Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
August 2024
Understanding OWASP Top 10 Client-Side Risks
Websites rely heavily on client-side code to deliver interactive user experiences. Unlike server-side code, which is protected within an organization’s infrastructure, client-side code runs in the user’s browser and is exposed to various risks such as data theft and JS injection. Recognizing the unique challenges of securing client-side code, OWASP has created a dedicated Top 10 list for client-side security risks.
How Frequently Should We Run a Vulnerability Scan?
All it takes is a single unpatched vulnerability to breach security and gain access to a company’s mission-critical assets. Effective vulnerability management is essential for strong cybersecurity. Vulnerability scans play a key role in this process, offering a clear view of the entire IT infrastructure and identifying existing vulnerabilities. How many times should we run scans? Are we scanning often enough? These are the questions we often get.
The persistent threat: Why major vulnerabilities like Log4Shell and Spring4Shell remain significant
As developers, we're constantly juggling features, fixes, and deadlines. Yet, a lurking issue has been surprisingly overlooked: the continued use of vulnerable Log4j and Spring Framework versions in many projects. Despite the high-profile exposure of Log4Shell and Spring4Shell vulnerabilities, a shocking number of applications are still running on these ticking time bombs. This isn't just a minor oversight — it's a major risk.
Predictive Vulnerability Management: Operationalizing EPSS with Business Context
Join us for an in-depth webinar on the Exploit Prediction Scoring System (EPSS), a powerful tool for predicting the exploitability of vulnerabilities. This discussion features experts Jay Jacobs from Cyentia and Stephen Schafferr from Peloton Interactive. They explore the intricacies of EPSS, its application, and the benefits of using EPSS over traditional methods like CVSS for better vulnerability management. Key topics include operationalizing EPSS, leveraging threat intelligence, and creating effective prioritization strategies. .
Building a Remediation Plan? How to Overcome the Top 5 Challenges
Building an effective remediation plan is crucial for enhancing security posture, ensuring compliance and minimizing operational risks. Modern attack surfaces with their ever-growing volume of vulnerabilities have only compounded pressures on remediation planning. Yet vulnerability and exposure management teams frequently encounter obstacles that slow down remediation planning, leading to increased risk exposure and potential regulatory penalties.
Beyond Patches and CVEs: The New Dynamics of Enterprise Technology and Vulnerability Management
The enterprise technology landscape has changed significantly, driven by the rapid adoption of cloud technologies, evolving IT infrastructures, and evolving exploitation activities. This transformation requires that organizations take an updated approach to vulnerability management—one that goes beyond the traditional focus on patch management to encompass a broader spectrum of risks.
Agent hijacking: The true impact of prompt injection attacks
Over the last 18 months, you’ve probably heard about Large Language Models (LLMs) like OpenAI’s GPT and Google’s Gemini. Whether you’re using them as a personal research assistant, an editor, or a data analyst, these tools represent a new frontier of Machine Learning (ML) and Artificial Intelligence (AI) and arguably will have the most significant impact of any technology in this decade.
Network Vulnerabilities and Threats: A Cyber-Security Challenge
The digital world is under constant risk as cyber-attacks are becoming increasingly advanced and increasing at a staggering rate. While significant developments have been made to mitigate cyber risk, network security threats continue to evolve further to get unauthorized access and steal data from companies. According to Cloudwards Cybersecurity Statistics 2024, Cybersecurity intrusions increased by 613% from 2013 to 2023.
Prioritize Vulnerability Remediation Efforts
Prioritization is essential for efficient remediation. But with an overload of findings and limited context, more time is spent filtering through the noise than reducing risk. Learn how Seemplicity's RemOps platform.
Advancing Cybersecurity with Continuous Threat Exposure Management
This SANS whitepaper delves into the Continuous Threat Exposure Management (CTEM) framework and how it has transformed the way organizations manage risks.
Jumpstart Your CTEM Program
Unlock the full potential of your Continuous Threat Exposure Management (CTEM) strategy with Seemplicity's RemOps platform. With RemOps-powered CTEM, you can streamline vulnerability management, reduce remediation times, and enhance collaboration between teams.
The 2024 Remediation Operations Report
Unlock essential insights into the latest trends, challenges, and best practices in vulnerability management and risk remediation.
