Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
November 2022
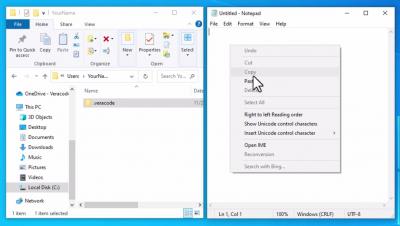
Configure the API Credentials File on Windows
Application Security Management Demo
Datadog Cloud Security Management Demo
Must Know Approaches for Maintaining Mobile Application Security and CIA Traits
Nowadays, every business wants to reach out to a larger audience. And the best way for it is Mobile App Development. Whether someone is at work, at home, or somewhere outside, people frequently go through apps on their mobiles. Such apps collect data, store it and process it to provide reliable results. Indeed, our sensitive and confidential data is also getting into the same process. Hence, it makes a top priority to focus on mobile application security.
Modern Application Security Needs More Than Tech. Don't Neglect Governance
This is the fifth of a six-part blog series that highlights findings from a new Mend white paper, Five Principles of Modern Application Security Programs. Be sure to look out for our upcoming blogs on each of the five principles. While IT and security professionals all generally agree that cyberattacks are on the rise, there remains a great deal of disparity in how they choose to prepare for those attacks.
SAST - All About Static Application Security Testing
Static Application Security Testing (SAST) has been a central part of application security efforts for more than 15 years. Forrester’s State Of Application Security Report, 2022 found that lacking application security remains a leading cause of external security breaches, so it’s safe to say that SAST will be in use for the foreseeable future. Contents hide 1 What Is SAST? 2 Why do we need SAST? 3 What problems does SAST address? 4 How does SAST work?
SAST - All About Static Application Security Testing
Static Application Security Testing (SAST) has been a central part of application security efforts for more than 15 years. Forrester’s State Of Application Security Report, 2022 found that lacking application security remains a leading cause of external security breaches, so it’s safe to say that SAST will be in use for the foreseeable future.
4 Reasons Scan Results May Differ Over Time: Advice from an Application Security Consultant
You didn’t change anything in your code, yet the scan is different this time. Here’s advice from an Application Security Consultant on why that may be. Have you ever wondered why you scan code one day and get one result, and then scan the same code a month later and get different results – even though you never changed anything?
AppSec Decoded: WhiteHat Dynamic
Learn more about Synopsys Software Integrity: https://www.synopsys.com/software-integrity.html
Subscribe: https://www.youtube.com/synopsys
Follow Synopsys on Twitter: https://twitter.com/sw_integrity
Dash Panel Discussion: Foundations of Security and Leadership at Scale
Building a Modern AppSec Program: AWS-Mend Fireside Chat
The modern approach to application security includes strategies and technologies that help development teams prioritize the vulnerabilities they should address and fix. By giving these teams tools that efficiently identify security vulnerabilities that present the biggest risk, they can address them as quickly as possible. Ori Bach, EVP of Product at Mend, and Harry Mower, Director, AWS CodeSuite, got together for a fireside chat to discuss how to implement these strategies.
JavaScript security best practices for securing your applications
Veracode Peer Benchmarking
Scalable SAST and SCA in a single solution with Polaris fAST services
The Power of Manual Penetration Testing in Securing Your Attack Surface
When it comes to protecting software, don’t count on automated testing to find all the vulnerabilities in your code. Here’s why manual penetration testing is more essential (and more accessible) than one might think.
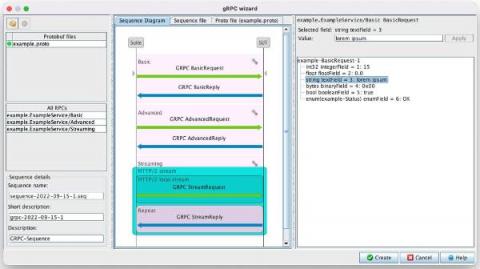
Defensics adds gRPC support for distributed web and mobile application security testing
Modern AppSec Programs Run on Automation
This is the fourth of a six-part blog series that highlights findings from a new Mend white paper, Five Principles of Modern Application Security Programs. Be sure to look out for our upcoming blogs on each of the five principles. With new headlines every day about organizations that have been targeted by cyberattackers, it’s not surprising that 75 percent of organizations assume they’re likely to have a breach in the next three years.
How Government Agencies Can Secure Mission Critical Software in the Cloud
Government agencies are instructed by Executive Order to improve the delivery of digital services to citizens while also safeguarding critical data and systems. Often, this leads to a difficult decision between speed of application production and software security. However, as recent events have shown, sacrificing security in the name of speed compromises the safety of citizens and government infrastructure.
Synopsys Action introduces GitHub Actions integration for developers
What You Need to Know About OpenSSL-3.0.7
OpenSSL released version 3.0.7 with security fixes for High Severity vulnerabilities CVE-2022-3786 & CVE-2022-3602 discussed here. Here's how to know if you're affected and what to do if you are.