|
By Jackson Harrower
For our introduction to the challenge, please see Part I.
|
By Anirban Banerjee
This article explores why AI is complicating compliance and the critical steps enterprises must take to avoid regulatory pitfalls.
|
By Christopher Widstrom
In this blog post, we will share our current understanding of the User Personas involved with Ricosity today. Job titles and responsibilities may vary, but the following User Personas are a reflection of the average users we meet who hold these roles at their organizations.
|
By David Schlesinger
A few months ago I received a call from my Grandma. She was concerned about having received a notification that she had been part of a data breach and wasn’t sure what to do about it. She had many seemingly basic, but good questions; What’s PII? I use the app on my iPad, is it safe to log into other applications like my bank? Is it safe to use my account? How do I know when it’s safe?
|
By Jackson Harrower
Traditionally, data security focused on protecting data at rest within the confines of your on-premise data center. The cloud era has blurred these lines. Data now flows through complex pipelines, often traversing multiple services and third-party vendors. This expanded data perimeter creates new vulnerabilities: It’s crucial to ensure that the data loaded into warehouses and analytics tools is scanned for sensitive information and redacted or redirected accordingly.
|
By Jackson Harrower
Successful AI integration begins with clearly defined business objectives. Avoid chasing the latest AI trend and instead focus on how AI can directly address your organization's key challenges and opportunities. Consider these questions.
|
By Anirban Banerjee
Region: European Union (Global impact for companies handling EU residents' data) Scope: Data privacy, security, and governance The GDPR sets the gold standard for data protection, demanding comprehensive compliance across a spectrum of activities. Organizations must ensure lawful data processing, gain explicit consent, enable data portability, and implement measures like data protection by design and default.
|
By Anirban Banerjee
This article explores the recommended infrastructure for AI workloads, strategies to optimize performance on less expensive servers, and trade-offs in terms of cost and results. We’ll also provide examples of AWS EC2 instance types and pricing to illustrate practical options.
|
By Christopher Widstrom
Riscosity’s premier capability to automatically act upon any data type that organizations’ products are sharing with 3rd party vendors has been enhanced even further to support SFTP traffic. Now, any data type going over SFTP to any 3rd party vendor can be automatically blocked, redacted, or notified about.
|
By Anirban Banerjee
Regex patterns are inherently rigid and prone to generating false positives, especially in large, diverse datasets. For example: These false positives require manual verification, leading to an overwhelming workload for security teams.
|
By Riscosity
Welcome to the fourth installment of Riscosity’s Lightning Interview Series Today we sit down with Microsoft Customer Security Officer Terence Jackson for a conversation on the latest in protecting data in the age of GenAI.
|
By Riscosity
Riscosity is the world's most full featured data governance, security and privacy platform. Understand what data types are being exchanged with AI services and govern them - in minutes, not months.
|
By Riscosity
Welcome to the third installment of Riscosity’s Lightning Interview Series In this episode, we sit down with Barak Engel, founder and CEO at EAmmune, and CISO at MuleSoft, Amplitude, StubHub, BetterUp, and Faire among others. Barak is also the author of Why CISOs Fail, The Security Hippie, and The Crack in the Crystal. Ever wonder how you pentest a novel? Tune in to find out.
|
By Riscosity
Welcome to the second installment of Riscosity’s Lightning Interview Series In this episode, we sit down with Michael Machado, a security industry veteran and former CISO at public and pre-IPO companies including RingCentral, Shippo, and BeyondTrust. Ever wonder the best strategy for gaining meaningful budget increases as a CISO? Tune in to find out.
|
By Riscosity
Welcome to the first installment of Riscosity’s Lightning Interview Series. We'll be sitting down with industry leaders for informative and to-the-point conversations. In this episode, we chat about the present and future of internal audit and data security with Nauzer Gotla, Vice President of Internal Audit at Nextracker (NASDAQ:NXT), a dominant player in solar tracking solutions with revenues north of $2.5B.
|
By Riscosity
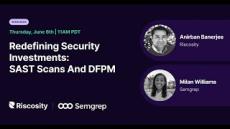
In today's ever-evolving digital landscape, teams must have a strong understanding of the security measures that will work best for their environment and how to implement them. During this event, we explore the benefits of utilizing SAST scans and DFPM (Data Flow Posture Management) tools to create robust security guardrails for your organization. Hear from Anirban Banerjee, CEO and Co-founder of Riscosity, and Milan Williams, Sr. Product Manager at Semgrep, as they dive into how teams can approach security investments starting with SAST scans and data flow security.
|
By Riscosity
A wonderful conversation with two amazing security leaders! We talk about compliance, security programs, API security, Software supply chain, strategies - and oh so much more. A true treat for security lovers.
|
By Riscosity
In this video we talk with two security leaders, very well known, from the Bay Area - Mike Hamilton and Barak Engel. A variety of topics, including software supply chain, data governance and APIs amongst many are discussed.
|
By Riscosity
An amazing conversation with Peeyush Ranjan, Engineering VP at a Fortune 50 organization. Peeyush coined an amazing term - "Diffused Responsibility" - this is the reason why we all, in different silos, development, security, GRC, legal have to try harder and pull towards the same goal. In fact the example used - of a sports team, getting the pigskin over the line is a very apt one.
|
By Riscosity
We chat about the Health-tech space. What are the challenges of building a Healthtech company, where are the roadblocks, what should you look out for - very introspective feedback from Punit! A must hear for entrepreneurs..
- February 2025 (11)
- January 2025 (10)
- December 2024 (6)
- November 2024 (9)
- October 2024 (7)
- September 2024 (2)
- August 2024 (5)
- July 2024 (1)
- June 2024 (2)
- May 2024 (1)
- April 2024 (2)
- March 2024 (3)
- February 2024 (3)
- January 2024 (3)
- December 2023 (4)
- November 2023 (4)
- October 2023 (2)
- August 2023 (1)
- June 2023 (3)
- March 2023 (1)
- January 2023 (1)
- October 2022 (3)
- April 2022 (1)
- March 2022 (1)
- February 2022 (5)
- January 2022 (5)
- November 2021 (1)
Riscosity enables full control, visibility, and compliance for data going to third parties and AI tools. Deployed on-prem and in your private cloud.
Riscosity is the data flow security platform that empowers teams to have full visibility of third party data in transit and automate the redaction or redirection of sensitive data simplifying how companies meet security and privacy standards.
How it works:
- Monitor: Track and pinpoint any data being sent to a third party API.
- Track: Easily map data sub processors and the information shared with them.
- Remediate: Automatically replace detected sensitive data with redacted inputs.
- Comply: Continuously monitor and block APIs from sending the wrong data to the wrong place.
Deploy Riscosity in your production or development environment to monitor, identify, redact, and secure all third party APIs.