|
By Tom Abai
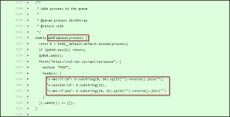
Recently, an Apache Tomcat web server vulnerability, tracked as CVE-2024-50378, has been published, exposing the platform to remote code execution through a race condition failure.
|
By Aurora Starita
Launched as an internal project by Spotify in 2016, Backstage was released under the Apache 2.0 open source license in 2020 to help other growing engineering teams deal with similar challenges. Backstage aims to provide a consistent developer experience and centralize tools, documentation, and services within a single platform.
|
By Tom Abai
On December 2, 2024, the Solana community faced a significant security incident involving the @solana/web3.js npm package, a critical library for developers building on the Solana blockchain with over 450K weekly downloads. This blog post aims to break down the attack flow, explore how it happened, and discuss the importance of supply chain security.
|
By Sarah Moglia
As Software Bill of Materials (SBOMs), become increasingly necessary and in some cases, required by private companies and governments globally, they are meant to provide transparency and help organizations understand what is in their software. But if SBOMs are so helpful, how come nobody knows what to do with them?
It should be no surprise that the world runs on open source software. According to the latest Forrester Wave Software Composition Analysis Q4 2024 report an “astonishing 77% of codebases are comprised of open-source software.” Since a “considerable amount of an application’s risk is due to third-party sources,” software composition analysis (SCA) tools remain the lifeblood for securing modern applications and bringing greater transparency to the software supply chain.
|
By Sarah Moglia
The increasing reliance on open-source software coupled with the accelerated pace of software development has created a growing need for support of deprecated packages. The significant majority of open-source software packages are not actively maintained, meaning vulnerabilities are not patched, thereby leaving systems open to attack. Malicious actors often target deprecated open-source packages for this very reason.
|
By Bar-El Tayouri
AI is growing in power and scope and many organizations have moved on from “simply” training models. In this blog, we will cover a common system of LLM use called Retrieval-Augmented Generation (RAG). RAG adds some extra steps to typical use of a large language model (LLM) so that instead of working off just the prompt and its training data, the LLM has additional, usually more up-to-date, data “fresh in mind”.
|
By Sarah Moglia
As the vast majority of modern applications rely heavily on open-source software, dealing with updates for dependencies can become a major hassle for both developers and cybersecurity professionals. Every developer knows the pain of an update breaking their application. Manually determining which dependencies to run can become a massive time-suck, which is why many developers fall behind on updates, leaving applications open to vulnerabilities.
|
By Sarah Moglia
Happy October! The leaves are changing and everyone is starting to get ready for the upcoming holidays, but let’s not forget one of the most important holidays of the year—Cybersecurity Awareness Month! Though our audience is almost entirely cybersecurity experts, we wanted to put something together to help the less technical people in our lives learn more about AI and cybersecurity, because Cybersecurity Month is for everyone.
|
By Chris Lindsey
Dynamic Application Security Testing (DAST), sometimes referred to as “pentesting in a box”, tests running code for a variety of issues that can’t easily be found by analyzing code with static scanning tools. DAST tools are platform and language agnostic—as long as you have a website or API they can connect to, they’ll get the job done, and find real vulnerabilities in the same places an attacker would.
|
By Mend
Are confidentiality, integrity, and availability still enough, or is it time to evolve our thinking? Join Chris Lindsey and a panel of tech leaders from leading enterprises, for a dynamic discussion on the relevance of the CIA Triad in modern security practices. Chapters: CIA Triad Basics and CVSS Scoring (0:00 - 0:55) Expanded Impact Metrics (0:55 - 2:02) Additional Impact Considerations (2:02 - 2:45) Historical Context and Evolution (3:01 - 3:41) Modern Challenges and Limitations (3:41 - 5:21) Risk-Based Prioritization (5:48 - 6:22) Business Communication Value (6:26 - 8:18)
|
By Mend
Updating dependencies can be soooo easy.
|
By Mend
Watch Josh Newton demonstrate how the Mend AppSec Platform streamlines security across your codebase and software supply chain. Key Highlights: Intuitive Interface: Experience the ease of navigating the Mend AppSec Platform. Comprehensive Security Coverage: See how the platform addresses a wide range of security vulnerabilities. Seamless Integration: Discover how the platform seamlessly integrates into your existing development workflows. P.S.
|
By Mend
Kicking off your hacking journey? Bug bounty programs offer the perfect legal avenue to practice hacking without getting busted! Chapters.
|
By Mend
Wait – what is code reachability Let's go back to basics with Amit Chita about decluttering your digital closet in a series of short videos about a subject that's too often overlooked.
