Securing a New Way of Working: You Gotta Love the CVEs
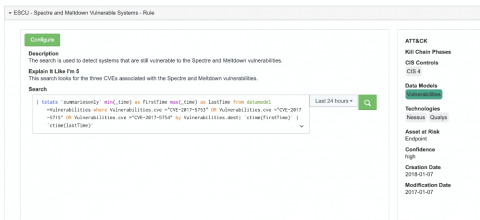
Right, so now the vast majority of your workforce works remotely. Clearly managing all these inbound VPN connections is on top of mind, but what about other vulnerabilities you should be monitoring for? In addition to the ever increasing number of inbound VPN connections, organizations can expect an increase in the use of SaaS-based collaborative software such as Slack, Dropbox, G Suite, and Trello.