2024 Strategic Roadmap for Managing Threat Exposure
According to Gartner, through 2026, over 40% of organizations will rely on consolidated platforms or managed service providers for cybersecurity validation assessments. Many security teams currently use isolated approaches focused more on threat type and severity than on actual organizational impact. This reactive strategy doesn't effectively manage the complexities of an ever-evolving cybersecurity landscape and is unsustainable for effective exposure management.
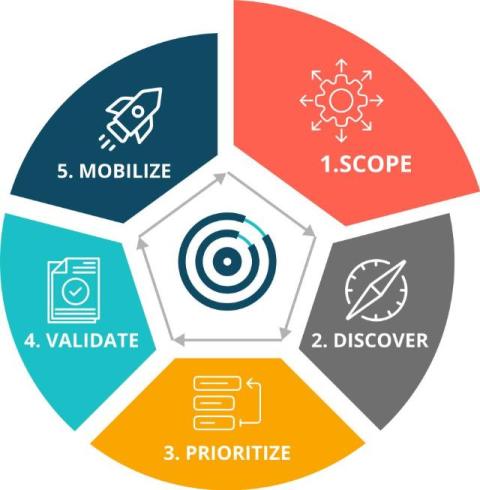
CTEM step-by-step guide | Stage one: Scoping
Welcome to our blog series on Continuous Threat Exposure Management (CTEM), where we dig into the five essential stages of implementing a robust CTEM program. Coined by Gartner in 2022, CTEM is a powerful process that can help continuously manage cyber hygiene and risk across your online environment. It’s also a lot to think about when you’re starting out, so it helps to break things down. Our series begins with the crucial first stage: Scoping.
ARMO's new security-boosting summer cocktail: Layered Vulnerability Scanning, SBOM View, and new Auto-Generated Network Policies
This summer ARMO is proud to announce a batch of new features designed to enhance your cloud security posture. We developed groundbreaking capabilities for in-depth vulnerability scanning, simplified vulnerability management with SBOM view, and streamlined network policy generation for two popular CNIs, Calico and Cilium.. We invite you to explore these new features and discover how they can add to your organization’s security. Let’s go.
CVE-2024-40766: Critical Improper Access Control Vulnerability Impacting SonicOS
On August 22, 2024, SonicWall published a security advisory regarding a critical improper access control vulnerability in several SonicWall Firewall models. This vulnerability, identified as CVE-2024-40766, is a flaw in SonicOS, the operating system that powers these firewalls. CVE-2024-40766 allows a remote, unauthenticated attacker to gain unauthorized access to resources and/or cause the firewall to crash under specific conditions.
Snyk Code, the only security tool chosen by developers in Stack Overflow's 2024 AI Search and Developer Tools survey
Snyk Code was the only code security tool shortlisted by developers as an AI tool they’ve been regularly using this past year or are looking forward to using next year in Stack Overflow’s recent 2024 AI Search and Developer Tools survey. This underlines Snyk’s dominance as the favorite AI security tool of both developers and security teams and confirms that Snyk Code is providing immense value to developers.
Windows Downdate Attacks, Quick Share Vulnerability Exploit, and More: Hacker's Playbook Threat Coverage Round-up: August 2024
In this version of the Hacker’s Playbook Threat Coverage round-up, we are highlighting attack coverage for several new threats, including those discovered via original research by the SafeBreach Labs team. SafeBreach customers can select and run these attacks and more from the SafeBreach Hacker’s Playbook to ensure coverage against these advanced threats. Additional details about the threats and our coverage can be seen below.
Navigating the AI-powered development era in financial services
Australian and New Zealand financial service institutions (FSIs) are facing pressure to innovate quickly while maintaining robust security and regulatory compliance. Many, like ANZ Bank and Commonwealth Bank, are exploring Generative AI to accelerate software development, but is it a silver bullet?
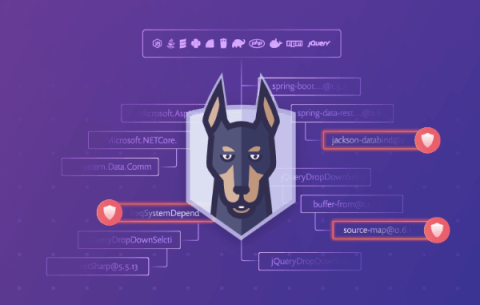
A developer's best friend: Lessons learned from our canine companions about AI code security
Happy International Dog Day! This official holiday celebrates our furry friends and the joy they bring to our lives! Today is particularly special for all of us at Snyk because of our four-legged mascot, Patch the Doberman. But what exactly does a dog have to do with application security? Here at Snyk, we see the idea of a “guard dog” protecting someone’s home as similar to how AppSec solutions can protect today’s development practices.
