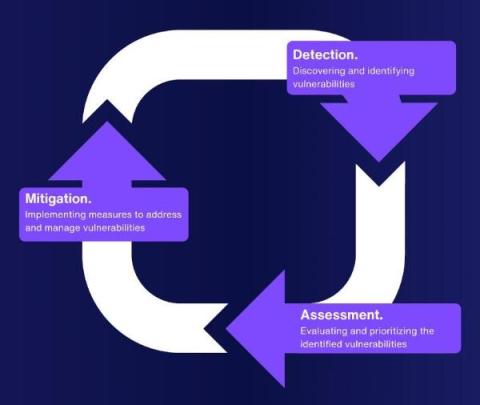
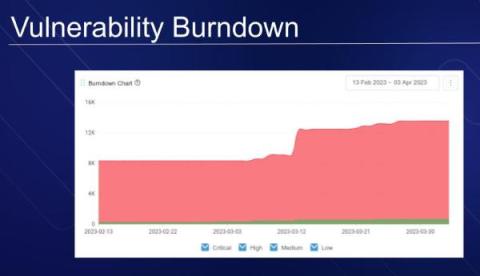
Unveiling Java Library Vulnerabilities
During a recent customer engagement, we encountered an interesting situation. The customer had raised concerns about a Java XXE (XML External Entity) vulnerability that had left their developers puzzled. Notably, their Static Application Security Testing (SAST) scans consistently identified this as a potential vulnerability.