Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
May 2023
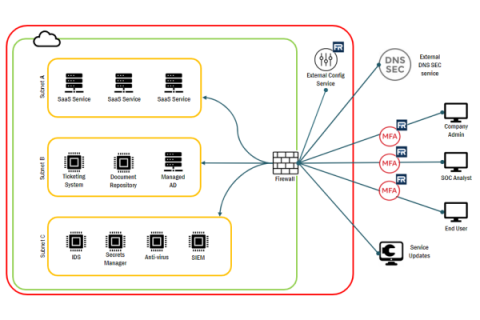
Understanding FedRAMP System Boundaries
In the ever-changing world of technology, staying secure is a top priority for many organizations. Identifying and documenting system boundaries is essential for keeping data safe and secure, but what does this mean? In this article, we’ll explore system boundaries, how to identify them, and how to generate system boundary diagrams. By the end of this guide, you’ll be well-versed in understanding system boundaries and creating diagrams that can help keep your information secure!
TrustCloud Product Updates: May 2023
Our team has been hard at work creating updates and new features just for you, see what we’ve been up to over the last month.
What is DORA? How to prepare your business for compliance
Designed to support the digital resiliency of financial institutions in the EU and UK, the Digital Operational Resilience Act is set to go in effect in January 2025. In this blog, we take a deep dive into what organizations must do in order to be compliant with this new legislation. Digital resiliency is one of the financial sector's most significant challenges today.
What are FedRAMP Requirements? (And Who Needs to Know)
For SaaS applications and cloud service providers (CSPs), maintaining compliance with FedRAMP requirements is critical to the bottom line. It means the difference between working with U.S. government agencies—or not. But as one might expect from a bureaucratic process, getting FedRAMP authorization is complicated and takes time. Before starting the FedRAMP approval process, teams and company leaders must understand the required steps, prepare thoroughly, and muster their patience.
TrustCloud Expands Audit Partner Network, Making it Easier for Companies to Attain Certifications and Win Enterprise Deals
Trust Talks with Rohit Parchuri, CISO at Yext
How SenseOn supports compliance
SenseOn helps organisations improve their security posture and provides the technical capability to meet many of the requirements of common cybersecurity standards. Globally, we have customers who have achieved compliance with ISO 27001, PCI DSS, SOC 2, CIS Top 18, HIPAA, GDPR, and more. This article addresses the most common standards and highlights how SenseOn can help.
Compliance Strategy for Small to mid-Sized Banks and Credit Unions
PCI DSS vs GDPR: A Comparison of Data Security Standards
Since the onset of the pandemic in 2020, global concern for data security and privacy has skyrocketed like a dazzling display of fireworks on New Year’s Eve. With an ever-increasing number of people utilizing online services and sharing their personal information on websites to engage in e-commerce transactions, the infrastructure for collecting and safeguarding consumer data has become of paramount importance.
A TrustCloud Trustimonial: Sevco Security
The Tools You Need to Pass a SOC 2 Audit
Achieving SOC 2 compliance often necessitates the use of specialized tools and software to address specific application and data security measures, but which ones are the best to get the job done? We asked our customers which tools they used and compiled their answers below. Now, let’s break down the tools that have helped our customers achieve compliance excellence, so you can, too. Tools or services marked with * denotes a partner or integration.
Case study: Calico Enterprise empowers Aldagi to achieve EU GDPR compliance
Founded in 1990, Aldagi is Georgia’s first and biggest private insurance firm. With a 32% market share in Georgia’s insurance sector, Aldagi provides a broad range of services to corporate and retail clients. With the onset of the pandemic in 2019, Aldagi wanted to make its services available to customers online. To this end, the company adopted an Agile methodology for software development and re-architected its traditional VM-based applications into cloud-native applications.
Fitting incident management into the SOC 2 puzzle
In today’s business landscape, security and compliance mean everything. Because of this, many modern businesses look towards solutions that will provide customers and prospects with the most confidence and trust. One of these is SOC 2 compliance and attestation. SOC 2 is a marker of solid and consumer-minded companies that want to protect customer data.
What You Should Know About Open Source License Compliance for M&A Activity
Companies are increasingly concerned about the security of applications built on open source components, especially when they’re involved in mergers and acquisitions. Just like copyright for works of art, each piece of open source software has a license that states legally binding conditions for its use.