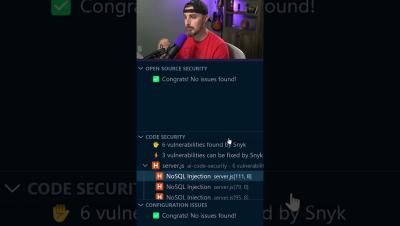
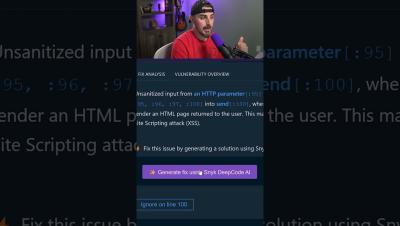
How AI Almost Got Me FIRED: Part 3
How many jobs has AI lost me now?...Joking! In this video we show you the AI coding tool Cody, and how to use Gemini Pro 1.5 and Mixtral alongside it. We also show how to spot and fix any vulnerabilities that get generated.
The Hidden Risks of Internet of Bodies (IoB): Cybersecurity in Healthcare Devices
The Internet of Bodies, or IoB, represents a groundbreaking shift in the healthcare industry, connecting vital health management devices like pacemakers, insulin pumps, and health monitors to the Internet. While these advancements come with many remarkable benefits, they also expose these essential devices to new cybersecurity vulnerabilities.
Seemplicity's Remediation Operations Platform | Product Explainer
Discover Seemplicity Remediation Operations (RemOps) Platform. See how Seemplicity's AI-powered platform streamlines exposure management, integrates with existing tools, and automates AI-powered tailored remediation plans. Learn how our platform helps your security and development teams collaborate effectively, rapidly address vulnerabilities, and enhance compliance, productivity, and overall security posture. Reduce risks across multiple domains and stay ahead in today's evolving threat landscape with Seemplicity's RemOps Platform.
Google Fixes Actively Exploited Chrome Vulnerability
Google has recently released an urgent security update to fix a high-severity vulnerability in its Chrome browser. This flaw, identified as CVE-2024-7971, has been actively exploited by attackers, posing a significant risk to users. The vulnerability, rooted in the V8 JavaScript and WebAssembly engine, could allow remote attackers to execute harmful code via specially crafted web pages. As cyber threats continue to evolve, it is crucial for users to stay informed and ensure their browsers are up to date.
Elevate Your Security Strategy with Effective Vulnerability Prioritization
Vulnerability prioritization is essential for organizations to efficiently allocate resources, reduce risk, and protect critical assets. However, with an increasing number of vulnerability scanning tools in use, security teams face a growing backlog of findings. This overwhelming volume of data can lead to analysis paralysis, where critical vulnerabilities remain unaddressed while minor issues consume valuable time and resources.
CVE-2024-28986 & CVE-2024-28987: Follow-Up: New SolarWinds HotFix Addresses Critical Vulnerabilities in Web Help Desk
On August 21, 2024, SolarWinds released a second hotfix for SolarWinds Web Help Desk (WHD) version 12.8.3. This hotfix addresses a newly disclosed hardcoded credential vulnerability (CVE-2024-28987) that allows a remote, unauthenticated attacker to access internal functionality and modify data. Additionally, the hotfix resolves the Java deserialization remote code execution (RCE) vulnerability (CVE-2024-28986) disclosed the previous week and fixes functionality issues introduced by the first hotfix.
Three trends shaping software supply chain security today
Building software continues to look like an assembly line, with developers pulling resources from across the web to create applications. Although third-party resources have played an essential role in developing software for many years, the way that development teams use these external components looks different today.
