Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2023
Enhance corporate application security with AWS Verified Access and Datadog
AWS Verified Access makes it easy and more secure for organizations to grant local or remote access to corporate applications without the use of a VPN. By using Verified Access, you can assign group policies to manage your organizations’ application access and administrative privileges at scale.
AppSec Decoded: Scale application security cost-effectively with Polaris | Synopsys
AppSec Decoded: Don't let your software supply chain poison your apps | Synopsys
AppSec Decoded: Easy deployment with Polaris | Synopsys
AppSec Decoded: Evaluating threats with threat modeling risk analysis | Synopsys
State of Application Security
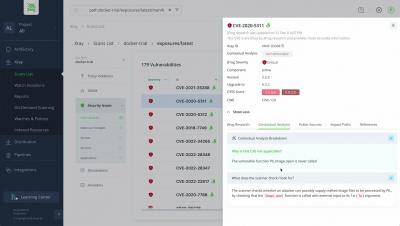
Web application security is an important concern for organizations. Attacks have historically happened at the infrastructure and network level, but today, they increasingly target the business logic exposed by services that handle the most critical and sensitive data. The attack surface of applications is ever increasing, with more than 25,000 vulnerabilities identified in 2022 alone.
Demo Hub launched for Kondukto Technology Partners
For quite a time we have been thinking about ways to make it easier for Kondukto users to try out the integrations of our Technology Partners. At this year’s RSA in San Francisco we are now happy to announce the first release of our Demo Hub. This industry-first feature, integrated right into the Kondukto platform, makes it easier for customers to evaluate and benchmark different solutions from the growing number of Kondukto’s Technology Partners.
How To Get Developer Buy-In For AppSec Programs
Anyone who works on application security knows developers are inseparable from AppSec programs. Even so, the hardest part is figuring out how to get security on their agenda and actively involve them in preventing and managing vulnerabilities. Only with their buy-in and active involvement, it is possible to scale an application security program to the level desired by AppSec teams, especially in large enterprises where developers way outnumber security engineers.
Datadog's Security Observability Day 2023
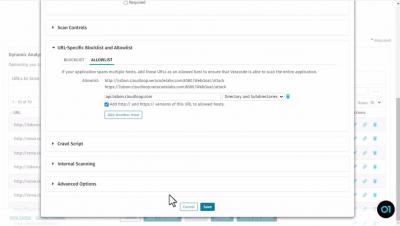
Create and Run an Unauthenticated Dynamic Analysis of a Web Application
Optimizing AppSec by Enhancing Integration with Jira
If there’s one thing we learned in our years of building AppSec technology, it’s that the best tools in the world are useless if they don’t get used. We know from speaking with our customers and industry research that developers won’t use AppSec tools that make their lives harder. Forcing them into cumbersome processes, or making them switch tools and learn a new user interface, will likely lead to AppSec neglect in favor of hitting development deadlines.
AppSec Decoded: Creating a system model in threat modeling | Synopsys
AppSec Decoded: Creating an attack model in threat modeling | Synopsys
Warning: Poor Application Security Health Could Kill You
The Food and Drug Administration (FDA) recently implemented new guidance regarding medical device cybersecurity. It’s not a moment too soon, as new cases arise in which healthcare technology is compromised by vulnerabilities that escalate risks, which could threaten patients’ lives. In a recent survey, over 20% of healthcare organizations said that after a cyberattack, their patient mortality rates had risen, and another 57% reported that cyberattacks led to poorer outcomes for patients.
Why the Need for Application Security Intensifies as EU Tightens Cybersecurity Requirements
Two new sets of regulations introduced by the European Union (EU) indicate that the public sector is taking increased interest in improving cybersecurity and resilience. The EU is introducing the Digital Operational Resilience Act (DORA) for financial institutions and the Cyber Resilience Act (CRA) for software and hardware providers, both designed to enforce software security and secure delivery of services.
See JFrog Advanced Security in Action
Polaris Software Integrity Platform | Synopsys
Snyk brings developer-first AppSec approach to C/C++
Snyk is known for its developer-first application security solutions for many ecosystems like Java, JavaScript, Python, and more. Snyk enables developers to not only find issues but quickly apply fixes, revolutionizing security and supporting its integration at the earliest stages of the SDLC. In 2022, we released the first round of support for C/C++ open source packages, and today we’re excited to announce the Open Beta of C/C++ for Snyk Code and licenses for Snyk Open Source.