Running DeepSeek AI privately using open-source software
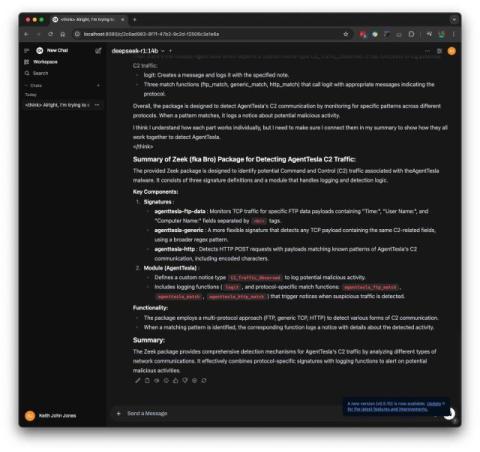
Zeek is a powerful open-source network analysis tool that allows users to monitor traffic and detect malicious activities. Users can write packages to detect cybersecurity events, like this GitHub repo that detects C2 from AgentTesla (a well-known malware family). Automating summarization and documentation using AI is often helpful when analyzing Zeek packages.