CVE-2024-6800: Critical Authentication Bypass Vulnerability Affecting GitHub Enterprise Server
On August 20, 2024, GitHub released security fixes for a critical authentication bypass vulnerability in GitHub Enterprise Server, identified as CVE-2024-6800. GitHub Enterprise Server is a self-hosted version of GitHub, designed for organizations to manage and collaborate on code securely within their own infrastructure. This vulnerability affects instances using SAML single sign-on (SSO) with certain identity providers (IdPs) that publicly expose signed federation metadata XML.
Five Key Findings from the Inaugural EPSS Report
Last month, Cyentia and First.org published the inaugural Exploit Prediction Scoring System (EPSS) performance report. The report goes beyond just assessing the EPSS predictive scoring model. It looks at historical vulnerability data and published CVEs, as well as provides comparisons to the other popular scoring models: CVSS and CISA-KEV.
Navigating the Challenges of CVE Management: Strategies for Effective Vulnerability Management
In today's rapidly evolving cybersecurity landscape, managing Common Vulnerabilities and Exposures (CVEs) is a critical yet increasingly complex task. As organizations scale their digital footprints, the sheer volume and diversity of vulnerabilities they must contend with have grown exponentially. This surge in potential threats, compounded by the sophisticated tactics employed by cyber adversaries, makes CVE management a required but complicated endeavor.
Dcode Capital Makes Investment in Nucleus Security to Solve Critical Cybersecurity Challenges for Federal Organizations
Unified vulnerability management streamlines vulnerability analysis, triage, and remediation.
Threat Context monthly: Executive intelligence briefing for August 2024
Welcome to the Threat Context monthly blog series where we provide a comprehensive roundup of the most relevant cybersecurity news and threat information from KrakenLabs, Outpost24’s cyber Threat Intelligence team. Here’s what you need to know from August.
Challenges in Automating and Scaling Remote Vulnerability Detection
When a new major CVE gets released, cybersecurity companies race to discover ways of detecting the new vulnerability and organizations scramble to determine if they are impacted or not. Developing high-confidence techniques to scan the public-facing Internet assets for newly published vulnerabilities can potentially take weeks or even months as vulnerability researchers discover and test various detection methods.
Enhancing Vulnerability Management with Threat Intelligence
The shift towards a proactive cybersecurity mindset has been steadily gaining momentum. Industry experts have emphasized the importance of best practices for implementation and the role of security orchestration. By integrating modern threat intelligence solutions into vulnerability management platforms, forward-thinking enterprises can become more proactive in their fight against cyber threats.
The Other Crowdstrike Outage
On July 19, 2024, a flawed update in CrowdStrike Falcon's channel file 291 led to a logic error that caused Windows systems to crash, resulting in widespread BSOD (Blue Screen of Death) incidents. The impact was severe, disrupting critical infrastructure globally, from grounded flights to halted public transit systems. In fact, you’d have to have been living under a rock to have missed this incident.
API Leaks: Identifying and Preventing Data Exposure
In this video, we explore the growing concern of API leaks and how they can lead to significant data exposure. Learn about the key strategies for identifying and preventing API leaks to protect your organization’s sensitive information. Our experts provide actionable insights on mitigating risks associated with API vulnerabilities.
How AI Almost Got Me FIRED: Part 2
This AI Code got me fired again?!...Joking! In this video we show you another AI coding tool called Tabnine and see if it can correctly help you in your coding, as well as how to spot and fix any vulnerabilities it generates.
Anatomy Of A Vulnerability: ScreenConnect From Publication To Exploitation
In a security bulletin on February 19, ConnectWise announced critical vulnerabilities (CVE-2024-1708 & CVE-2024-1709) to its on-premises ScreenConnect product (identified and responsibly reported by one of Kroll’s SOC analysts), allowing attackers to takeover an organization’s ScreenConnect. The vulnerability, trivial to exploit, allows anonymous individuals to a create system admin account on publicly exposed instances of the product.
CVE-2024-7646: Ingress-NGINX Annotation Validation Bypass - A Deep Dive
Attention: a new Kubernetes vulnerability was uncovered by André Storfjord Kristiansen (@dev-bio on GitHub) and it demands immediate attention from security professionals and DevOps teams. CVE-2024-7646, affecting the popular ingress-nginx controller, allows malicious actors to bypass annotation validation and potentially gain unauthorized access to sensitive cluster resources. This vulnerability has been assigned a CVSS v3.1 base score of 8.8 (High).
