Risk Management: Addressing Shortcomings and Paving the Way Forward
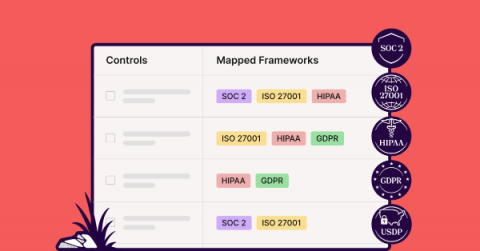
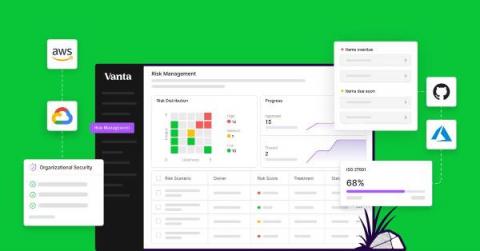
In today’s ever-changing business landscape, managing risk is crucial for the success and longevity of any organization. From financial risks to operational risks and cyber threats, businesses face a range of challenges that require a robust and secure risk strategy. With the complexities of modern business, risk management can no longer be put on the back burner, and companies will need to keep up with the latest practices and solutions to stay afloat.