Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2023
Vendor Risk Assessments: 3 Common Mistakes to Avoid
Few organizations can perform their daily tasks and operations without vendors and third-party partners. And even if they could, successful businesses understand that working with others provides a better experience than doing it alone. The vendors and partners a business associates with matter. These relationships impact security measures, revenue, and brand reputation.
Security SOS: It's dangerous to view cloud and data separately
Security risks within the IT infrastructure of global businesses are increasingly prevalent – and damaging. When swathes of data are separated in the hybrid or multi cloud, it can leave big open doorways for malware to walk right in. The message I want businesses to hear is that cloud and data are not separate. IT only exists to service the needs of a business’ data. Securing cloud services – and therefore your data – is a business-critical issue.
Safeguarding Patients' Personal Health Information: 7 Steps to Achieving HIPAA Compliance with Trustwave DbProtect
The Health Insurance Portability and Accountability Act, best known as HIPAA, is one of the most well-known healthcare privacy laws in the United States. The primary objective of HIPAA is to safeguard patients' Personal Health Information (PHI). HIPAA's Security and Privacy rules establish guidelines for protecting Electronically Protected Health Information (EPHI), and Trustwave DbProtect is a powerful tool to help achieve this goal.
TrustCloud Product Updates: June 2023
Coming soon TrustCloud’s New Platform Experience Get ready for a new and improved homepage that gives you a high-level snapshot of your compliance program, risks, employee compliance, automation status, and audit preparedness—all without toggling between apps. See a sneak peek. Coming soon Ask questions, get answers in TrustCloud Forums We created FlightSchool to help you learn about our products, GRC, and trust. Now, you can join the conversation with FlightSchool Forums!
Is the CMMC 2.0 Rollout on the Horizon?
The Department of Defense (DoD) introduced the Cybersecurity Maturity Model Certification (CMMC) in 2019. This framework outlined a series of security standards contractors must meet to win DoD contracts, so it’s a big concern for many companies. However, four years later, the Cybersecurity Maturity Model Certification rollout has yet to take effect. Part of this delay comes from the fact that the DoD has revamped the CMMC.
NIST Compliance for Enhanced Security
The Value of SOC2 Compliance
ARMO achieves SOC 2 certification: strengthening security and trust
Unleashing the Power of Incident Reporting: Strengthening Security and Compliance
Whether it is reporting a phishing email or something that might be illegal that a coworker is doing, your employees should be a strong last line of defense for security and compliance. According to Gartner, almost 60 percent of all misconduct that is observed in the workplace never gets reported. For decades both compliance officers and security leaders have known that the earlier employees report incidents, the lower the risk. Yet low reporting rates continue to be a problem.
What is the Gramm-Leach-Bliley Act (GLBA)?
The Gramm-Leach Bliley Act (GLBA or GLB Act), or financial modernization act, is a bi-partisan federal regulation passed in 1999 to modernize the financial industry. It repealed vast swathes of the Glass-Steagall Act of 1933 and the Bank Holding Act of 1956, allowing commercial banks to offer financial services such as investments or insurance. It also controls how financial institutions deal with their customer's private information.
Part 2: Preparing the Board of Directors for the SEC's Upcoming Cybersecurity Compliance Regulations
In March 2022, the U.S. Securities and Exchange Commission (SEC) issued a proposed rule, the Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure, that, if adopted, would require companies to disclose their cybersecurity governance capabilities and the role of the board concerning oversight of cyber risk.
How do you choose an MSSP
Businesses in all industries face a constant barrage of threats and attacks. For government contractors (GovCons) handling sensitive information, ensuring robust security measures is paramount. A Managed Security Services Provider (MSSP) can be a valuable partner in safeguarding your organization’s critical assets. In this section, we will explore what an MSSP is, why GovCons need one, how to choose the right MSSP, and the essential questions to ask before hiring one.
What is CMMC?
Defense contractors face increasingly sophisticated cyber threats that can compromise sensitive data and disrupt operations. To combat these risks, the Department of Defense (DoD) has implemented the Cybersecurity Maturity Model Certification (CMMC).
Navy Provides the Source Code For STIG SCA Scanner to Ignyte for fixing the CMMC Market
The licensing partnership with the Navy will allow the Ignyte team to integrate SCAP with the existing open source ecosystem to bring the capability to a broader set of potential customers that serve the military.