CVE-2024-28986: Critical RCE Vulnerability Impacting SolarWinds Web Help Desk
On August 13, 2024, SolarWinds released a hotfix for CVE-2024-28986, a critical Remote Code Execution (RCE) vulnerability affecting Web Help Desk (WHD). WHD is an IT service management software widely used across various industries for tracking and managing support tickets. This vulnerability arises from a Java deserialization flaw, which could enable a remote attacker to execute arbitrary code on vulnerable hosts.
Unveiling Top API Vulnerabilities and Emerging Trends: Introducing the Wallarm Q2 2024 API ThreatStats Report
As we move through 2024, the Wallarm Research Team continues to monitor the evolving API vulnerability and threat landscape. Our latest Q2 ThreatStats Report reveals critical trends and developments that are reshaping the security environment. Continuing from our Q1 findings, the surge in AI API vulnerabilities is not only persisting but intensifying, with an alarming increase in both the volume and severity of exploits.
Deep Dive and Simulation of a MariaDB RCE Attack: CVE-2021-27928
In early 2021, a new vulnerability, identified as CVE-2021-27928, was discovered and published. It affects multiple versions of the open-source relational database management systems (RDMBS) MariaDB and Percona Server, and the wsrep (write set replication) plugin for MySQL. Fortunately, security professionals swiftly released a patch to ensure that affected systems could be updated to mitigate risks.
Cato CTRL Threat Brief: CVE-2024-38077 - Windows Remote Desktop Licensing Service RCE Vulnerability ("MadLicense")
Recently, CrowSec security researchers published a proof of concept (PoC) for a critical remote code execution (RCE) vulnerability in Windows Server (CVSS score 9.8), ranging all the way from Windows Server 2000 up to 2025. The vulnerable component is the Remote Desktop Licensing service, often deployed and enabled on Windows Servers using Remote Desktop Services. The exploit is a 0-click pre-auth exploitation, meaning no user interaction or authentication details are necessary.
The journey to AppSec gold: Lessons we can learn from the Olympians
The 2024 Olympics are in full swing, and everyone at Snyk is excited to tune into the games and cheer on our respective countries’ athletes. There’s a lot to love about the Olympics — dazzling opening ceremonies, heart-racing feats, close-call victories, and so much more. But along with all the fun and excitement comes a sense of inspiration.
OWASP Mobile Top 10 2024: A Security Guide
The OWASP Mobile Top 10 lists the foremost crucial security risks in mobile applications. This list is essential for developers, security professionals, and organizations to prioritize their resources while addressing mobile app development vulnerabilities in order of severity.
Black Hat 2024 In Review - The Power of Unity
Black Hat 2024 has come and gone. The Nucleus team attending the show has (mostly) caught up on their sleep, which can mean one thing – a look back at the conference and our impressions of the event.
Trustwave Rapid Response: Mitigate Windows TCP/IP RCE Vulnerability (CVE-2024-38063)
Microsoft has disclosed a critical (CVSS 9.8) TCP/IP remote code execution (RCE) vulnerability that impacts all Windows systems utilizing IPv6. To conduct this attack, threat actors can repeatedly send IPv6 packets that include specially crafted packets. By doing this, an unauthenticated attacker could exploit this vulnerability, leading to remote code execution. Systems that have IPv6 disabled are not susceptible to this vulnerability.
CVE-2024-38856 -Apache OFBiz Pre-Auth RCE Vulnerability
A new zero-day vulnerability, CVE-2024-38856, has been discovered in the Apache OFBiz open-source enterprise resource planning (ERP) platform, presenting a critical threat to businesses worldwide. This pre-authentication remote code execution (RCE) flaw allows unauthenticated attackers to exploit weaknesses in OFBiz’s request handling, leading to unauthorized access and potentially damaging control over affected systems.
We Made It! Nucleus Placed 267 on Inc. 5000 Fastest Growing Companies
This week, Nucleus can add another accolade to a growing list, being listed as number 267 on Inc. Magazine’s list of the 5000 fastest-growing companies in America. We are proud of the growth we’ve achieved as a company and the potential for the future at Nucleus. Looking more closely at the results, we are the fourth fastest-growing security company on the list. As many people know, the cybersecurity and technology market has been tumultuous recently.
