Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Application Security
The latest News and Information on Application Security including monitoring, testing, and open source.
Aikido Security achieves ISO 27001:2022 compliance
What Developers Need to Succeed for Effective Application Security
We’ve said it before but it bears repeating: application security isn’t optional anymore. Customers at every level are demanding that the applications they use are secure from the start. Software vendors are well aware of this.
Get More Out of Mend.io with Repository Integrations
Mend.io Customer Success Story - WTW
Best Practices of Highly Effective AppSec Programs
As the pace of application development accelerates, many companies face a growing challenge: how to reinforce security while keeping pace with the schedule of releases.
Unveiling Java Library Vulnerabilities
During a recent customer engagement, we encountered an interesting situation. The customer had raised concerns about a Java XXE (XML External Entity) vulnerability that had left their developers puzzled. Notably, their Static Application Security Testing (SAST) scans consistently identified this as a potential vulnerability.
The Comprehensive Web Application Security Checklist [with15 Best Practices]
Top 6 DevOps Web Application Security Best Practices
In today’s world, the importance of incorporating web application security best practices cannot be overstated. Recent studies show that web applications are the top attack vector in nearly 80% of incidents. The good news is DevOps processes lend themselves to integrated security practices. Here are the top six best practices for seamlessly weaving web application security into DevOps.
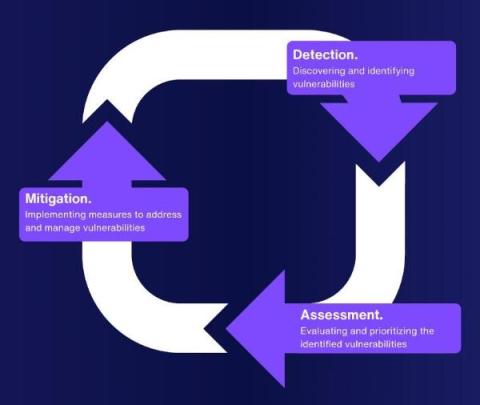
How to Streamline Vulnerability Management
The current cyber world is a veritable minefield, with problems and dangers evolving at a rate that far outstrips the ability of most organizations to respond. More than merely a technical issue, an organization's security posture is determined by the quality of its vulnerability management.