Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2022
Introducing Datadog Application Security Monitoring
Securing modern-day production systems is expensive and complex. Teams often need to implement extensive measures, such as secure coding practices, security testing, periodic vulnerability scans and penetration tests, and protections at the network edge. Even when organizations have the resources to deploy these solutions, they still struggle to keep pace with software teams, especially as they accelerate their release cycles and migrate to distributed systems and microservices.
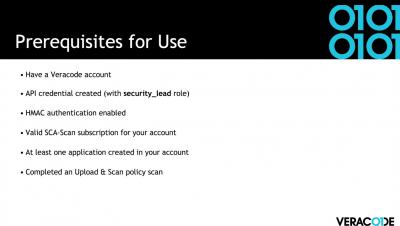
How to generate a Software Bill of Materials (SBOM) using Veracode Software Composition Analysis
How to Generate an SBOM in Veracode SCA
Emerging government regulations have driven the advancement of standards for securing software supply chains. The production of a Software Bill of Materials (SBOM) in a standard format is an increasing audit and compliance need for large organizations.
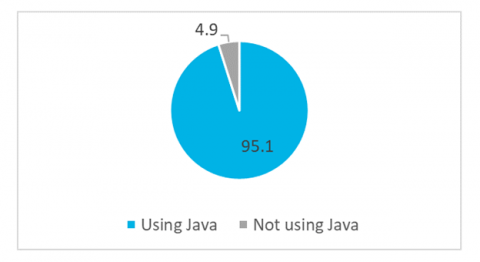
Just Because You Don't Use Log4j or Spring Beans Doesn't Mean Your Application is Unaffected
By now, you’re probably all aware of the recent Log4j and Spring Framework vulnerabilities. As a recap, the Log4j vulnerability – made public on December 10, 2021 – was the result of an exploitable logging feature that, if successfully exploited, could allow attackers to perform an RCE (Remote Code Execution) and compromise the affected server.
CIS Control 16 Application Software Security
The way in which we interact with applications has changed dramatically over years. Enterprises use applications in day-to-day operations to manage their most sensitive data and control access to system resources. Instead of traversing a labyrinth of networks and systems, attackers today see an opening to turn an organizations applications against it to bypass network security controls and compromise sensitive data.
Veracode Acquires ML-Powered Vulnerability Remediation Technology From Jaroona GmbH
On the heels of our significant growth investment from TA Associates, we are pleased to announce our acquisition of auto-remediation technology from Jaroona. Jaroona’s intelligent remediation technology accelerates Veracode’s vision and strategy to automatically detect and remediate software vulnerabilities. Jaroona was recognized as a Gartner Inc. 2021 Cool Vendor for DevSecOps.
What is the maturity level of your AppSec program?
Testing OWASP's Top 10 API Security Vulnerabilities (Part 1)
Application Programming Interface (API) attacks are set to become one of the most prevalent cyberattacks with a broad target range. By nature, APIs expose application logic and sensitive data such as personally identifiable information (PII), causing APIs to become a target for attackers. In 2019, Gartner predicted that API hacks would become the most common form of cyberattacks in 2022. So how can teams stay ahead of API attacks?
CIS Control 16: Application Software Security
Modern IT environments typically include a wide range of applications: software developed in house, hosted software platforms, open-source tools and purchased solutions. Because these applications access sensitive systems, data and other IT assets, cybercriminals are eager to exploit them during attacks. CIS Control 16 offers application software security controls for strengthening your organization’s security posture.
Spring4Shell Vulnerability vs Log4Shell Vulnerability
On March 29, 2022, details of a zero-day vulnerability in Spring Framework (CVE-2022-22965) were leaked. For many, this is reminiscent of the zero-day vulnerability in Log4j (CVE-2021-44228) back in December 2021.