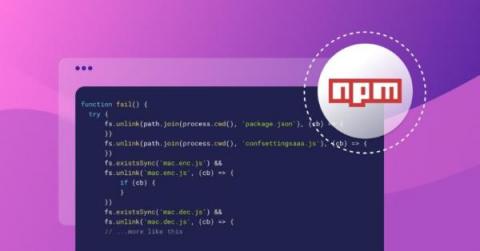
Ignoring vulnerabilities with Snyk
Ignore a vulnerability? That sounds like a paradox. Why would anyone want to ignore a vulnerability? While ignoring security issues should not be your default practice, it is still sometimes necessary. Development and security teams today face vulnerability backlogs consisting of thousands of issues. To maintain rapid development, they must be able to effectively prioritize their work.