Vulnerability Assessment: A Guide
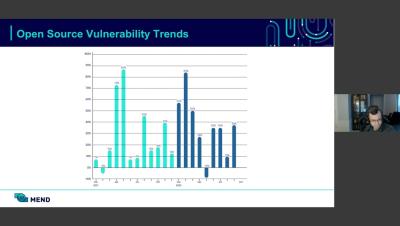
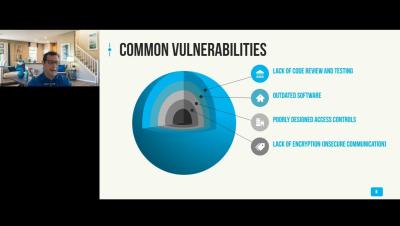
The complexity of technology is ever-increasing and the number of breaches (and the cost of dealing with them) is growing right along with it. Governments are cracking down and turning cybersecurity from nice to have to absolutely mandatory. In response, organizations across industries are taking a more serious look at their security posture and, with that, the need to perform thorough vulnerability assessments.