Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Stripe OLT
CrowdStrike Windows Outage
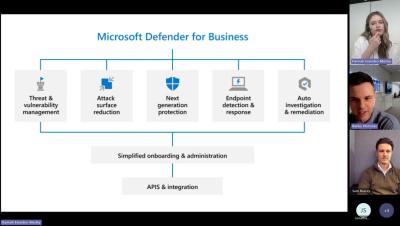
Microsoft Defender for Business - A Stripe OLT Security Essentials Webinar
Copilot for Microsoft 365 - The Ultimate Webinar with Stripe OLT
Microsoft Threat Protection Specialisation
As you may have seen in the press earlier this year, Stripe OLT recently achieved two crucial Microsoft certifications, in both Modern Work and Security. These certifications (also known as designations) are important to Microsoft solution partners because they signify a deep understanding and proficiency of specific Microsoft technologies.
XDR vs SIEM: Cost-Efficient Cyber Security for Today's Decision Makers
CISOs and IT leaders are tasked with the critical responsibility of safeguarding their organisations against an ever-increasing array of threats, all while striving to optimise costs and drive business growth. CISOs are grappling with the demand to achieve more with limited resources this year—a challenge that many have not encountered before.
Microsoft's Anatomy of a modern attack surface: A breakdown
In today’s hyper-connected digital landscape, cyber security has grown increasingly complex. Organisations are shifting operations to the cloud, enabling remote work, and engaging with third-party ecosystems, expanding the potential attack surfaces. Threat actors are exploiting this complexity with high-volume, multi-faceted attacks.
Benefits of conducting a Penetration Test in your Microsoft Environment
Penetration testing is a pivotal strategy amongst various security methodologies, aimed at bolstering an organisation’s digital environment. Commonly known as “pen testing” or “ethical hacking”, this type of test represents a structured and regulated method for assessing the security integrity of a company’s digital ecosystem.
SMB Workshop Business Premium Webinar: Stripe OLT X Microsoft
The Stealthy Threat of AI Prompt Injection Attacks
Just last week the UK’s NCSC issued a warning, stating that it sees alarming potential for so-called prompt injection attacks, driven by the large language models that power AI. The NSCS stated “Amongst the understandable excitement around LLMs, the global tech community still doesn‘t yet fully understand LLM’s capabilities, weaknesses, and (crucially) vulnerabilities.