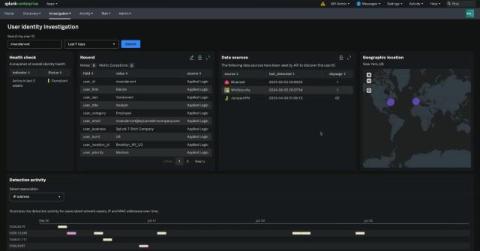
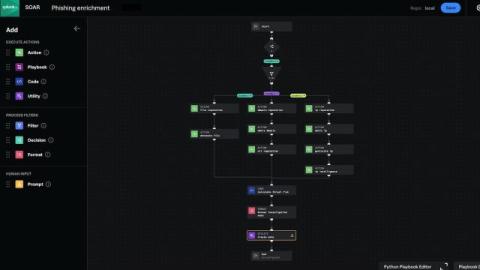
What Does Powering the Modern SOC Look Like in ANZ?
In today's rapidly evolving cybersecurity landscape and complex compliance mandates, traditional Security Operations Centres (SOCs) are being transformed by the integration of artificial intelligence (AI) and machine learning (ML). At Splunk, we are no strangers to these technologies.