malicious indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) being leveraged by the threat actors are listed in US-CERT Alert (AA23-158A) – CL0P Ransomware Gang Exploits CVE-2023-34362 MOVEit Vulnerability.
Clop Ransomware Likely Sitting on MOVEit Transfer Vulnerability (CVE-2023-34362) Since 2021
NOTE: The MOVEit Transfer vulnerability remains under active exploitation, and Kroll experts are investigating. Expect frequent updates to the Kroll Cyber Risk blog as our team uncovers more details. On June 5, 2023, the Clop ransomware group publicly claimed responsibility for exploitation of a zero-day vulnerability in the MOVEit Transfer secure file transfer web application (CVE-2023-34362).
DevSecOps Lifecycle Coverage with Snyk and Dynatrace: Next Level Integrated Solution
CTI Roundup: Microsoft Finds a macOS Bug That Lets Hackers Bypass SIP Root Restrictions
Improved BlackCat ransomware variant strikes with lightning speed in stealthier attacks, Microsoft finds a macOS bug that lets hackers bypass SIP root restrictions, and Dark Pink hackers continue to target government and military organizations.
3 Reasons to Leverage AI for Enhanced Threat and Vulnerability Management
As the cyber threat landscape continues to evolve, you know there’s a growing need to ensure applications and software are protected from malicious actors. A holistic and intelligent approach to threat and vulnerability management is essential for ensuring security against modern cyber risk. By leveraging AI-powered tools, especially for tasks like remediating security flaws, you can manage and reduce risk quickly and effectively.
Application Vulnerability Management: The Complete Guide
Snyk welcomes Enso: Enabling security leaders to scale their AppSec program with ASPM
As we approach the second half of 2023, both security and development teams are seeing seismic shifts in the application security world. AI is powering a productivity revolution in development, enabling developers of all types (and even non-developers) to introduce code faster than ever. Meanwhile, it’s more difficult than ever for developers and AppSec professionals to identify and prioritize true risk to the business.
Snyk Learn now aligns with the NIST NICE Workforce Framework
We are excited to announce that Snyk Learn, our developer-first cybersecurity education platform, is now aligned with the National Institute of Standards and Technology's (NIST) National Initiative for Cybersecurity Education (NICE) Framework.
Reduce risk to your supply chain with a software bill of materials (SBOM)
Today, we’re excited to launch a few new features as part of our ongoing efforts in our Software Supply Chain Security solution. These developer-first tools help you gain a better understanding of your app’s supply chain, identify potential risks, and take the necessary steps to get ahead of them.
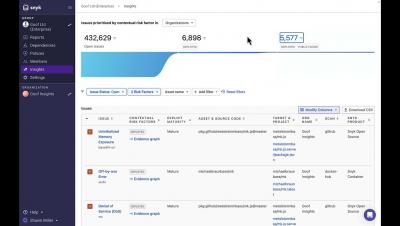
Announcing Insights: Helping you focus on top risks for your organization
Modern applications are built, deployed and, run in increasingly complex and dynamic environments. Assessing and prioritizing the security issues introduced by these applications without taking this context into account inevitably leads to focusing remediation efforts on the wrong set of issues. This not only results in real risk slipping under the radar but also wastes the valuable time of developers, increasing their frustration and eroding their trust in security.
SnykLaunch June '23: Insights and DeepCode AI enable faster fixes and prioritization
As we approach the second half of 2023, both security and development teams are seeing seismic shifts in the application security world. DevOps practices continue to evolve, meaning that developers are introducing code more and more rapidly, andwith the help of AI, developers of all kinds are able to create code faster than ever. Plus, apps aren’t just made up of first-party code and third-party dependencies anymore.
Introducing parlay, a tool for enriching SBOMs
The increasing adoption of software bill of materials (SBOM) standards are starting to drive better interoperability between security tools. The NTIA’s work on defining a minimum set of elements for an SBOM was a key part of that, especially with multiple formats like CycloneDX and SPDX in widespread use. But with work on SPDX 3.0 and CycloneDX 1.5 progressing, there are lots of things we can do with the SBOM formats beyond the minimum elements.
What can you do with an enriched SBOM? A parlay quickstart guide
We just released parlay, a new open source tool that can enrich SBOMs with additional information. You can read more in the announcement blog post. In that post, we briefly mentioned why this is important for decision-making based on SBOM data, but thought a few quick examples might be interesting. parlay can add a lot of extra information to an SBOM, and we can use that information to write more powerful policies.
Three Steps to Prevent a Cybersecurity Breach from MOVEit Exploit
SecurityScorecard conducted an extensive investigation into the Zellis breach. This research revealed alarming insights about the scale and persistence of the attack. The data exfiltration was carried out in several steps: Netflow data from Zellis IP ranges indicated large outbound transfers over HTTPS, which pointed towards the presence of a web shell. Additionally, SecurityScorecard researchers detected exfiltration over SSH to known malicious IP addresses.
Using Insights (Snyk)
MOVEit and Lose it: Exploitation and Patching Hell
Outpost24 acquires external attack surface management provider Sweepatic to reduce risk exposure of internet facing assets
Outpost24, a leading cybersecurity risk management platform, today announced the acquisition of Sweepatic. Outpost24, a leading cybersecurity risk management platform, today announced the acquisition of Sweepatic. Based in Leuven (BE), Sweepatic is an innovative external attack surface management (EASM) platform. Gartner identified EASM as a top Security and Risk Management (SRM) trend for 2022.
