How to Streamline Vulnerability Management
The current cyber world is a veritable minefield, with problems and dangers evolving at a rate that far outstrips the ability of most organizations to respond. More than merely a technical issue, an organization's security posture is determined by the quality of its vulnerability management.
Overview of Vulnerability Management
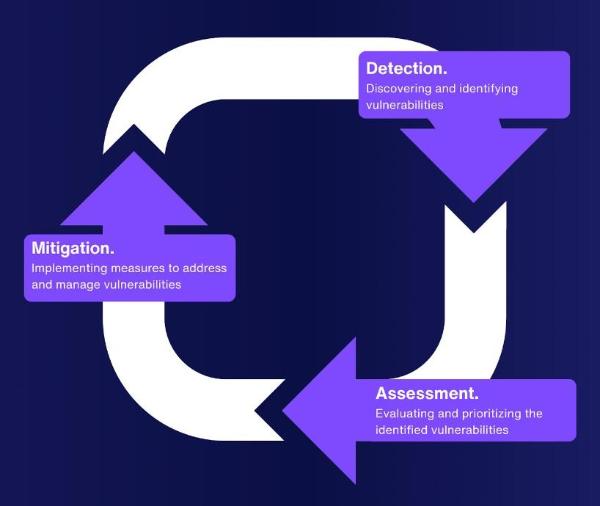
When discussing vulnerabilities, we discuss the chinks in our digital armor. The life cycle of vulnerability management isn't linear, it's cyclical — starting with detection, then assessment, and ending with mitigation, only to loop back to detection.
Understanding vulnerabilities also means understanding the risks associated with them. Not all vulnerabilities are equal. Some pose a minuscule threat, while others can be catastrophic if exploited. Linking each vulnerability to its organizational risk helps shape an appropriate response strategy, ensuring that resources are effectively utilized.
Measuring Success with Metrics and KPIs
Effective vulnerability management is about implementing strategies and ensuring those strategies deliver results. It's where Key Performance Indicators (KPIs) and metrics come into play, offering quantifiable insights into the effectiveness of implemented measures.
Core Metrics to Monitor
Three KPIs which are crucial to the success of your vulnerability management are Time to Remediate, Vulnerability Recurrence Rates, and Fix Success Rate.
“Time-to-Remediate” is pivotal as it provides insights into how quickly vulnerabilities are fixed. A shorter remediation time often correlates with a more efficient system, as it minimizes the window of opportunity for attackers.
Similarly, “Vulnerability-Recurrence-Rates” indicate the robustness of the patches applied. If vulnerabilities recur frequently, the mitigation efforts may only address surface-level symptoms rather than the root cause.
Often-overlooked, the “Fix-Success-Rate” measures the percentage of patches successfully applied versus those attempted. A lower success rate may indicate lack of understanding of vulnerabilities development teams are trying to fix.
Tangible Benefits and Stakeholder Buy-in
Metrics translate the effectiveness of vulnerability management into tangible business benefits.
For instance, consistently low “Time-to-Remediate” and “Vulnerability-Recurrence-Rates” can translate to fewer disruptions in service and higher customer trust. It also gives stakeholders a clear return on investment (ROI) narrative.
Security teams that demonstrate a direct link between improved metrics and business benefits can:
- Secure support and resources
- Further, strengthen vulnerability management
- More easily launch new security initiatives
Organizations that adopt a metrics-driven approach transform vulnerability management from a nebulous concept into a concrete business process with clear benchmarks and objectives. Optimizing the process strengthens the organization's overall security posture in the long run.
Deep Dive into Challenges
The sheer volume of emerging vulnerabilities can be overwhelming, making it difficult and time-consuming to stay updated. Complex IT architectures exacerbate this, including multi-cloud, hybrid systems, and IoT devices.

Regulatory and compliance pressures further complicate the landscape. Regulations like GDPR or CCPA mandate strict data protection measures, and failure to comply due to vulnerabilities can result in severe penalties. Thus, vulnerability management is more than a technical or a legal imperative.
Comprehensive Strategies for Streamlined Vulnerability Management

Enhanced Automation Techniques: Embracing automation can drastically reduce the time taken to identify and fix vulnerabilities. AI-driven tools offer real-time monitoring and can predict potential weak spots in the system. A robust, interconnected defense strategy results when these tools are synced with other security tools.
Risk-Based Approach: Traditional methods of addressing vulnerabilities often use a blanket approach, trying to fix everything. Instead, channel your efforts more effectively by segmenting vulnerabilities based on system importance and potential impact. This means high-risk vulnerabilities are addressed promptly, reducing potential damage.
Ongoing Education: Knowledge is the most potent weapon in the world of cybersecurity. By continually updating your team's knowledge base, you're strengthening your defense capabilities and fostering a culture of vigilance. Workshops, seminars, and hands-on training are invaluable instruments.
Data-Driven Decision-Making: Leveraging data analytics can provide insights into patterns, potential threats, and system health. A vulnerability data lake enriched with machine learning algorithms can predict threat vectors before they emerge, offering a significant strategic advantage.
A Structured and Iterative Approach to Patching: Structured patching, backed by rigorous testing environments like canary releases, ensures patches are rolled out without disruptions. If vulnerabilities remain, automated rollbacks can restore system integrity.
Interdepartmental Collaboration for Holistic Security: A siloed approach is the Achilles heel of many organizations. By encouraging cross-departmental collaboration, one can address vulnerabilities holistically, drawing from diverse expertise and insights.
Tactical Blueprint for Implementing a Streamlined Process
To transition from understanding vulnerabilities to effectively managing them, one needs a strategic blueprint: Audit your existing status, set objectives, allocate resources to your vulnerabilities, and collect feedback to measure progress agilely.

