Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
January 2024
Unfolding the Basics of SaaS Defense
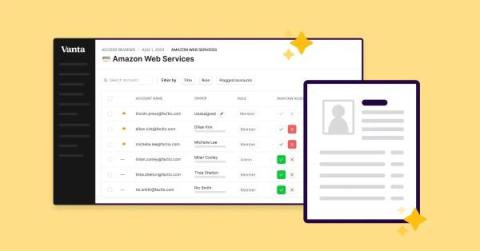
Introducing AI Data Import for Access Reviews
Introducing NIST AI RMF: Monitor and mitigate AI risk
Practitioner's Corner: Turning Regulatory Compliance into Strategic Opportunity
Celebrating new milestones plus enterprise-ready features and more AI capabilities
What Are the Similarities and Differences Between FISMA vs. FedRAMP Certification?
Getting ISO 27001 certification as a SaaS scale up
PCI DSS Requirement 5 - Changes from v3.2.1 to v4.0 Explained
Manual GRC: Why Spreadsheets Are Not the Solution
What Are Compliance Automation Tools?
How to Comply with NIST SP 800-171 Revision 3
Cybersecurity Standards vs Procedures vs Controls vs Policies
Expedite CMMC With Keeper Security
Riscosity Achieves SOC 2 Type II Compliance
Beyond Compliance: Secure Your Business in the Cloud with Falcon Cloud Security
Risk Management Essentials: How to Build A Risk Register
Everything you need to know about the SEC Form 8-K
How to automate your technical vulnerability management with Aikido and Vanta
What is SOC 2 Compliance?
PCI DSS Requirement 4 - Changes from v3.2.1 to v4.0 Explained
Determining Cyber Materiality in a Post-SEC Cyber Rule World
What is a Compliance Risk Assessment?
How Automated Compliance Can Reduce the Cost of Compliance
PCI DSS Requirement 3 - Changes from v3.2.1 to v4.0 Explained
Understanding configuration management with Vanta and AWS
Trust Assurance for Security Teams: A 6 Point Scorecard for Upgrading Your GRC Program
SOX Compliance In Salesforce: What's In Scope And How To Make It Simple
What You Should Know About SOC 2 Compliance
What is IEC/ISA 62443-3-3:2013? Cybersecurity & Compliance
In AI we trust: AI governance best practices from legal and compliance leaders
A Comprehensive Guide on OWASP Top 10 2023 Compliance
Simplified security: The ultimate actionable MASVS compliance checklist for security teams
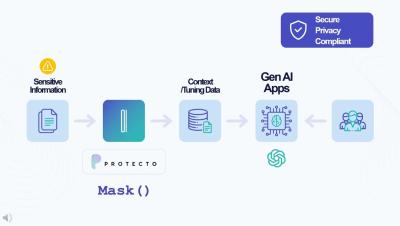
Protecto - Data Protection for Gen AI Applications. Embrace AI confidently!
Enhancing Workplace Security with Attendance Tracking Software
Trustwave Government Solutions Achieves "FedRAMP In Process - PMO Review" Designation
PCI DSS Requirement 2 - Changes from v3.2.1 to v4.0 Explained
In our last discussion, we explored the evolution of Requirement 1 in the transition from PCI DSS v3.2.1 to v4.0, with a particular emphasis on the move towards ‘network security controls’. As we continue our exploration of the updated PCI DSS v4.0, today’s focus will be on the transformations in Requirement 2.
Why you should automate your third-party risk management
The number of tools organizations use is growing everyday. According to Zylo 2023 SaaS Management Index Report, the average organization has 291 SaaS applications in their tech stack — a number which only increases as your organization grows. The more tools that are added to your tech stack, the more third-party risk your business incurs. These risks could result in threats like data theft, service outages, or loss of revenue and customer trust.
Emerging Trends in Wage and Hour Litigation: What You Need to Know
Rubrik Security Cloud-Government is StateRAMP Certified
Tips for Ensuring HIPAA Compliance
How To Get Your Salesforce Org Ready For GDPR Compliance
In a mature Salesforce Org with hundreds of thousands of records, it might be difficult to know where to start on GDPR compliance. In this post, we’ll cover the steps you need to take to get your Salesforce Org GDPR compliant.
3 Ways to Navigate the Challenges of Australian IRAP Assessments
How Financial Services Organizations Can Stay Compliant - Without Sacrificing Security
Cyber Exposure Management Meets the New SEC Reporting Requirements
New in Vanta | January 2024
We closed out 2023 by rolling out more enhancements to the Vanta platform, including Updates to Automated Tests, 8 new integrations, GDPR with EU-US Data Privacy Framework, and more:
The Digital Smile: Virtual Consultations and Teledentistry Services
Compliance Automation and Its Benefits for Reporting
The Security Performance Management Evolution: Interview with Bitsight's Greg Kesen & Dark Reading
How AI is transforming the future of trust
How is generative AI transforming trust? And what does it mean for companies — from startups to enterprises — to be trustworthy in an increasingly AI-driven world?
What is NIST SP 800-53 and 5 Necessary Steps to Comply with It?
