- December 2024 (1)
- November 2024 (3)
- October 2024 (3)
- September 2024 (7)
- August 2024 (2)
- July 2024 (7)
- June 2024 (9)
- May 2024 (5)
- April 2024 (6)
- March 2024 (7)
- February 2024 (6)
- January 2024 (7)
- December 2023 (8)
- November 2023 (8)
- October 2023 (4)
- September 2023 (9)
- August 2023 (4)
- July 2023 (4)
- June 2023 (7)
- May 2023 (5)
- April 2023 (3)
- March 2023 (5)
- February 2023 (4)
- January 2023 (7)
- December 2022 (3)
- November 2022 (9)
- October 2022 (11)
- September 2022 (9)
- August 2022 (9)
- July 2022 (8)
- June 2022 (3)
- May 2022 (7)
- April 2022 (8)
- March 2022 (7)
- February 2022 (8)
- January 2022 (2)
- December 2021 (11)
- November 2021 (9)
- October 2021 (3)
- September 2021 (7)
- August 2021 (5)
- July 2021 (7)
- June 2021 (20)
- May 2021 (15)
- April 2021 (26)
- March 2021 (13)
- February 2021 (11)
- January 2021 (11)
- December 2020 (19)
- November 2020 (7)
- October 2020 (14)
- September 2020 (13)
- August 2020 (19)
- July 2020 (15)
- June 2020 (7)
- May 2020 (7)
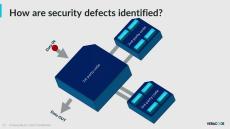
Veracode delivers the application security solutions and services today’s software-driven world requires. Veracode’s unified platform assesses and improves the security of applications from inception through production so that businesses can confidently innovate with the web and mobile applications they build, buy and assemble as well as the components they integrate into their environments.
Veracode’s powerful cloud-based platform, deep security expertise, and systematic, policy-based approach provide enterprises with a simpler and more scalable way to reduce application-layer risk across their global software infrastructures.
The Veracode Solution:
- Overcoming DevSecOps Challenges: Innovating through software holds many promises but also bears risks. AppSec programs often struggle with the same problems:
- Some solutions are hard to manage and scale.
- Developers are not empowered to fix security issues.
- Security teams lack bandwidth to manage DevSecOps programs.
- Delivered Through SaaS: Our SaaS model delivers a better, more scalable service at a lower cost. Because we've analyzed over 10 trillion lines of code, Veracode is able to provide the fastest path to accuracy - without tuning. Our expertise is based on analyzing customer programs for over a decade.
- Application Analysis: Veracode simplifies AppSec programs by combining five application security analysis types in one solution, all integrated into the development pipeline.
- Developer Enablement: Most AppSec programs forget that there is only one team that can fix security findings: the development team. Veracode provides developers with security feedback in their IDE in seconds as they are writing code, helping them learn on the job.
- AppSec Governance: AppSec programs can only be successful if all stakeholders value and support them. That’s why Veracode helps security teams to demonstrate the value of AppSec.
Manage Your Entire Application Security Program in a Single Platform.