NeoSystems Announces Executive Leadership Progression
Navigating the complex world of Cybersecurity compliance
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Cyberattacks have become increasingly common, with organizations of all types and sizes being targeted. The consequences of a successful cyberattack can be devastating. As a result, cybersecurity has become a top priority for businesses of all sizes.
Trust Talks with Thomas Owen, CISO at Grafana
Security Journeys: From Change Management to Compliance
Zero Trust seems to no longer command the volume of articles that once set it up as a trend that promised a bright new future for security. This is in part because security is a journey. Rushed implementations and low returns often result in burnout with new technology, and generally the real work happens in the quiet stages when analysts and consultants are putting together the tooling and playbooks that deliver true value and not just a “checkbox outcome.”
Unveiling the Future of AI in Cybersecurity
Welcome to our latest podcast episode, where we delve into the fascinating realm of AI in cybersecurity. Phil Agcaoili, the esteemed entrepreneur, and former CISO professional, joins us in this fascinating discussion. Alongside our hosts, Max Aulakh and Joel Yonts, we unravel the profound impact of artificial intelligence on cybersecurity, compliance, and the workforce.
The Top Compliance Regulations for Financial Institutions
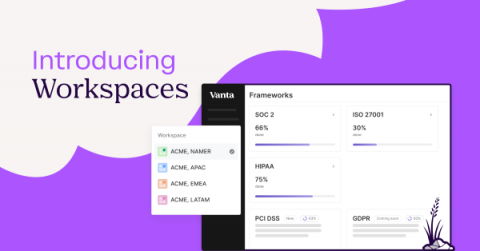
Introducing Vanta Workspaces
We’re thrilled to announce Vanta Workspaces, a new capability in our platform that enables complex organizations with multiple business units to easily customize, manage, and automate compliance at both the business unit and parent organization level in a single Vanta account. With Workspaces, your organization can save time and money, improve your compliance and security posture, and accelerate revenue with the attestations and certifications your end customers require.
How to comply with PCI DSS 4.0 while juggling day-to-day tasks
In our webinar, Insights for Navigating PCI DSS 4.0 Milestones, we discuss some of the challenges organizations face as they try to comprehend the new requirements of PCI DSS 4.0.
Understanding the ISO 27000 Series Changes
PCI DSS Requirement 3 Summary of Changes from Version 3.2.1 to 4.0 Explained
In The Clouds: What Can Risk Management Do for You?
Congrats on your SOC 2 Report! Here's What to Do Next
After tons of hard work, your company has successfully completed a SOC 2 audit and received a well-deserved SOC 2 report! Congratulations! Receiving your SOC 2 attestation is no easy feat, and it’s a significant milestone that demonstrates your company’s commitment to security and trust assurance. If you’re not sure what to do next, no worries – the hard part is done.
FIPS 140-3 Certification and Levels: FIPS 140-2 Vs 140-3
The Federal Information Processing Standard (FIPS) 140-3, is a collection of standards released by the United States government to examine cryptography modules. It explains how to design, develop, and run a cryptography module. The National Institute of Standards and Technology (NIST) and Communications Security Establishment (CSE) created FIPS 140-3 to safeguard critical, unclassified information.
Vanta Expands Partnership with CrowdStrike, Announces New Integration to Secure Access for Automated Compliance
Vanta expands CrowdStrike partnership and announces 3 new investors
At Vanta, we’re on a mission to secure the internet and protect consumer data by transforming the way companies meet their security compliance and establish and deepen trust with their customers, vendors, and partners. Today we’re excited to share several announcements that help us achieve our mission.
How You Can Save Time During a SOC 2 Audit
POV: an important prospect requires all of their partners to get a SOC 2 audit. You’ve just met with your auditing firm and you’ve been tasked with evidence collection, which sounds like tracking down a lot of people and documents. No one can tell you when the RFP knowledge base was last updated. The sales team is asking how long it will take, and can it go faster? You sit back and wonder the same thing: is it possible, and if so, how?
Scans required for PCI DSS compliance
As a risk-based response to the continuous, and varied assaults on our systems by criminals, the PCI DSS standard requires a minimum of 20 technical scans per full year for merchants, and 21 for third-party service providers (TPSPs)
What is FIPS? Detailed Guide on FIPS 140-2
The Federal Information Processing Standard (FIPS) is a collection of rules published by the National Institute of Standards and Technology (NIST) that outlines how to store and handle sensitive data securely. It is a fundamental security precaution that all companies must use to protect Personally Identifiable Information (PII). FIPS defines best practices for data encryption, authentication, and access control.
