New OpenSSL critical vulnerability: What you need to know
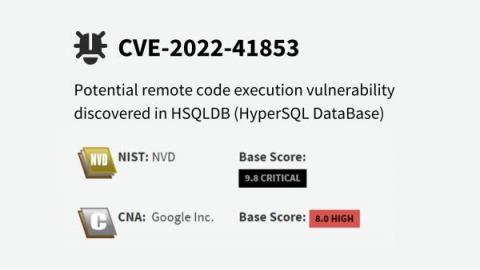
On Oct 25, 2022 The OpenSSL project announced a forthcoming release of OpenSSL (version 3.0.7) to address a critical security vulnerability. This release should go live on Tuesday, November 1, 2022 between 1300 and 1700 UTC. Snyk has published a placeholder advisory with the current known details, and will update the advisory when official vulnerability details are publicized. The last critical vulnerability in OpenSSL was released in 2016.