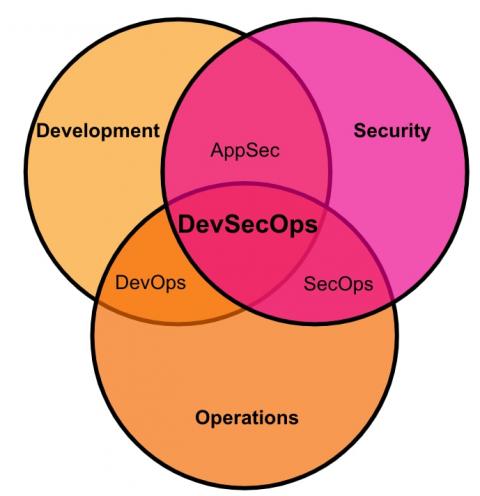
DevSecOps: The What, Why, Who, and How
By way of a brief introduction, I have had a 25+ year career in technology, and this has come with some wonderful experiences and opportunities along the way. One constant throughout my journey has been a need to increasingly leverage data, enabling informed decisions (even automated) at all levels to ensure: secure, high performing and observable products and services are available to the customers and partners I’ve been supporting.