Infrastructure Audit: A thorough, objective audit helps map out existing vulnerabilities, clearly showing the current state. This is where red teams and penetration testers earn their keep, providing invaluable insights.
Objective Setting: Setting clear, measurable goals provides direction. Your goals could be reducing vulnerability detection time or increasing patch efficiency. Benchmarked against industry standards, objectives help maintain competitive parity.
Resource Allocation: This is the engine that drives the entire process. Assigning dedicated teams, allocating budgets, and optimizing these resources is vital. Consider this an investment—the costs of breaches far outweigh the expenditure on robust vulnerability management.
Feedback Loops: A feedback-driven model ensures that the system remains dynamic. Regular feedback can highlight areas of improvement, ensuring that the vulnerability management system remains agile and adaptable.
The Role of Leadership in Creating a Vulnerability-Resistant Culture
While systems and tools are crucial, the human element must be considered. Leadership's role is pivotal in shaping organizational culture. Leaders must understand cybersecurity's business implications, translating this into strategic decisions.
Promoting a culture that prioritizes security, encourages continuous learning, and champions data-driven vulnerability management, ensures an organization-wide alignment towards a common goal — robust cybersecurity.
Comprehensive Toolkit and Resources for Decision Makers
To ensure efficient vulnerability management, decision-makers must arm themselves with a robust toolkit and a comprehensive set of resources. They enable informed decision-making and contribute to a proactive security culture.
Vulnerability Scanners:
These software applications automatically identify vulnerabilities in software, networks, and applications. Leading options include tools like Veracode, Checkmarx, and Invicti.
When selecting a vulnerability scanner:
- Ensure its database is frequently updated.
- Ensure it's compatible with your organization's systems.
- Regularly review and update its configurations to match your organization's evolving infrastructure.
- Once vulnerabilities are detected, run simulated attacks to assess their potential impact. This will offer real-world insights into the criticality of each vulnerability.
Threat Intelligence Platforms
Such platforms gather and analyze information about emerging threats, giving organizations a heads-up on potential future vulnerabilities. Solutions like Mandiant, Recorded Future, ThreatConnect, or AlienVault can be considered.
Tips for optimizing use:
- Integrate the platform with other security tools for real-time updates.
- Allocate personnel to review intelligence and update organizational strategies accordingly regularly.
Patch Management Software
These tools assist in deploying and managing patches across an organization's digital infrastructure. Examples include SolarWinds Patch Manager and ManageEngine Patch Manager Plus.
To maximize efficacy:
- Schedule regular patching intervals.
- Use software that provides reports on patch success rates and failures.
AppSec Security Training Platforms:
Since human error significantly contributes to vulnerabilities, platforms like Secure Flag, Codebashing, Secure Code Warrior or Avatao can train employees to recognize and respond to threats.
Best practices include:
- Regularly updating training content to reflect current threat landscapes.
- Hosting periodic refresher courses for all employees.
- Create and monitor KPIs for security related code quality on a per-developer level.
Security Forums and Communities:
Engaging in forums like Stack Exchange's Information Security community or the Spiceworks security section can be valuable. Here, professionals discuss emerging threats, share experiences, and provide recommendations.
Centralizing Vulnerability Management with Kondukto
Centralizing vulnerability management can simplify what is otherwise a complex process. Using a Vulnerability Management platform like Kondukto may be crucial to realizing the full potential of this strategy.
Simplified Vulnerability Tracking
Instead of logging into multiple tools to assess vulnerabilities, use Kondukto’s Vulnerability Management platform. It fetches vulnerabilities from all your security tools and deduplicates them. Spend less time on manual consolidation and focus more on devising remediation strategies, enabling you to respond to threats quicker.
Optimize DevSecOps Workflow
Utilize Kondukto’s DevOps friendly approach to manage identified vulnerabilities.
Use the Kondukto CLI to integrate all security tests into your CI/CD pipelines and let Kondukto take automated actions like creating tickets in Jira, alerts on Slack or breaking builds in Jenkins based on the rules you configure on the platform.
Role-Based Data Access for Cohesive Collaboration
Define user roles within Kondukto and allocate data access accordingly. This ensures that developers, security engineers, managers and other stakeholders see only what's relevant to them. Tailored data-views prevent information overload, leading to quicker decision-making and streamlined team communication.
Preserve and Build upon Historical Data
Integrate your existing tools with Kondukto as tools evolve or get replaced. Kondukto retains the security insights derived from them.
Benefit: It ensures your team has a historical context, facilitating better-informed future decisions and strategies. This institutional memory can be pivotal in understanding long-term security trends and vulnerabilities.
Conclusion
Vulnerability management is more than a technical endeavor — it's an organizational imperative. As digital threats are omnipresent, having a streamlined and efficient vulnerability management process is non-negotiable. Streamlining vulnerability management translates to saved time and enhanced protection.