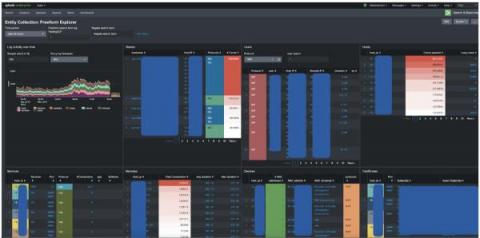
Corelight launches the Entity Collection
Corelight Labs, our amazing research team, has been hard at work on another content collection which we are excited to introduce: the Corelight Entity Collection. Corelight evidence is powerful and comprehensive. So comprehensive, in fact, that it can sometimes be hard to know where to start. Providing customers faster ways to find meaningful context in our data was the driving force behind the creation of the Entity Collection.