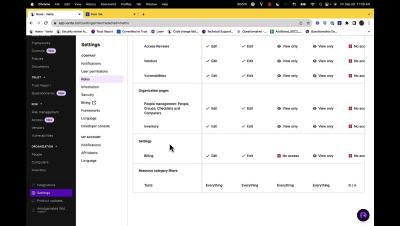
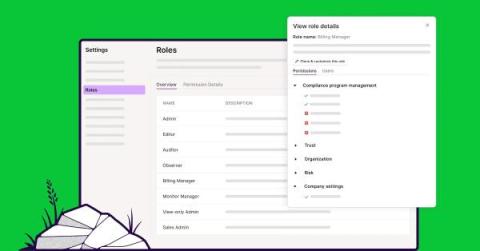
How Riot integrates with Vanta to increase cybersecurity awareness
Many data breaches start with a compromised account from one of a company’s employees. Jérôme Berloty and Benjamin Netter decided to build a product based on that fact and launched Riot in 2020. Based in Paris, France, Riot combines learning modules and phishing simulations to raise cyber awareness and solve compliance needs. The courses are chat-based, five minutes long, and immersive and interactive, making learning more entertaining.