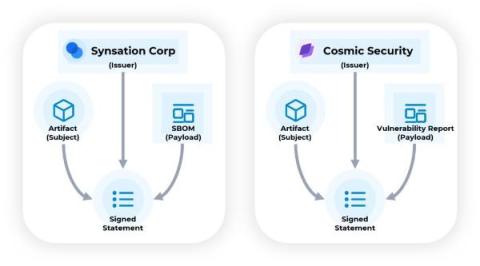
Creating DataTrails for Supply Chain Artifacts
In a world where software is produced, distributed, and re-distributed, how do you ensure the software you consume is authentic and safe for your environment? How do you know the software you deployed yesterday is safe today? Most software exploits are discovered after the software has been deployed, which raises the question: It’s not just about getting software updates, as the majority of exploits are distributed as updates. Staying updated isn’t the most secure.