Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
December 2023
Navigating the Digital Frontier: The Evolution of Cyber Vulnerabilities in Credit Unions
How vulnerable are credit unions, the bedrock of community finance, to rapidly advancing cyber threats? CISO Global understands that credit unions’ member-owned and not-for-profit structure allows their banking counterparts to outpace them in allocating resources for cyber defenses. While credit unions are deeply committed to protecting member data, their budgetary constraints might limit their ability to invest in the most advanced cybersecurity technologies and staff.
2023 Kubernetes vulnerabilities roundup
How to prevent open redirect vulnerabilities in Laravel
An open redirect vulnerability occurs when a website allows user-supplied input to influence the destination of a redirect without implementing proper validation or sanitization measures. To exploit this vulnerability, an attacker may send users a seemingly trustworthy link, which, when clicked, redirects them to a harmful website, potentially leading to phishing attacks or other malicious activities.
Common Types of Cybersecurity Vulnerabilities
Common cybersecurity vulnerabilities that cybercriminals can exploit include weak credentials, lack of data encryption, misconfigurations, out-of-date software and zero days. These vulnerabilities often lead to cyber attacks that bypass an organization’s security measures and steal confidential data. Organizations need to identify and mitigate these vulnerabilities to prevent security breaches.
Welltok's MOVEit Breach Continues; Another 2 Million Records Harvested
Welltok provides a multi-use platform allowing institutions and individuals to manage their health and well-being. It is a third-party solution that caters to clinics, health networks, industry leaders, and private clinics. They also offer personalized resources and solutions meant to improve the health and lives of applicable patients.
SSH protocol flaw - Terrapin Attack CVE-2023-48795: All you need to know
The SSH Terrapin attack (CVE-2023-48795) has recently caught attention, targeting the SSH protocol security by truncating cryptographic information. The inherent flaw in the SSH protocol itself affects a wide range of SSH client and server implementations. Following our initial research communication, this post will detail its fundamentals and impact.
Hunting for Android Privilege Escalation with a 32 Line Fuzzer
Trustwave SpiderLabs tested a couple of Android OS-based mobile devices to conduct the research on privilege escalation scenarios. Specifically, we wanted to show a straightforward process attackers may use to exploit vulnerabilities in an Android device’s system services and systems. The testing revealed that, in some cases, exploiting the issues we found were very easy.
CVE-2023-41727, CVE-2023-46220, CVE-2023-46261, and More: Multiple Critical Vulnerabilities Patched in Ivanti Avalanche
Xfinity Writhes; 36 Million Records Breached via Vendor Vulnerability
Xfinity is the name of Comcast Communications’ internet, TV, and phone service; it is the most significant cabled internet service in the states, with more than 32 million residential customers. Available in 39 contiguous states and the capital, the service provides communication solutions for individuals, companies, institutions, and clinical networks. Xfinity’s vast influence has made them a target for cybercriminals.
Apache Struts 2 Vulnerability CVE-2023-50164 Exposed
Vulnerability Remediation for Servers: Beyond Just Patching
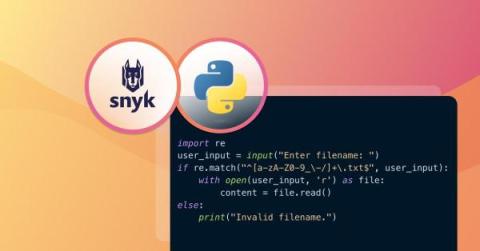
Command injection in Python: examples and prevention
Despite Python's reputation for simplicity and versatility, ensuring the security of Python programs can be challenging if you or other team members neglect security best practices during development. Additionally, you’ll likely use libraries or other open source projects while building a Python application. However, these resources can introduce additional security issues that leave your program vulnerable to exploits such as command injection.
How to Operationalize Vulnerability Threat Intelligence
Is your team on the *security* naughty or nice list?
As kids, many of us felt anticipation, excitement, and maybe even nervousness during the holiday season. Had we been good enough to get the Gameboy, Barbie Dream House, or Etch a Sketch we’d been pining for, or were we just going to get a big ol’ lump of coal?
Release Spotlight: Qualys PCS
Under the hood of CVE patching
Microsoft Copilot Studio Vulnerabilities: Explained
The best Cybersecurity conference you never heard of
For the past 12 years in Austin, TX, the last week of October has been reserved for the Lonestar Application Security Conference (LASCON). Unequivocally, LASCON is the best cybersecurity conference you have never heard of! LASCON is the annual confab of the Austin, TX OWASP (the Open Worldwide Application Security Project) chapter. OWASP is a volunteer organization that is a treasure trove of application security information with things such as standards, discussion groups, documentation, and more.