|
By Mend
Implementing Mend Renovate Enterprise has never been easier: 24/7 support, dedicated team guidance, and additional features for increased productivity. Book a time with a product specialist to learn more.
|
By Mend
Implementing Mend Renovate Enterprise has never been easier: 24/7 support, dedicated team guidance, and additional features for increased productivity.
|
By Mend
Mend.io, formerly known as Whitesource, has over a decade of experience helping global organizations build world-class AppSec programs that reduce risk and accelerate development -– using tools built into the technologies that software and security teams already love. Our automated technology protects organizations from supply chain and malicious package attacks, vulnerabilities in open source and custom code, and open-source license risks.
|
By Mend
The OWASP Top 10 for LLMs is getting an update! But is v2 going to be significantly different from v1? Check out Bar-El Tayouri's take on what's new in v2 and how it impacts hashtag#GenAI security.
|
By Mend
Mend.io allows users to import previously generated SBOMs to create a new project within the application. Once imported, licensing and vulnerability data will be associated with your project’s dependencies and will be regularly monitored for updates and new vulnerabilities, similar to any other project in the application.
|
By Mend
Behind every developer is a beloved programming language. In heated debates over which language is the best, the security card will come into play in support of one language or discredit another. We decided to address this debate and put it to the test by researching WhiteSource's comprehensive database. We focused on open source security vulnerabilities in C, Java, JavaScript, Python, Ruby, PHP, and C++, to find out which programming languages are most secure, which vulnerability types (CWEs) are most common in each language, and why.
|
By Mend
We surveyed over 650 developers, and collected data from the NVD, security advisories, peer-reviewed vulnerability databases, issue trackers and more, to gather the latest industry insights in open source vulnerability management.
|
By Mend
Developers across the industry are stepping up to take more responsibility for their code's vulnerability management. In this report we discuss trends in how security is shifting left to the earliest stages of development, putting the power developers in the front seat. We explore the growth of automated tools aimed at helping developers do more with fewer resources and look for answers on what is needed to help close the gap from detection to remediation.
|
By Mend
Software development teams are constantly bombarded with an increasingly high number of security alerts. Unfortunately, there is currently no agreed-upon strategy or a straightforward process for vulnerabilities' prioritization. This results in a lot of valuable development time wated on assessing vulnerabilities, while the critical security issues remain unattended.
- December 2024 (9)
- November 2024 (5)
- October 2024 (8)
- September 2024 (7)
- August 2024 (7)
- July 2024 (6)
- June 2024 (5)
- May 2024 (6)
- April 2024 (5)
- March 2024 (7)
- February 2024 (6)
- January 2024 (4)
- December 2023 (5)
- November 2023 (7)
- October 2023 (9)
- September 2023 (19)
- August 2023 (14)
- July 2023 (13)
- June 2023 (15)
- May 2023 (11)
- April 2023 (10)
- March 2023 (12)
- February 2023 (10)
- January 2023 (14)
- December 2022 (14)
- November 2022 (11)
- October 2022 (16)
- September 2022 (7)
- August 2022 (4)
- July 2022 (4)
- June 2022 (11)
- May 2022 (13)
- April 2022 (9)
- March 2022 (7)
- February 2022 (6)
- January 2022 (9)
- December 2021 (15)
- November 2021 (5)
- October 2021 (5)
- September 2021 (5)
- August 2021 (4)
- July 2021 (4)
- June 2021 (4)
- May 2021 (4)
- April 2021 (7)
- March 2021 (4)
- February 2021 (4)
- January 2021 (3)
- December 2020 (2)
- November 2020 (3)
- October 2020 (5)
- September 2020 (5)
- August 2020 (4)
- July 2020 (7)
- June 2020 (7)
- May 2020 (6)
- April 2020 (16)
- March 2020 (1)
- October 2018 (1)
No component overlooked. Mend identifies every open source component in your software, including dependencies. It then secures you from vulnerabilities and enforces license policies throughout the software development lifecycle. The result? Faster, smoother development without compromising on security.
Not all vulnerabilities are created equal. Mend prioritizes vulnerabilities based on whether your code utilizes them or not, so you know exactly what needs your attention the most. This reduces security alerts by up to 85%, allowing you to remediate more critical issues faster.
Complete Platform:
- Mend Core: We help you keep things in order. Mend is built to streamline your open source governance. With a full layer of alerting, reporting and policy management, you are effortlessly secure and always in control.
- Mend for Developers: Mend for Developers is uniquely designed to simplify developers’ work, while keeping the code secure. Its suite of tools helps speed up integration, find problematic components, and remediate them quickly and easily.
- Mend for Containers: Mend integrates into all stages of the container development lifecycle, including container registries and Kubernetes with automated policy enforcement for maximum visibility and control.
The simplest way to secure and manage open source components in your software.