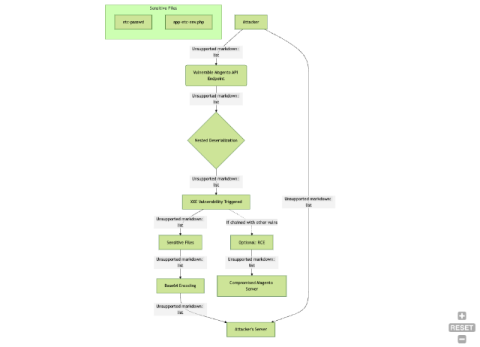
Access your data with Federated Analytics for Amazon Security Lake with Splunk, AWS, and Accenture
Federated Analytics gives organizations the full power of Splunk extended to data stored in Amazon Security Lake. Trusted partners like Accenture are helping bring these new capabilities to life at organizations around the world.