Vulnerability disclosure: Which comes first, the security bug in PHP or the CVE?
For security researchers, there is a series of hurdles in raising a potential vulnerability well before the issue itself is widely recognized. Convincing the project maintainers that there is an issue becomes the first hurdle, even with a working example. At times, there is a thin and fuzzy line to a vulnerable path being identified as a bug rather than a security vulnerability.
Common SAML vulnerabilities and how to remediate them
Security Assertion Markup Language (SAML) is an XML-based framework that plays a pivotal role in enabling secure identity and access management. It acts as a trusted intermediary between various entities in a digital ecosystem, such as identity providers, service providers, and users. The primary purpose of SAML is to facilitate single sign-on (SSO), a seamless and efficient authentication process where a user can access multiple applications and services using a single set of credentials.
MOVEit Claims 7 Million More; Patients of Delta Dental of California and Others
Delta Dental of California (DDC), Delta Dental Insurance Company, Delta Dental of Pennsylvania, and other subsidiaries may have exposed data; the compromised data is not a product of the organizations. Instead, the breach stems from a third-party servicer specializing in file management and transferring tools—MOVEit.
CVE-2023-50164: Public PoC Leveraged to Exploit Critical RCE Vulnerability in Apache Struts
Snyk named as a top cybersecurity company in inaugural Fortune Cyber 60 2023 list
We’re proud that Snyk has been honored with inclusion on the inaugural Fortune Cyber 60 list as a top growth-stage company. The full list was unveiled late last week. In 2023, our industry encountered distinctive challenges, but the entire Snyk community demonstrated resilience and a steadfast commitment to our founding mission: empowering and equipping DevSecOps teams worldwide to build securely.
Understanding the Zimbra Cross-Site Scripting Flaw (CVE-2023-37580)
Conversations with Charlotte AI: "What is my exposure to vulnerabilities used by Scattered Spider?"
Top 3 security best practices for handling JWTs
In modern web development, JSON Web Tokens (JWTs) have become a popular method of securely transmitting information between parties. JWTs are used for authentication and authorization and are often used to store user information. However, with the increasing use of JWTs come potential security risks that developers need to be aware of. As a developer, you are responsible for ensuring that your application is secure and user data is protected.
Apache Struts 2 Remote Code Execution (CVE-2023-50164) - Cato's Analysis and Mitigation
By Vadim Freger, Dolev Moshe Attiya On December 7th, 2023, the Apache Struts project disclosed a critical vulnerability (CVSS score 9.8) in its Struts 2 open-source web framework. The vulnerability resides in the flawed file upload logic and allows attackers to manipulate upload parameters, resulting in arbitrary file upload and code execution under certain conditions. There is no known workaround, and the only solution is to upgrade to the latest versions, the affected versions being.
CVE-2023-50164: Remote Code Execution Vulnerability Discovered in Apache Struts
Apache has released an advisory for a critical vulnerability discovered in Struts versions 2.0.0-2.3.37(EOL), 6.0.0-6.3.0.1 and 2.0.0-2.5.32. This vulnerability is being tracked as CVE-2023-50164 with a CVSS score of 9.8 (Critical) and is reportedly being actively exploited. Impacted versions are affected by a file upload and directory traversal vulnerability that can lead to remote code execution.
Enhancing code to cloud security with the Common Configuration Scoring System
Proprietary severity scoring often burdens AppSec teams. With every new vendor, you must evaluate their custom severity framework and work to translate assessed risk between tools. To eliminate this burden and provide our customers with a clear security assessment for configurations across the SDLC, Snyk will be moving towards standardizing our code to cloud security rules set on the Common Configuration Scoring System (CCSS)!
Threat Exposure Management for the Expanding Attack Surface
Snyk highlights AWS re:Invent 2023
With over 50,000 in attendance, AWS re:Invent 2023 had generative AI taking center stage at keynotes, race cars, and robots wowing at the Expo. Once again, Snyk showed up in a big way. Some of our highlights included being awarded the AWS ISV Partner of the Year in EMEA and UKI, achieving AWS Security Competency, and several new integrations with AWS services. Best of all, we got to meet all of you!
What is Vulnerability Assessment?
Each day there are more and more cyber attacks and threats occurring, with those looking to exploit your IT systems finding various different methods to infiltrate your IT infrastructure. This means it's more vital than ever that you limit the vulnerabilities of your IT infrastructure and guarantee its security. In regards to this, a viable solution available to you is vulnerability assessment.