Vulnerabilities in NodeJS C/C++ add-on extensions
One of the main goals of this research was to explore C/C++ vulnerabilities in the context of NodeJS npm packages. The focus will be on exploring and identifying classic vulnerabilities like Buffer Overflow, Denial of Service (process crash, unchecked types), and Memory Leakages in the context of NodeJS C/C++ addons and modeling relevant sources, sinks, and sanitizers using Snyk Code (see Snyk brings developer-first AppSec approach to C/C++).
InCyber Forum Europe recap: 4 tips from DevSecOps experts
As your organization considers how to shift security left and facilitate shared responsibility for fixing issues, it can be tricky to know where to start. Which tooling will work best with your existing processes? What are the best ways to spread the word about the importance of application security? And once you’ve chosen tools, how do you actually get developers to use them?
Exploited: Ivanti Virtual Traffic Manager (vTM ) (CVE-2024-7593)
This post is based on ongoing security research – the post will continue to be updated as we get additional information… A critical vulnerability has just been announced in Ivanti’s Virtual Traffic Manager (vTM) that allows unauthenticated remote attackers to create administrator users.
Four easy ways to analyze your Java and Kotlin code
Nowadays, the security of your applications is just as important as the functionality they provide. Therefore, analyzing your code for security vulnerabilities is a vital part of maintaining the integrity of your applications and protecting your users' data. As developers, we are at the front lines of this battle. It's our responsibility to ensure that the code we write is not just functional and efficient but also secure.
CSRF simplified: A no-nonsense guide to Cross-Site Request Forgery
Cross-Site Request Forgery (CSRF) is a serious web security vulnerability that allows attackers to exploit active sessions of targeted users to perform privileged actions on their behalf. Depending on the relevancy of the action and the permissions of the targeted user, a successful CSRF attack may result in anything from minor integrity impacts to a complete compromise of the application.
CVE-2024-7593 & CVE-2024-7569: Critical Vulnerabilities Impacting Ivanti Virtual Traffic Manager and Neurons for ITSM
On August 12, 2024, Ivanti announced a critical authentication bypass vulnerability in its Virtual Traffic Manager (vTM), identified as CVE-2024-7593. Ivanti Virtual Traffic Manager (vTM) is a software-based application delivery controller that manages traffic flow to ensure high performance, availability, and security for web applications.
MadLicense CVE-2024-38077 RCE Threatens All Windows Servers
The latest CVE-2024-38077 Remote Code Execution vulnerability (RCE) and coined MadLicense has been rated as absolutely critical with a CVSS 3.1 score of 9.8. The Windows Remote Desktop Licensing (RDL) service has a vulnerability that enables network attacks with low complexity, affecting all versions of Windows Server from 2000 to 2025 (all Windows Servers).
CVE-2024-38428 Wget Vulnerability: All you need to know
On Sunday, June 2nd 2024, a fix commit was pushed for a vulnerability in GNU’s popular Wget tool. Two weeks later, the vulnerability was assigned the ID CVE-2024-38428 and later was classified as a critical vulnerability – with a CVSS score of 9.1. In this blog, we take a dive deep into this threat by seeing what caused it, what consequences it might have, and how it can be mitigated.
Scams: Understanding vulnerabilities and protective strategies
Many people don’t realize that scams are complicated events orchestrated by scammers, which often include myriad persuasive techniques and take advantage of our individual characteristics and circumstances. While each scam varies in complexity, they typically progress through three broad stages, each influenced by factors that either heighten or diminish our vulnerability to becoming victims.
How AI Almost Got Me FIRED: Part 1
This AI code got me fired!!...Not really! But in this video we show you how AI coding tools like Codeium can greatly help accelerate coding , but how they also come with some downfalls and how you can spot them.
Supercharge domain discovery with AI-powered External Attack Surface Management (EASM)
Modern organizations have sprawling attacks surfaces of known and unknown assets that grow each day. This means understanding and managing your external attack surface is more crucial than ever. But with the vast number of digital assets that organizations need to monitor, accurately identifying every component of your attack surface can seem overwhelming – which is why many turn to External Attack Surface Management (EASM).
Key Aspects of a Successful Remediation Plan | Seemplicity
Kevin Swan, Senior Product Marketing Manager at Seemplicity, dives deep into the essential components of a successful remediation plan. Learn how to transform vulnerability management chaos into scalable remediation plans by focusing on four critical areas: identifying what needs to be remediated, locating vulnerable assets, assigning responsible teams, and implementing effective remediation strategies.
