Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
Container inspection: walking the security tight rope for cloud DevOps
Containers have become very popular with DevOps as a way to increase speed and agility. However, with recent reports of hackers utilizing vulnerabilities in Docker container images to compromise hosts and launch malicious containers – how can we identify this at the time of development to prevent security costing us later?
Focus on Fixing, Not Just Finding, Vulnerabilities
When investing in an application security (AppSec) program, you expect to see a return on your investment. But in order to recognize a return, your organization needs to determine what success looks like and find a way to measure and prove that the program is meeting your definition of success.
Security Advisory: Critical Zerologon Vulnerability (CVE-2020-1472)
A critical CVSS:10 vulnerability (CVE-2020-1472) in the Microsoft Netlogon process was patched in the August patch cycle, but details were not made public until earlier this week (14th September).
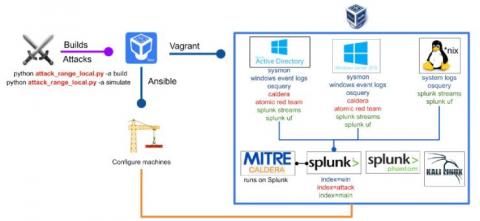
Detecting CVE-2020-1472 (CISA ED 20-04) Using Splunk Attack Range
The recent disclosure of CVE-2020-1472 vulnerability by Microsoft showcases the need for tools that allow defenders to quickly replicate published exploit code, register attack data, and create signatures or other mitigations against released exploits with a high likelihood of exploitation against popular infrastructure or operating systems.
NNT Vulnerability Tracker - Online Demo
MITRE releases 2020 CWE Top 25 most dangerous software weaknesses
Knowing what could hurt you can help you. That’s the point of the nonprofit MITRE’s 2020 Common Weakness Enumeration (CWE) Top 25 Most Dangerous Software Errors (CWE Top 25) list, released a few weeks ago.
Detecting CVE-2020-14386 with Falco and mitigating potential container escapes
On September 14, CVE-2020-14386 was reported as a “high” severity threat. This CVE is a kernel security vulnerability that enables an unprivileged local process to gain root access to the system. CVE-2020-14386 is a result of a bug found in the packet socket facility in the Linux kernel. It allows a bad actor to trigger a memory corruption that can be exploited to hijack data and resources and in the most severe case, completely take over the system.
The History of Common Vulnerabilities and Exposures (CVE)
During the late 1990s, security professionals were using information assurance tools in concert with vulnerability scanners to detect and remove vulnerabilities from the systems for which they are responsible. There’s just one problem – each security vendor has its own database with little to no crossover.
Critical Vulnerabilities in ICS Products Could Enable OT Execution Attacks
Security researchers recently discovered six critical vulnerabilities in third-party code that could expose hundreds of thousands of OT environments to remote code execution attacks. These vulnerabilities were found in Wibu-Systems’ CodeMeter software, a license management platform that is used widely by some of today’s leading industrial control system (ICS) product vendors, include Rockwell Automation and Siemens.