Who Owns PCI Controls? Unpacking ZenGRC in Compliance
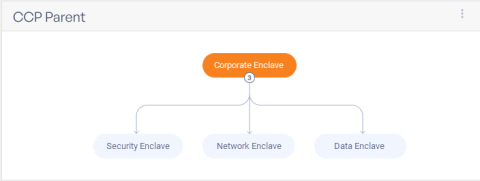
PCI DSS compliance is crucial for any business that processes, stores, or transmits cardholder data. But who exactly is responsible for implementing and enforcing PCI DSS requirements? This blog post will unpack PCI data security standard controls, who owns them, the penalties for non-compliance, and how a Governance, Risk management, and Compliance (GRC) platform like ZenGRC can help streamline compliance.