Using GitHub Copilot Chat to Write Secure Code
Watch the full video for more...
Non human Identities - Permissions, Third Party Vulnerabilities and Risk
Non-human identities (NHIs) dominate the era of cloud services and SaaS applications. They are the identities that authenticate between different servers, APIs and third party integrations to provide programmatic access to data and services. Non-human identities utilize different protocols, such as OAuth, REST and SSH.
A security expert's view on Gartner's generative AI insights - Part 2
Welcome to the second part of our two-part special on Gartner’s “4 Ways Generative AI Will Impact CISOs and Their Teams” report! If you’ve missed the first part on model composition, you can read it here. Today, we will explore why security specialism matters in an AI security tool, particularly where AI quality is concerned.
Windows Downdate: Downgrade Attacks Using Windows Updates
Downgrade attacks—also known as version-rollback attacks—are a type of attack designed to revert an immune, fully up-to-date software back to an older version. They allow malicious actors to expose and exploit previously fixed/patched vulnerabilities to compromise systems and gain unauthorized access.
Asset and Inventory Management - The Foundation of the Vulnerability Management Lifecycle
Organizations face a myriad of cybersecurity threats that can compromise sensitive data and disrupt operations. A cornerstone of defending against these threats is an effective vulnerability management program. This program’s first, and arguably most critical, step is strong asset and inventory management. A thorough and accurate asset inventory is essential for identifying and mitigating vulnerabilities.
A security expert's view on Gartner's generative AI insights
Snyk’s goal has always been to empower developers to build fast but safely. This is why we created the developer security category and why we were amongst the first advocates of “shifting left.” Now, AI has changed the equation. According to Gartner, over 80% of enterprises will have used generative AI APIs or models, or deployed their own AI model, by 2026.
Samsung Introduces Million-Dollar Bug Bounty for Critical Galaxy Vulnerabilities
Samsung has introduced a groundbreaking bug bounty program offering up to $1,000,000 for discovering critical vulnerabilities in its mobile devices. This initiative, named the 'Important Scenario Vulnerability Program (ISVP),' underscores Samsung's commitment to bolstering the security of its Galaxy devices. The program focuses on vulnerabilities related to arbitrary code execution, device unlocking, data extraction, arbitrary application installation, and bypassing device protections.
Tech Analysis: Addressing Claims About Falcon Sensor Vulnerability
CrowdStrike is aware of inaccurate reporting and false claims about the security of the Falcon sensor. This blog sets the record straight by providing customers with accurate technical information about the Falcon sensor and any claims regarding the Channel File 291 incident. CrowdStrike has provided a Technical Root Cause Analysis and executive summary that describes the bug in detail.
Application vulnerability management best practices
Over the years, application vulnerability management has been vital to DevSecOps — which emphasizes shared security responsibility across teams. However, as development practices have evolved, security teams must learn how to adapt and meet developers within their existing workflows. For example, containerization, infrastructure as code (IaC) AI coding assistants, and increased reliance on third-party code are all commonplace in the typical development lifecycle.
Extend the power of your AppSec data with the new Snyk and Snowflake integration
We are thrilled to announce the new Snyk Analytics for Snowflake, allowing Snyk customers to seamlessly access and analyze Snyk’s data from their Snowflake account.
Mastering Best Practices for Vulnerability Management
Understanding vulnerability management is crucial for maintaining the security of your systems. It involves identifying, assessing, and mitigating vulnerabilities that exist within your network, applications, and infrastructure. By gaining a deep understanding of vulnerability management, you can effectively prioritize and address security risks. One key aspect of vulnerability management is conducting regular vulnerability assessments.
Trustwave Managed Vulnerability Scanning Shines a Light on Vulnerabilities
The digital landscape constantly shifts, presenting exciting opportunities and lurking threats for businesses of all sizes. In this ever-evolving environment, maintaining a secure network is no longer a luxury; it's a necessity. However, achieving true security requires more than just firewalls and antivirus software. It demands a comprehensive understanding of your network's vulnerabilities – the chinks in your digital armor that attackers could exploit.
