Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevSecOps
Bringing Immutable Audit Trails to Dropbox
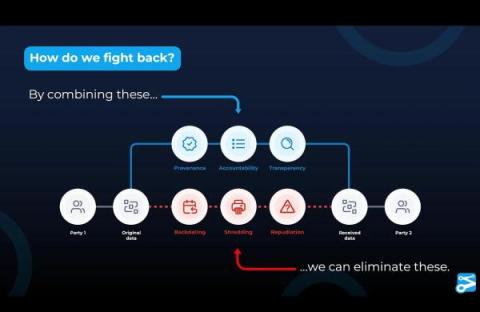
In the age of Gen AI, it is now apparent that we can no longer trust what we see and read. The fakers have the upper hand: while typical security approaches rely on scaling up teams, attacks scale at the press of a button. To safely move forward and realize the benefits Gen AI enables, we need a better trust model that adds integrity, transparency and trust to all data and a common provenance format that captures origin, authenticity and lineage information. We must verify data before we use it.
A DevSecOps solution for your apps on AWS from Snyk
AWS offers the infrastructure, innovation, services, and reliability to run your mission-critical applications, which is why millions of customers partner with AWS to build, run, and scale applications in the cloud. But how can customers proactively ensure the security of these critical applications?
Detect Fakes and Prevent Misuse: Digital Content Integrity, Authenticity & Transparency
As supply chains continue to evolve and new Al technology becomes part of every business, traditional trust systems that rely on human interactions to verify and validate data will struggle to keep pace. Digital supply chain practices from media through software to physical goods must adapt to this changing global technology landscape. The innovations unleashed in GenAI have made it apparent that we can no longer trust what we see and read; we must verify data before we use it.
Secure by Default: Integrating GitGuardian in Vermeer's Software Development Lifecycle
Discover how Vermeer Corporation transformed its software development lifecycle to prioritize security. Learn about their journey from open-source tools to adopting GitGuardian for seamless, integrated secret scanning, enhancing DevSecOps with a 'Secure by Default' approach.
DevSecOps Best Practices: Leveraging Veracode DAST Essentials
DevSecOps is a modern approach to software development that implements security as a shared responsibility throughout application development, deployment, and operations. As an extension of DevOps principles, DevSecOps helps your organization integrate security testing throughout the software development life cycle. In this blog, we discuss DevSecOps best practices and practical steps to producing secure software.
Build Audit Trails With Dropbox and DataTrails
DataTrails enables compliance and audit teams to eliminate the time-wasting and error-prone processes with our new solution. With the introduction of our Dropbox connector, there is a no-code solution that provides notarized evidence of your file’s metadata. Now you can capture legally admissible proof for your business with just a few clicks. To get started, set-up a free DataTrails account and connect it to Dropbox by following these instructions.
RKVST is now DataTrails!
We’ve listened, we’ve learned, and the market has definitely spoken! Our old name just wasn’t working: it was hard to pronounce, hard to spell, and hard to understand what we do. Even if the ‘archivist’ leap was made it didn’t carry our special mission with it.
RKVST is now DataTrails! #shorts
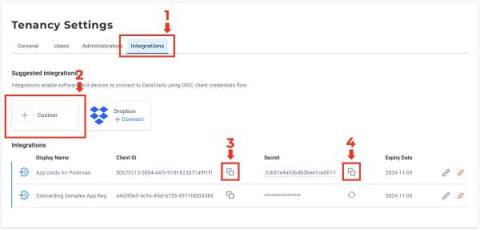
Postman Configuration for DataTrails
One of my favourite tools for playing with REST APIs is, of course, Postman. It can make interacting with DataTrails super quick and easy, and help you develop custom workflows for storing and validating your digital provenance and audit trails. Here’s a step-by-step guide to getting a robust Postman set-up configured, and if you head over the Postman public collections you’ll find a link to a pre-baked DataTrails Postman collection with this done for you, along with some example requests.