Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
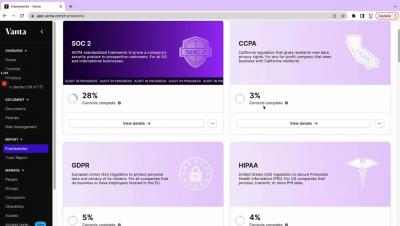
Compliance
[PCI DSS Requirement 2]: Summary of Changes from Version 3.2.1 to 4.0 Explained
Why Healthcare Data is a Primary Target for Cybersecurity Threats?
Over the past several decades, cybercrime has evolved to be more comprehensive, threatening, and damaging. There is an emerging trend of cybercriminals attacking all sorts of individuals and organizations in the industry. The healthcare industry has been a soft target for many years and healthcare data is a prime target for cybercriminals intent on stealing data.
Craft Fireside Chat: Building Trust in a Zero Trust World
App Security & Compliance for SaaS Companies in Saudi Arabian Market
Security Questionnaires Explained: How to Respond to the Most Common Questions
Security questionnaires are a set of questions used to assess the security posture of an organization, usually to determine if one company can trust another and work together. These questions are designed to identify and evaluate potential vulnerabilities, as well as to ensure compliance with industry standards and regulations.
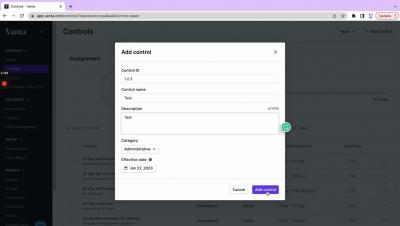
Startups! Here's Your Guide to SOC 2: Audit Preparation
As a startup, it can be challenging to navigate the complex world of compliance. From financial regulations to data privacy laws, there are many different rules and regulations that a new business must adhere to. However, achieving good compliance is essential for the long-term success of any startup. A well-designed compliance program can not only help a startup avoid legal and reputational risks, but it can also improve overall efficiency, productivity, and business growth.
What is continuous security monitoring?
Continuous security monitoring refers to an ongoing monitoring system that keeps a constant watch for security vulnerabilities, the state of your information security controls, and potential risks and threats to your information security. If you think too much about information security, it can seem insurmountable. At any given moment, there could be teams of hackers trying everything in their power to get access to your data.