The Role of Cybersecurity Assurance Levels in ISO 21434
How to protect your physical infrastructure with AWS and Vanta
This blog is part of a series about how to use Vanta and AWS to simplify your organization’s cloud security. To learn more about how to use Vanta and AWS, watch our Coffee and Compliance on-demand webinar. Amazon Web Services, or AWS, is one of the most popular cloud providers for organizations today — providing one of the most flexible and secure cloud environments available.
Unpacking New SEC Cyber Regulations with Industry Experts
Reviewing the Proposed CMMC Regulations: Key Takeaways and Recommendations
The U.S. Department of Defense (DoD) delivered a timely Christmas gift to government contractors and subcontractors last month – the proposed regulations for the Cybersecurity Maturity Model Certification (CMMC) program. After over two years in development, the proposed rule, released on December 26, 2023, aims to enhance cybersecurity compliance across the defense industrial base.
Choosing the Best Cybersecurity Compliance Software
Cybersecurity Compliance: How to Avoid Costly Mistakes and Stay Protected
TrustCloud Named Security Innovation of the Year (SMB) by the Cloud Awards
PCI DSS Requirement 1 - Changes from v3.2.1 to v4.0 Explained
As we all know, data security is a constantly evolving field, and it’s essential to keep up with the latest standards and requirements. And mark your calendars, because the current PCI DSS v3.2.1 is set to retire on March 31st, 2024. That’s right, the PCI Security Standards Council (SSC) has announced the release of the new and improved PCI DSS v4.0, and compliance with this updated version is mandatory for organizations to maintain data security.
How to use AWS and Vanta for identity and access management
This blog is part of a series about how to use Vanta and AWS to simplify your organization’s cloud security. To learn more about how to use Vanta and AWS, watch our Coffee and Compliance on-demand webinar. Amazon Web Services, or AWS, is one of the most popular cloud providers for organizations today — providing one of the most flexible and secure cloud environments available.
Secure your data with FIPS compliance in Endpoint Central
In today’s fast-paced digital landscape, security is not just a priority; it’s an imperative. We’re excited to announce a significant enhancement to Endpoint Central that will take your data security to a whole new level—Federal Information Processing Standards (FIPS) compliance. In this blog, we’ll explore what FIPS compliance is, why it matters, and how it can benefit your organization.
The CISO's Guide to a Modern GRC Program with Trust Assurance
The position of CISO is not an enviable one. Modern CISOs face enormous challenges like managing the complexity of on-prem and cloud environments, being responsible for the actions of thousands of employees without having authority over them, being perceived as a drag on growth and other resources, and trying to keep up in a compliance and technology landscape that just keeps changing. Oh and budget? Limited and scrutinized.
FAQ: What Is DFARS Compliance and How Does It Work?
The Defense Federal Acquisition Regulation Supplement, better known as DFARS, has significance for contractors working with the Department of Defense (DoD). Our intention is to offer a comprehensive perspective on DFARS in the context of cybersecurity, its various clauses, and the intricacies of maintaining compliance as these rules constantly shift and change over time.
Cracking the DISA STIGs Code: A Comprehensive Guide
We’ve talked a lot about FedRAMP, CMMC, and the typical business/contractor security controls outlined in NIST SP 800-171, but these aren’t the only elements of cybersecurity that the government wants enforced. There are also the DISA STIGS to follow. What are they, do they apply to you, and how can you follow them?
5 Compliance and Governance Happenings That Will Drive Exposure Management in 2024
Navigating Regulatory Standards in Non-Banking Financial Companies
The Most Important Security Metrics to Maintain Compliance: Best Practices for Prioritizing Cyber Resilience
Quantify Cyber Materiality When Navigating APRA's Regulations
Navigating the DoD's Proposed Rule: A Comprehensive Guide to CMMC Compliance Strategies
On December 26, 2023 the Department of Defense (DoD) unveiled the long-anticipated Proposed Rule for the Cybersecurity Maturity Model Certification (CMMC) Program, sending a clear message to defense contractors that CMMC is happening sooner than many thought, and that those taking a “wait and see” attitude can no longer wait to prepare.
What Is XDR, and How Can It Help You Achieve Comprehensive Compliance Requirements?
In the ever-evolving cybersecurity landscape, organizations are constantly striving to enhance their defenses against organized malicious actors. As cyber attacks become more advanced, regulatory bodies have created and enforced compliance requirements to ensure that organizations protect sensitive data and systems. One groundbreaking solution that can help your organization meet these challenges is Extended Detection and Response, known as XDR.
Why you need a consultant to pass ISO 27001
Implementing ISO 27001, the international standard for information security management, is a complex process that requires expertise, experience and careful planning. This blog explores why using a consultant for ISO 27001 implementation is crucial to not just ensure certification, but also (and perhaps more importantly), to build an information security management system that is tailored to your business and its objectives. To make sure your certification is actually working for you.
From automated compliance to AI: How investors are prioritizing security
AI and cybersecurity are top strategic priorities for companies at every scale — from the teams using the tools to increase efficiency all the way up to board leaders who are investing in AI capabilities.