LLM Security: Splunk & OWASP Top 10 for LLM-based Applications
As a small kid, I remember watching flying monkeys, talking lions, and houses landing on evil witches in the film The Wizard of Oz and thinking how amazing it was. Once the curtain pulled back, exposing the wizard as a smart but ordinary person, I felt slightly let down. The recent explosion of AI, and more specifically, large language models (LLMs), feels similar. On the surface, they look like magic, but behind the curtain, LLMs are just complex systems created by humans.
Firmware Vulnerabilities Run Rampant in Cellular Routers
The current state of OT/IOT security is being repainted with a new coat of risk. The shade of color? Cellular routers and the vulnerabilities within firmware. In our new report with Finite State, our joint research explores the risks organizations face within the software supply chains of OT/IoT routers. Hardware has firmware – operational software – within its memory components.
Efficient Vulnerability Management with Limited Resources
The role of vulnerability management has never been more critical, especially as professionals in the field face the daunting task of securing entire organizations with minimal budget and headcount.
5 Snyk Alternatives and Why They Are Better
Snyk is widely recognized as one of the top security tools for developers, especially when it comes to finding vulnerabilities in open-source code, containers, and infrastructure as code. However, no tool is perfect for every scenario and access to the Snyk platform comes with a price tag. Depending on your needs, there may be Snyk alternatives that provide better integration, features, or just better value for money.
More Ways GitHub Copilot Makes You Vulnerable
Do these suggestions still give us vulnerable code? Or do they make our code less vulnerable? Today we are putting this to the test.
Infosec Europe session: 4 tips for safer AI adoption
AI adoption continues to move at a breakneck speed for businesses across the globe, as shown in a Coatue report comparing AI adoption to early internet adoption and found that AI growth is happening at two times the speed of the former.
Introducing new Snyk AppRisk integrations: Enhancing application risk management with development context
In the fast-paced world of modern software development, grasping the full scope of an application is essential for managing an application security program. This entails having visibility into all the application assets involved in building the app, knowing their ownership, and understanding their importance to the development process and the broader business.
CVE-2024-4879 & CVE-2024-5217 Exposed - The Risks of RCE in ServiceNow
Recent critical vulnerabilities in ServiceNow, a widely used cloud platform, have put numerous organizations at risk of data breaches. Threat actors are exploiting these input validation flaws, enabling remote code execution and unauthorized access. Despite recent fixes, government agencies, data centers, and private firms remain targeted. This blog highlights how these flaws are exploited for data theft and outlines security measures to mitigate these risks.
Hotjar's OAuth+XSS Flaw Exposes Millions at Risk of Account Takeover
A critical flaw in Hotjar that combines XSS with OAuth putting millions of websites at risk, exposing user data and risking account takeovers. Hotjar, a trusted product experience insights platform used by over a million websites, including global brands like Adobe and Microsoft, offers powerful behavior analytics and feedback tools. These include Heatmaps, Recordings, Surveys, and Feedback, which help product teams understand user behavior and improve user experience (UX).
How to tell if your organization's credentials have been involved in a breach
Stolen credentials are the easiest route into your organization for a hacker. Verizon’s 2023 Data Breach Investigation Report found that threat actors used stolen credentials in 49% of attempts to gain unauthorized access to organizations. The problem IT teams face is knowing when credentials have been stolen or leaked in a breach – otherwise you’re waiting to respond to a security issue rather than handling it proactively.
Triaging Non-CVE Vulnerabilities with Nucleus
Join Scott Kuffer, Co-Founder of Nucleus Security, in this webinar, focused on effective vulnerability management. Dive deep into the complexities of managing non-CVE based vulnerabilities. Learn about centralized vs. distributed remediation strategies and gain practical tips on triaging, prioritizing, and responding to vulnerabilities. This webinar emphasizes the importance of a unified approach to vulnerability management, leveraging threat modeling, and re-evaluating risk assessment methodologies to protect your business.
Highlights of The 2024 Remediation Operations Report
As digital threats grow increasingly sophisticated, organizations must stay ahead by adopting advanced strategies to manage and mitigate vulnerabilities. This necessity has driven significant changes in how remediation operations are conducted, emphasizing the importance of continuous improvement and innovation. Seemplicity’s 2024 Remediation Operations Report revealed several key trends and practices that are shaping the future of remediation operations.