Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2021
Spotlight Sports Group Halves Time Spent on Supplier Management with Rizikon Pro from Crossword Cybersecurity
Empowering women in the field of ethics and compliance
Ethics and compliance is becoming a burgeoning industry as an increase in government regulations in areas such as sustainability, diversity, and data privacy make compliance an important focus for companies. It’s especially important in tech companies as the ever-growing risk of cybersecurity breaches requires that security teams be vigilant in protecting sensitive data.
The Basics of PCI Compliance: Merchant Levels and Requirements
PCI compliance isn’t just good for customers; it’s also good for business. Merchants that fall short of PCI compliance standards not only put their customer data at risk, they also may face hefty fines. The PCI Compliance Guide reports that fines and penalties can range from $5,000 to $100,000 per month for the merchant.
The 3 Types of Security Controls (Categories, Frameworks and Standards)
Security controls can be physical or virtual, policies, training, techniques, methodologies, action plan, devices, and customised solutions to avoid, detect, and prevent intruders and minimise the security risk befalling the individual or organisational proprietary information systems, etc.
Life Sciences Data Management and Compliance
What Is A Compliance Management System?
Regardless of your industry, regulatory compliance is an important component of ongoing success. Staying on top of your compliance obligations can be challenging, and a strong compliance management program will require a compliance management system.
Securing the Supply Chain
A Beginner's Guide to Risk Mitigation and Management for Security and Compliance Professionals
Good data governance can go a long way toward reducing business risk. If your content and your data are secure, you’ve eliminated danger to your customers’ information and secured your proprietary information. From a digital perspective, you’re ahead of the game. But data governance shouldn’t be your only concern.
Cybersecurity Maturity Model Certification (CMMC): Tips for Compliance
Following a string of 83 data breaches in 2019 alone, the United States Department of Defense (DoD) established the Cybersecurity Maturity Model Certification (CMMC). The CMMC framework is a unified national standard for improving cybersecurity. Companies in the defense industrial base (DIB) must implement CMMC requirements in order to win contracts. Read on to find out how you can achieve compliance.
PHI Compliance: What It Is and How To Achieve It
For organizations that work in or partner with the healthcare industry, HIPAA compliance is of paramount importance. Keeping a patient’s medical records and personal information safe isn’t just a matter of avoiding penalties. It’s also key to building trust with patients and, ultimately, providing great patient care. Here’s what health organizations and their partners need to know about PHI and keeping it secure.
Is Zendesk HIPAA Compliant?
As an omni-channel customer service solution, Zendesk allows for companies to meet customers where they are by providing a variety of options for customer support, intake, and management of the overall customer experience (CX) process.
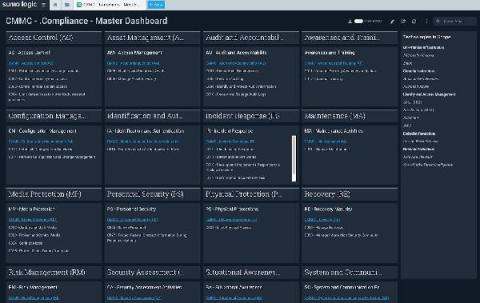
CMMC Compliance Made Easy with Sumo Logic
How to achieve MISRA and AUTOSAR coding compliance
Get practical steps for MISRA and AUTOSAR compliance to improve code quality, safety, and security in automotive software. Recent advancements in the automotive industry include the development of autonomous driving systems, connectivity units, and digital cockpits and infotainment systems that improve the user experience.
Announcing Synopsys as an OpenChain Project third-party certifier
Today, we are proud to announce the expansion of the partnership between Synopsys and the OpenChain project to include third-party certification. The OpenChain Project already recognizes the open source expertise of Synopsys in both the service provider and vendor space. This latest recognition ensures that Synopsys participates in and continuously aligns to the OpenChain Project and ISO/IEC 5230 compliance specification.
Egnyte Expands Content Governance and Compliance Solutions for Google Workspace and Dropbox
If you’re like most companies, your teams rely on a variety of cloud apps and storage solutions to get work done and collaborate with internal and external teams. While this flexibility is great for end users, it creates enormous complexity when it comes to data security and governance. IT teams must juggle multiple administrative dashboards, permissions configurations and access control policies across apps.
Overcoming Compliance Issues in Cloud Computing
The benefits of organizations moving some or all their IT workloads to the cloud are well-known and numerous. There are several challenges to successful cloud adoption, though, and one of the most important of them is compliance. Whether your cloud use case is low-cost data storage, scaling your infrastructure for critical business apps or disaster recovery, this article helps inform you about and overcome compliance issues in cloud computing.