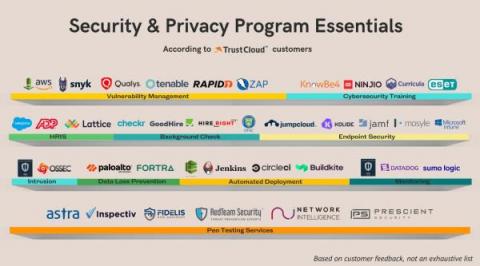
Your Shopping List for Security & Privacy Program Essentials
Whether your org is about to begin its journey for SOC 2, or you’re planning to wrangle up more standards (think ISO 27001, CMMC, and HIPAA, to name a few), the set of tools and software you have in place can be make-or-break. We asked our customers what their recommended tools were, and compiled your shopping list for security and privacy program essentials. Tools or services marked with * denotes a partner or integration.
Preparing for CMMC Compliance: Tips and Best Practices
A Sarbanes-Oxley Act (SOX) IT Compliance Primer
At the turn of the most recent century, the financial world was in a moment of unregulated growth, which lead to some serious corporate misdeeds in the United States. This presented the opportunity for two senators to enact a new law to ensure accurate and reliable financial reporting for public companies in the US. The result was the Sarbanes-Oxley Act (SOX) of 2002. But what does financial reporting have to do with cybersecurity and IT compliance?
Preparing the Board of Directors for the SEC's Upcoming Cybersecurity Compliance Regulations
In March 2022, the U.S. Securities and Exchange Commission (SEC) issued a proposed rule, the Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure, that, if adopted, would require companies to disclose their cybersecurity governance capabilities and the role of the board concerning oversight of cyber risk.
You Just Completed Your ISO 27001 Audit, Now What?
Take it From a Compliance Officer: Secure Networks Matter
Even before the fiasco at Silicon Valley Bank, financial institutions were under tremendous scrutiny from regulators. How could they not be? Banks are among the oldest known targets for theft, and in a digital age, the best way to extract money is going to be either straight cyber-theft from existing accounts or ransomware. IT systems that house customers’ financial data can be architected with the right security controls in place to protect that data to the highest standard.
Our approach to threat modeling
In this series, you’ll hear directly from Vanta’s Security, Enterprise Engineering, and Privacy, Risk, & Compliance Teams to learn about the team’s approach to keeping Vanta — and most importantly, our customers — secure. The following post comes from our Security Team and explains our approach to threat modeling.
The key to 21 CFR Part 11 Compliance
21 CFR Part 11 is a set of regulations issued by the U.S. Food and Drug Administration (FDA) that establishes the criteria under which electronic records and signatures are considered trustworthy, reliable, and equivalent to paper records. In order to sell products in the United States, companies must demonstrate that their systems meet the standards set forth in Part 11. This can be a daunting task, as the requirements are numerous and detailed.
TrustCloud Launches TrustHQ for Atlassian, upgrading Jira to become the central hub for all GRC activities
What to do if your company suffers a data breach
Becoming aware that your company has suffered a data breach can be unsettling. However, due to the nature of cybercriminal activity, it is crucial to react quickly and correctly to contain the incident, minimize any further damages, and protect your business from legal troubles. Data breaches are affecting millions of people across the globe, with over 340 million records already compromised in 2023 headline cases and new incidents surfacing every week.
Improve your risk posture: Introducing Risk Management customization
Today we’re excited to announce Risk Management customization, a collection of new capabilities in our platform that enhance the existing Risk Management solution and give you more flexibility to enable custom risk management scoring and prioritization. Currently in beta, Risk Management customization will be generally available in the coming months.
Why Compliance Monitoring Is Critical for Your Business: Benefits and Best Practices
As regulatory requirements continue to evolve and data breaches become more common, businesses are under increasing pressure to maintain compliance with industry standards. Compliance monitoring is a crucial aspect of this process, enabling organizations to identify and address potential risks before they lead to costly violations or incidents.
The Role of Compliance in Mitigating Identity Theft Risks
In the digital age, identity theft poses a pervasive threat that organizations, regardless of their size or sector, must relentlessly combat. This insidious form of cybercrime involves the malicious exploitation of sensitive and confidential data, carrying grave implications for any organization. The consequences of a single breach can encompass financial losses, irreparable damage to reputation, and the imposition of regulatory penalties.
Keeping Patient Data Secure: How HIPAA Regulations Shape Healthcare Cybersecurity
The definitive guide to compliance with cloud-managed Kubernetes
Introducing Compliance Score: simplifying compliance assessment
Kubernetes compliance under GDPR
Case study: Calico enables HanseMerkur to reduce infrastructure overhead and achieve ISO 27001 compliance
Established in 1875, HanseMerkur is one of the oldest private health insurance companies in Germany, with customers across Europe. The company ran multi-tenant clusters on premises with Kubespray, with around 150 internal software developers as users. As the company must handle personal information and confidential data, it adheres to ISO 27001, the German equivalent of SOC 2, as per industry standards.