Responding to the Critical MOVEit Transfer Vulnerability (CVE-2023-34362)
On May 31, 2023, Kroll received multiple reports that a zero-day vulnerability in MOVEit Transfer was being actively exploited to gain access to MOVEit servers. Kroll has observed threat actors using this vulnerability to upload a web shell, exfiltrate data and initiate intrusion lifecycles. This vulnerability may also enable a threat actor to move laterally to other areas of the network.
Risk-based Vulnerability Management: A Bigger Bang for Your Buck
Every five to ten years, major technology shifts change the way that vulnerability assessment and the related IT risk mitigation processes are approached or implemented. What has remained constant is the formula we use to measure risk and thus prioritize and triage vulnerabilities. Risk = (Likelihood of event) * (Impact of consequences) It’s an approach that intuitively makes sense, but there have been two challenges with how this formula has been applied.
Snyk scanning capabilities are now embedded in Jira Software
Today, development is faster than ever. More apps and code are being written than ever before. There are more third-party dependencies in use to speed development, more containerization, and even code that controls the deployment and configuration of apps and the cloud. To ship quickly, developers need to stay on top of security issues. They want to understand how to build secure applications by getting feedback as they work.
OWASP API Security Top 10 2023 Explained
The Open Web Application Security Project (OWASP) is a non-profit foundation devoted to web application security. One of OWASP's guiding principles is that all of their resources should be freely available and simple to find on their website, enabling anyone to increase the security of their own web applications. They provide forums, tools, videos, and documentation among other things.
Checklist for Developers to Build Secure APIs
Movin' Out: Identifying Data Exfiltration in MOVEit Transfer Investigations
CrowdStrike incident responders have been at the forefront of investigating impacted victims of CVE-2023-34362. Since the release of the vulnerability, there has been great collaboration across the cybersecurity industry, and this blog will cover novel details for teams investigating the potential impact to their organizations.
CVE-2023-34362: SQLi Zero Day Vulnerability in MOVEit Transfer exploited in the wild
CVE-2023-34362 is an SQL injection (SQLi) vulnerability that has been found in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain unauthorized access to MOVEit Transfer’s database. SQL Injection (SQLi) poses significant risks as it allows attackers to potentially steal, manipulate, or delete sensitive data from databases.
Don't Get a PaperCut: Analyzing CVE-2023-27350
A day in the life of an ethical hacker
Ethical hacking refers to the practice of using hacking techniques to identify and expose vulnerabilities in computer systems, networks, and applications. Unlike malicious hackers, ethical hackers use their skills and knowledge to help organizations and businesses identify security weaknesses before they can be exploited by malicious actors. Ethical hacking can include a range of activities, from scanning and penetration testing to social engineering and physical security testing.
Ethical hacking techniques
Ethical hacking is used to find potential security issues in computer systems and networks. In this post, we’ll cover a collection of techniques and procedures commonly used by ethical hackers to find vulnerabilities before malicious users can take advantage.
Sysdig Launches Vulnerability Overview Landing Page
Trustwave Action Response: Zero Day Exploitation of MOVEit (CVE-2023-34362)
On May 31, threat actors were discovered targeting a critical zero day in MOVEit Transfer software resulting in escalated privileges and unauthorized data access. The vulnerability being exploited is an SQL injection and has since been patched. Resources links, including one for the patch, are at the bottom of this post. MOVEit Transfer is a managed file transfer (MFT) solution developed by Ipswitch (a subsidiary of Progress Software).
Over 2 million Websites Vulnerable to XSS Exploit (CVE-2023-30777) in WordPress Plugin
Vulnerability prediction insights from Outpost24 on Smashing Security
The Smashing Security podcast recently invited our Director of Product Management, John Stock, on to discuss our Vulnerability Prediction Technology (VPT) tool, the security challenges brought by remote work, and the importance of balancing risk management with business goals.
CVE-2023-34362: MOVEit Transfer SQL Injection Vulnerability Actively Exploited in the Wild
CVE-2023-33733: RCE Vulnerability in ReportLab PDF Toolkit
Netskope Threat Coverage: MOVEit Transfer Zero-Day
A new critical zero-day vulnerability in the MOVEit Transfer software is being actively exploited by attackers to exfiltrate data from organizations. MOVEit Transfer is a managed file transfer (MFT) software, developed by Progress, designed to provide organizations a way to securely transfer files, which can be implemented on-premise or as a cloud SaaS platform. According to BleepingComputer, attackers have been actively exploiting MOVEit Transfer to download data from organizations.
CyRC Vulnerability Advisory: CVE-2023-32353, Apple iTunes local privilege escalation on Windows
Decade-old critical vulnerability in Jetpack patched on millions of WordPress websites
Jetpack, an extremely popular WordPress plugin that provides a variety of functions including security features for around five million websites, has received a critical security update following the discovery of a bug that has lurked unnoticed since 2012. Jetpack's maintainers, Automattic, announced on Tuesday that it had worked closely with the WordPress security team to push out an automatic patch for every version of Jetpack since 2.0.
A quick primer on LDAP injection
Lightweight Directory Access Protocol (LDAP) is an authentication mechanism for securing web applications. LDAP is popular because it's lightweight and scales easily — features that appeal to developers, but mean that LDAP databases often store large amounts of valuable information. This makes them an attractive target for attackers. Applications construct LDAP queries derived from user inputs to access and manipulate the information stored in LDAP databases.
All About OWASP Large Language Model (LLM) Top 10
Large language models have gained immense popularity among web users today owing to the generation of human-like text responses. However, as with any technology, LLM is not without its risks and safety issues.
OWASP: Web Application Threats
Web applications are the backbone of any online presence. They allow companies to reach customers, communicate with them, and even store sensitive data. Unfortunately, this also means that web applications can be targeted by attackers who want to exploit weaknesses in their security measures.