TrustCloud Product Updates: November 2023
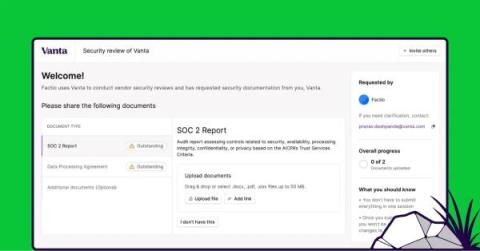
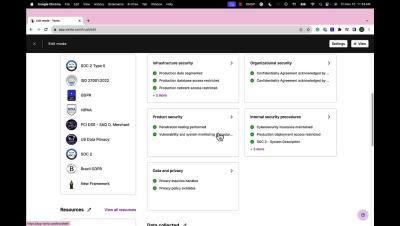
Our team has been hard at work creating updates and new features just for you, see what we’ve been up to over the last month. Free up your workflow with programmatic vendor assessments Now in Beta Release, TrustCloud Third Party Risk Assessments help you verify that your vendors meet your control requirements without bogging down your workflow. Learn more.