Lie Machines - The global fight against misinformation
In this latest podcast in our ‘Beyond Data’ series, Tessa Jones (Calligo’s Chief Data Scientist) and Peter Matson (Data Science Practice Lead) talk with Oxford University’s Professor Philip Howard about the threats posed to democracy by technology, specifically in the shape of Lie Machines.
Centralized Log Management for SOX Compliance
NeoSystems Names Stuart Itkin Senior Vice President And CMO
Understanding FedRAMP System Boundary
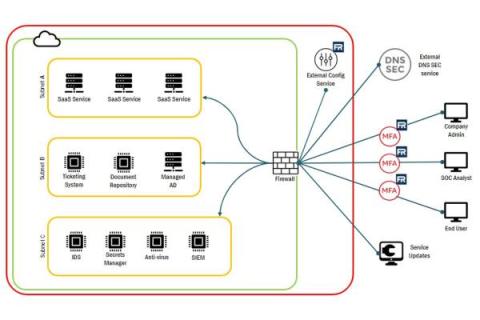
In the ever-changing world of technology, staying secure is a top priority for many organizations. Identifying and documenting system boundaries is essential for keeping data safe and secure, but what does this mean? In this article, we’ll explore FedRAMP System Boundary, how to identify them, and how to generate FedRAMP System Boundary diagrams.
New in Vanta | May 2023
In May we announced Vanta Workspaces for customers with multiple business units, improved navigation bar labels & groupings, 15 new integrations, and more.
The Roadmap to Securing Your Digital Assets with Cybersecurity
“Technology trust is a good thing, but control is a better one.”
Risk Registers: The Ultimate Guide with Examples & Template
Effectively utilizing a risk register allows your organization to anticipate and overcome challenges with confidence. No GRC program is failproof, which is why it’s so critical to take a thorough look at potential risks and remediations. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a better understanding of what it does.
Why Is CMMC a Big Deal?
The Cybersecurity Maturity Model Certification (CMMC) has been around for a few years. And, in its short tenure, it has, itself, matured. The current version of the CMMC is 2.0, released in November 2021. In the latest version of the model, the original five-level model hierarchy was collapsed into three distinct levels: Foundational, Advanced, and Expert.
How to Make the Business Case for ISO 27001 Compliance
As a CIO at a mid-sized company, I faced a new challenge when vendors asked for more specifics about our information security and the protocols we have in place to safeguard our sensitive data. Naturally, those questions were directed toward the IT team (and were phrased in ISO 27001 terminology), which was initially challenging because we had limited knowledge of that particular standard.
How to Achieve ISO 27001: Everything You Need to Know to Pass the Audit
Welcome to our guide on ISO 27001 compliance! We’ll cover everything you need to know about ISO 27001, including its clauses, the preparation & audit processes, costs, and best practices. Let’s get started!
HIPAA and Incident Response: How to Manage Security Incidents in a HIPAA-Compliant Environment.
Webinar How Does NIST 800 171 R3 Impact Your CMMC Plans
TrustCloud Releases World's First Free Security Questionnaire Tool and Compliance Sharing Portal for Startups
Building trust with vendor management
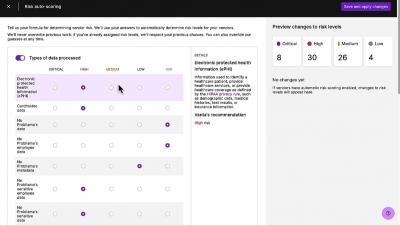
If you’re working towards a stronger security posture to become an organization that’s worthy of customer trust, your vendors are going to play an increasingly important role. In this article, we’ll give you an overview of vendor management and walk through what a robust vendor management process looks like.
A TrustCloud Trustimonial: Icon
Free ISO 27001 Vendor Questionnaire Template (2023 Edition)
Security Questionnaires: The Complete Breakdown for Vendors
New research from SecurityScorecard found that 98% of organizations have at least one vendor that’s had a breach in the last two years. Although this doesn’t necessarily mean affiliated organizations were affected by the breaches, it does emphasize the extensive range of potential exposure to indirect risks. Now more than ever, it’s crucial for vendors to develop a deep understanding of security questionnaires and to implement best practices.
Introducing Vanta's Security and Privacy Training Library
In today’s world, it’s important for your employees to learn about security and privacy best practices not only for their day-to-day roles at your company, but also to help inform the myriad of security and privacy decisions they make in their personal lives every day.