JetBrains TeamCity Vulnerability Exploit: SafeBreach Coverage for US-CERT Alert (AA23-347A)
On December 13th, The U.S. Federal Bureau of Investigation (FBI), U.S. Cybersecurity & Infrastructure Security Agency (CISA), U.S. National Security Agency (NSA), Polish Military Counterintelligence Service (SKW), CERT Polska (CERT.PL), and the UK’s National Cyber Security Centre (NCSC) have issued an urgent advisory about the ongoing exploit of CVE-2023-42793 by Russian Foreign Intelligence Service (SVR) threat actors.
A New Way to View Vulnerabilities: Improving Your Workflow
We are thrilled to announce the introduction of our new vulnerabilities page on assessments. This innovative update allows you to view the overall status and remediation progress of all your assets for a single assessment in one comprehensive view. We've listened to your feedback, and we believe these enhancements will bring a more streamlined and efficient approach to your vulnerability management.
Three reasons to invest in an ASPM solution in 2024
The pace of software development is astounding! The transition to agile, DevOps, cloud, and the supercharged use of AI is empowering distributed development teams to build software with greater speed and autonomy. In contrast to the remarkable strides in development methodologies, maintaining a robust security posture has become a formidable challenge. AppSec teams are still playing catchup, both outnumbered and out-resourced.
Announcing Snyk AppRisk: Elevate your AppSec game with ASPM
Snyk AppRisk provides AppSec teams with the comprehensive application security posture management (ASPM) workbench they need to govern and scale their security programs as well as minimize risk arising from applications.
Introducing Snyk AppRisk Essentials
ISO/IEC 27001 compliance guide for CISOs and IT Managers
Building trust with customers often starts by demonstrating the right security controls. In the digital age, data security is paramount, and adherence to standards like ISO/IEC 27001, PCI DSS, and SOC 2 has become a key differentiator in the competitive market landscape.
Snyk recognized as an Emerging Segment Leader in Application Security in Snowflake's Next Generation of Cybersecurity Applications report
We are thrilled to announce that Snyk has been acknowledged as a key player in the evolving landscape of application security. The recent release of Snowflake's Next Generation of Cybersecurity Applications report has designated Snyk as an Emerging Segment Leader in Application Security, highlighting our commitment to innovation and excellence in the field.
CVE-2023-36553: Critical OS Command Injection Vulnerability in FortiSIEM
Weekly Cybersecurity Recap December 8
This week’s data breaches contained significant impact figures from around the world. Malware on a vendor’s computer inadvertently breached Japan’s Line Messenger. New York’s East River Medical Imaging suffered the loss of employee and patient record information. The Pan-American Life Insurance Group faces a 105k record data breach through MOVEit.
Demystifying CVSS Scoring
CrowdStrike Discovers Vulnerability in Flexera's FlexNet Inventory Agent (CVE-2023-29082)
CrowdStrike’s cloud security team discovered a new vulnerability (CVE-2023-29082) in Flexera’s FlexNet Inventory Agent. When exploited, an attacker can escape from a container and gain root access to the host. Exploitation of CVE-2023-29082 can allow an attacker to perform a variety of actions on objectives, including execution of malware and exfiltration of data.
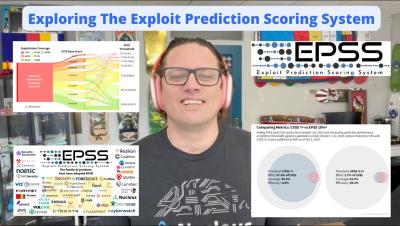
What is Exploit Prediction Scoring System (EPSS)?
State of Log4j Vulnerabilities: How Much Did Log4Shell Change?
December 9 marks two years since the world went on high alert because of what was deemed one of the most critical zero-day vulnerabilities ever: Log4Shell. The vulnerability that carried the highest possible severity rating (10.0) was in Apache Log4j, an ubiquitous Java logging framework that Veracode estimated at the time was used in 88 percent of organizations.
SEC Allegations: SolarWinds CISO Aware of Cyber Risks Who Should Fix Vulnerabilities? #podcast
How Malicious Insiders Use Known Vulnerabilities Against Their Organizations
We are well aware of the devastating effect insiders can have when using their legitimate access and knowledge to target their own organization. These incidents can result in significant monetary and reputational damages. Entities small and large, across all sectors, can fall victim to insider threats.
