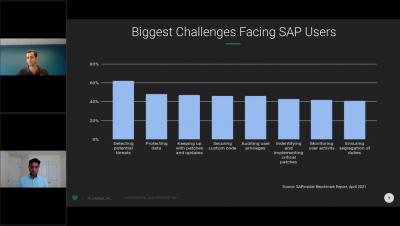
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
November 2021
5 Steps to Become PCI Compliant
Integrating ISO27701 in PIMS to Improve Data Privacy | Privacy Information Management System
How to Make Slack HIPAA Compliant in 2022
As digital transformation continues post-COVID more organizations, including those covered by HIPAA, will seek out SaaS solutions that make collaboration easier. Fortunately more and more applications like Slack are enabling HIPAA compliant use. In early 2019 as Slack filed for its IPO, the company also updated its security page to provide details on its qualifications as a HIPAA compliant messaging app.
How Penetration Testing Helps You Comply with ISO 27001?
ISO27001 is a prominent International Standard and best practice for Information Security Management. The core element of this standard is identifying risks and mitigating vulnerabilities that threaten the security of information assets. So, the technical risk and vulnerability assessment form the basis of implementing the ISO27001 Standard.
What is the CCPA? Definition and Compliance Guidelines for 2021
The California Consumer Privacy Act of 2018 (CCPA) gives Californian consumers greater transparency into how their personal data is being handled. Under the CCPA, California residents have a right to: California's landmark move to greater privacy laws mirrors the consumer data protection posture outlined in the GDPR and Canada's propositions in Bill C-11. Guidance for complying with the CCPA is outlined through CCPA regulations.
What Is Governance, Risk, and Compliance?
Obfuscate user data with Session Replay default privacy settings
Session Replay enables you to replay in a video-like format how users interact with your website to help you understand behavioral patterns and save time troubleshooting. Visibility into user sessions, however, can risk exposing sensitive data and raise privacy concerns. For example, a user session may include typing in a credit card or social security number into an input field.
SOC 2 vs. SOC 3 Compliance: What's the Difference?
Beware the Data Ditch!
More than half of businesses are in the “Data Ditch”. More than half of businesses have started to invest in their Data Maturity and have begun to make smarter, wider use of their data. And by more than 10 metrics of business performance, they are worse off than if they had not bothered. Meanwhile, a third of businesses have come out the other side and have seen dramatic upticks to their performance. and more...
A Definitive List of Different Cloud Compliance Standards
Cloud security is not only good for consumers — but it’s also a requirement for businesses in many industries. Understanding compliance regulations (like GDPR) and security frameworks (like NIST) can help IT teams create strong, layered privacy and security controls and data loss prevention using a range of platforms and integrations. Here are the most common and comprehensive security standards that businesses need to know to be cloud compliant.
Riscosity Overview
ISO 27001 Compliance: What You Need to Know for Your Certification
Looking to become certified to the ISO 27001 standard? In this article you will learn what ISO 27001 is, the key terms and definitions, information security risks you need to consider, and the process for meeting your compliance and certification requirements.
Titania Launches New Module for Organizations Working with U.S. Government Agencies to Meet Cybersecurity Compliance Accurately
CMMC 2.0 Overview: What Changed?
The Cybersecurity Maturity Model Certification (CMMC) is an emerging program created to ensure cyber protection of vulnerable Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) for companies within the Defense Industrial Base (DIB).
LimaCharlie Achieves SOC 2 Certification
LimaCharlie has successfully completed its Service Organization and Control (SOC 2) audit. The audit was conducted by the Johanson Group, a leading professional service firm that focuses on SOC 2 & 3 examinations for public and private companies. The Johanson Group counts Cisco, Symantec and Broadcom among their many clients. They have members on the team that are Certified Information System Auditors (CISA) and are Certified Information Systems Security Personnel (CISSP).
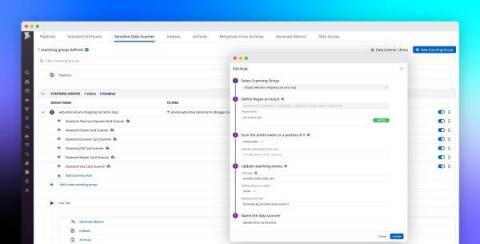
Build a modern data compliance strategy with Datadog's Sensitive Data Scanner
Within distributed applications, data moves across many loosely connected endpoints, microservices, and teams, making it difficult to know when services are storing—or inadvertently leaking—sensitive data. This is especially true for governance, risk management, and compliance (GRC) or other security teams working for enterprises in highly regulated industries, such as healthcare, banking, insurance, and financial services.
What is Compliance Management and Why Is It Important?
Every business has a set of rules and regulations that it must uphold. To maintain compliance, businesses must adhere to the regulations and laws specific to their industry. The problem is, these regulations are constantly changing, and failure to stay up-to-date can lead to serious financial strains and damage to company reputation. Let’s explore how effective compliance management can ensure the continuity and security of your organization.
Selecting the right cybersecurity framework for your organization
Who needs CMMC certification (Resource Guide for 2022)
If your company works with the US Department of Defense (DoD) as a contractor or subcontractor, you will need to prepare to meet CMMC requirements in order to successfully bid on and win contracts. This recent development has been a significant adjustment for small organisations who wish to work with or continue working with the DoD.
What Types of Security Capabilities Do Managed Service Providers (MSP) Offer?
Last time, I discussed the four basic types of managed service providers (MSPs) with which organizations commonly partner. Those categories help to determine the types of services offered by MSPs. In general, MSPs provide five primary services to customers.
What is CMMC? + Useful Resources, Communities & Expert Advice
In this guide, we are covering the facts that you need to know in order to prepare your business to tick off the necessary boxes required to meet CMMC compliance.
Top 12 Cybersecurity Regulations for Financial Services
The proliferation of cyberattacks targeting the financial sector has forced the establishment of several mandatory cybersecurity regulations. Though often considered an unnecessary burden on security teams, regulatory compliance is one of the most effective strategies for keeping financial services accountable for their security posture. Cybersecurity regulations must be malleable to remain relevant in a rapidly evolving threat landscape.