Keeper: An Essential Zero-Trust and Zero-Knowledge Cybersecurity Platform for the Federal Government
The U.S. federal government tends to move very slowly – except when it comes to zero-trust cybersecurity. The drive to get all agencies to zero trust is cruising along at warp speed, as evidenced by White House Executive Order 14028, CISA’s Zero Trust Maturity Model, OMB OMB M-22-09 and the DoD zero trust strategy and roadmap, all of which were released within the span of less than two years.
How to SOC 2: Everything You Need to Know to Pass the SOC 2 Audit
Welcome to our guide on SOC 2 compliance! We’ll cover everything you need to know about SOC 2, including its key principles, types of reports, the preparation & audit processes, costs, and best practices. Let’s get started!
Get Started with SOC 2 for Vendor Risk Management
SOC 2 reports evaluate internal controls to see how well a company identifies, assesses, mitigates, and monitors risks. In the context of third-party risk management (TPRM), a SOC 2 can give you confidence that your critical vendors are following best practices to protect your data. If you’re getting started with SOC 2 for third-party risk management or need an update, this blog has got you covered.
Trust Talks with Jonathan Price, CISO at Evisort
How to Create an Robust BYOD Policy for Your Organization
Did you know that 70% of organizations have adopted a Bring Your Own Device (BYOD) policy? As technology continues to evolve, more companies are encouraging employees to use their personal devices for work purposes. While this can increase flexibility and productivity, it also poses unique challenges in terms of security and compliance. In this article, we’ll discuss.
Webinar: Six Best Practices to Help with Your Regulatory Compliance Program
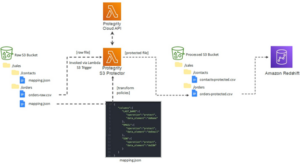
Coast Capital Savings Credit Union: Meeting Canadian Regulatory Standards for Compliance with Protegrity
One of Canada’s largest credit unions, Coast Capital Savings Credit Union (CSS), with over 50 branches across the country, needed to protect critical PII data stored in their AWS cloud environments, Amazon Redshift, AWS EMR, and AWS S3. CSS had to meet Canadian regulatory standards for compliance in 2021, including the Personal Information Electronic Documents Act (PIPEDA), along with a data transformation initiative surrounding its architecture.
Mastering CMMC Compliance with UTMStack: A Comprehensive and Technical Approach
Achieving and maintaining Cybersecurity Maturity Model Certification (CMMC) compliance is a critical requirement for organizations operating within the defense industrial base. As a comprehensive SIEM solution, UTMStack offers advanced features and capabilities that not only streamline the compliance process but also inspire confidence in security and protection.
Introducing Fireblocks Compliance Solutions Suite + Notabene Travel Rule Integration
Today, Fireblocks is launching our new Fireblocks Compliance Solutions Suite to streamline and simplify how our customers meet digital asset regulatory requirements, and stay ahead of industry threats. The new suite enables Fireblocks customers to easily integrate transaction monitoring, wallet screening, and Travel Rule compliance into their existing transaction and compliance workflows and approvals.
Future of Data Privacy Examining the Impact of GDPR and CPRA on Business Practices
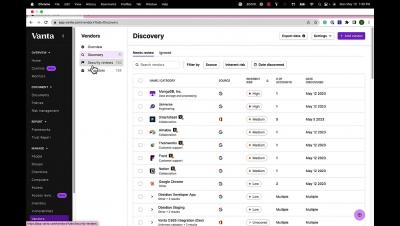
Shine a Light on Shadow IT: Vanta Launches Category-First Vendor Risk Management Solution
New in Vanta | April 2023
We’re excited to announce the newest addition to Vanta’s product portfolio, Vendor Risk Management, as well as improvements to Access Reviews, and more updates from April:
A new way to proactively manage third-party risk: Vendor Risk Management
Businesses are using more SaaS applications than ever, with an average of 110 apps per organization. This proliferation of third-party applications means increasingly more customer and employee data is handled by external vendors. Ensuring your third-party vendors are secure by tracking risk, conducting reviews, and responding to issues is a security best practice and compliance requirement. Unfortunately, this process is often a manual — and expensive — one.
Candid Chats: How to transition to ISO 27001:2022?
Automate the ISO 27001 Compliance Process
In Part I of our two-part blog series, we recapped key drivers for ISO 27001 compliance. Now that you know why companies enthusiastically adopt the ISO 27001 standard to improve cybersecurity protection, we will take a deeper technical dive into Egnyte for ISO 27001.