Atlassian Releases Four Critical Patches to Prevent RCE
CVE-2023-22523, CVE-2022-1471, CVE-2023-22524, and CVE-2023-22522: Four Critical RCE Vulnerabilities Impacting Multiple Atlassian Products
CVE-2023-49103, CVE-2023-49104, and CVE-2023-49105: Multiple Critical Vulnerabilities in ownCloud
Adobe ColdFusion Vulnerability: SafeBreach Coverage for US-CERT Alert (AA23-339A)
On December 5th, the Cybersecurity and Infrastructure Security Agency (CISA) released an advisory that confirmed the exploitation of CVE-2023-26360 at a Federal Civilian Executive Branch (FCEB) agency by unknown threat actors. Exploiting this vulnerability allowed threat actors to gain access to the FCEB agency network on two separate occasions in June 2023.
Request smuggling and HTTP/2 downgrading: exploit walkthrough
During a recent penetration test on a customer application, I noticed weird interactions between the web front-end and back-end. This would eventually turn out to be a vulnerability called HTTP request smuggling, enabled by the fact that the front-end was configured to downgrade HTTP/2 requests to HTTP/1.1. With the help from my colleague Thomas Stacey, we were able to construct an exploit chain with response queue desynchronization along with traditional HTTP/1.1 request smuggling techniques.
Code injection in Python: examples and prevention
As software becomes increasingly integral to our professional and personal lives, the need to protect information and systems from malicious attacks grows proportionately. One of the critical threats that Python developers must grapple with is the risk of code injection, a sophisticated and often devastating form of cyberattack.
CVE-2023-41998, CVE-2023-41999, and CVE-2023-42000: Multiple Arcserve UDP Vulnerabilities Patched
Accelerate C/ C++ security with Snyk
Securing C/C++ applications has been a massive challenge historically. Until today, many organizations using C/C++ have had to rely on a niche, single-language tool that, while decent at finding vulnerabilities, requires code to be compiled before scanning, slows down developers with clunky integrations, and provides vulnerability alerts that do not help developers to remediate the issue.
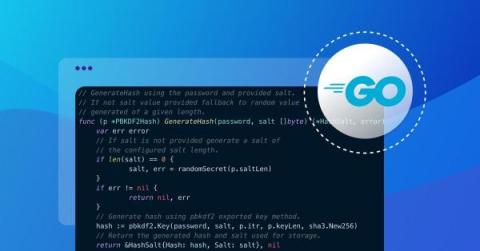
Secure password hashing in Go
User credentials are the information required to authenticate a user's identity and grant them access to a system or application. Typically, this includes a username or email address and a password. While a username can be stored as plaintext in a database, sensitive information like email addresses or passwords should not. If a malicious actor gains access to your database where you store this information, you don't want to hand over this information to them easily.
Forescout Vedere Labs discloses 21 new vulnerabilities affecting OT/IoT routers
Research Into IoCs Linked to Exploitation of CVE-2023-47246
The SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team has conducted further research into the indicators of compromise (IoCs) that SysAid shared when disclosing a new vulnerability in its on-premise software last month.
Snyk named a 2023 Gartner Peer Insights Customers' Choice for Application Security Testing
Snyk, the leader in developer security, is excited to share that we’ve been named Customers’ Choice in the 2023 Gartner Peer Insights Voice of the Customer for Application Security Testing for a second consecutive year. Gartner defines the Application Security Testing category as products and services designed to analyze and test applications for security vulnerabilities. This distinction is based on meeting or exceeding user interest, adoption, and overall experience.
Manifest V3 Essentials: Chrome Extension Tips!
Open Source Vulnerability Management Recommendations for 2024
Stepping in 2024, the dynamics of open source vulnerability management are shifting. Rapid changes to software development demand a more nuanced approach to open source security from practitioners. From redefining risk to the cautious integration of auto-remediation, here are the pivotal recommendations for successful open source vulnerability management in 2024 and beyond.
Achieving developer security adoption at Nylas with Snyk
Effective security programs promote collaboration between developers and security teams. Many organizations aim for a seamless developer experience that allows security teams to build guardrails directly into dev workflows, breaking down silos, and promoting collaboration between these departments.
Preventing Broken Access Control Vulnerabilities in Web Applications
Access control is crucial for modern web development as it enables the management of how users, processes, and devices should be granted permissions to application functions and resources. Access control mechanisms also determine the level of access permitted and manifest activities carried out by specific entities. Broken access control vulnerabilities arise when a malicious user abuses the constraints on the actions they are allowed to perform or the objects they can access.