Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Compliance
Understanding HIPAA Compliance Requirements for Business Associates
What is a SOC 2 readiness assessment?
A SOC 2 readiness assessment is a final look at your organization’s documents, policies, processes, and vulnerabilities before your formal audit takes place. This is a crucial phase of SOC 2 compliance because your auditor will be using these materials in depth to assess your control environment. A SOC 2 readiness assessment provides answers to questions such as: Before we dive deeper into readiness assessments, here’s a quick primer on SOC 2 audits.
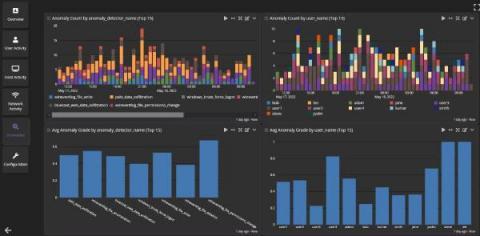
Log Management for Shared Responsibility Model Compliance
Important Trends in Cybersecurity
The cybersecurity industry is an ever-evolving landscape wherein businesses struggle to keep up with the dynamic security and cyber-threat landscape. Due to unprecedented events such as the COVID-19 pandemic, evolving IoT landscape, and the newly evolved techniques of sophisticated cybercrimes, businesses are grappling to deal with the growing cyber threats.
Compliance Guide: Australia & its New Telco Regulation (2022)
Of the many lessons that can be learned from how the Optus data breach was handled, one stands out - Australia’s privacy laws are not equipped to support Aussie data breach victims. To change this, the Australian Government is amending its Telecommunications Regulations 2021 Act. APRA-regulated financial entities can now be involved in efforts to mitigate financial fraud following a data breach.
Brace yourself - ISO27001 changes are coming
If you’re not aware already, then be prepared for change, because a new version of ISO27001 was published in October 2022! It’s all very exciting! The last change to the standard was in 2017. The changes made back then were fundamentally cosmetic, with a few minor tweaks to wording. The changes barely caused a ripple and, even today, organisations are still certified to ISO27001:2013, meaning that no fundamental changes to the standard have taken place for around ten years.
A picture speaks a thousand words
Deep within data lies stories that can help businesses of all shapes and sizes see hidden detail – and act on it. Take a US healthcare provider, for example, who came to us with a pressing issue: the greatest cause of its patient dissatisfaction was due to waiting times. When were the longest peaks? Where was the epicenter of the backlog? And once this was known, what targeted processes could be introduced to speed things up?
Automotive Software - ISO 21434 Compliance Simplified
The modern vehicle comes equipped with a variety of software systems. Especially features that connect it to the outside world, such as online updates, fleet management and communication between vehicles, offer attack surface. The security of automotive software is crucial, not only because bug-induced call-backs are costly, but also because the well-being of passengers depends on it.
Kintent's Frank Kyazze Takes On Data Connectors Dallas, Identifies Industry Frustration with Security Audits
Recently, we caught up with Frank Kyazze, Privacy Director here at Kintent, to chat about his experience at the Data Connectors conference in Dallas last month. Frank had the opportunity to serve on the “Protecting Against Cyber Attacks” discussion panel while in attendance. Frank took part in the panel, discussing how now more than ever, it is imperative for organizations to be vigilant against bad actors.